MicrosoftHost.exe is a malicious process that the malware creates to disguise itself as a benign process. Users may witness high CPU load coming from this specific process. Despite its name, it is not associated with Microsoft in any way. In this post, I will explain what this process is and how to remove it.
MicrosoftHost.exe Overview
MicrosoftHost.exe is malware masquerading as a Windows system process. Despite the rather convincing name, this process doesn’t belong to Windows system processes. The main purpose of this virus is to utilize your computer’s resources to mine cryptocurrency for attackers. For the user, it only results in a significant load on the system and makes it inoperable.
This process falls into the category of cryptocurrency miner viruses. These programs use computing power to mine Monero or other anonymous currencies. Miners typically do not corrupt user files, which is a slight relief. However, in addition to significantly degrading system performance, MicrosoftHost.exe prevents the installation of anti-malware, which I will discuss next.
Like most similar threats, MicrosoftHost.exe is mostly distributed via applications downloaded from unreliable sources. Users, eager to get free access to paid software, download such files without a drop of doubt, disable system protection during their installation, unaware of the embedded malicious code.
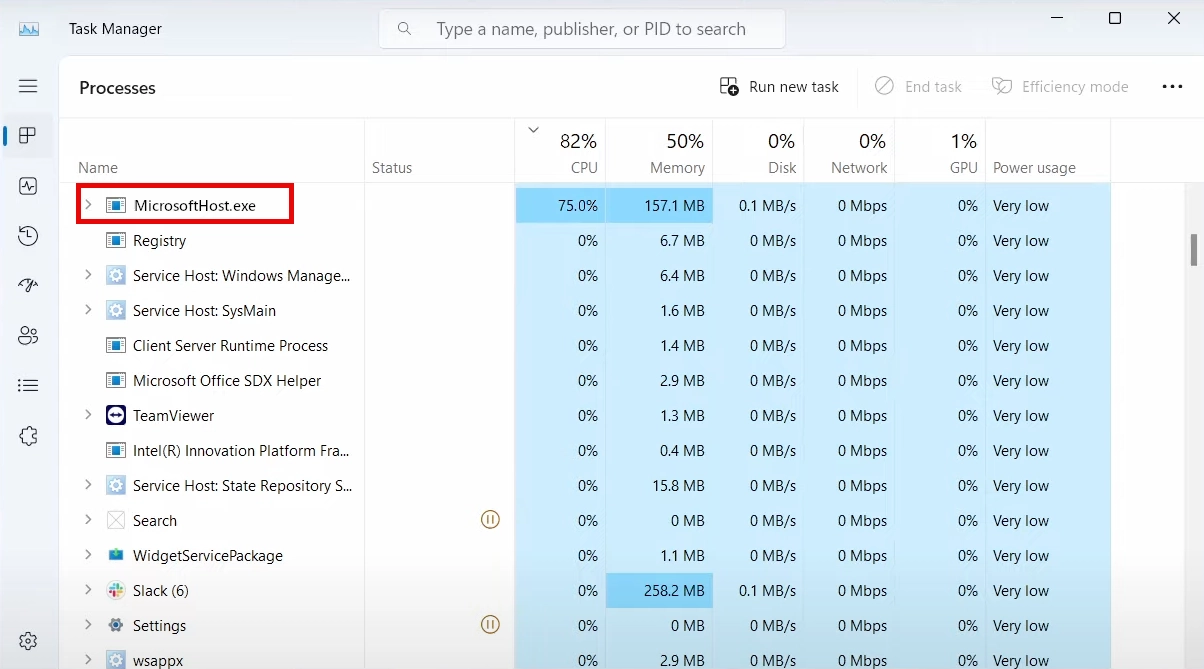
Signs of MicrosoftHost.exe infection are fairly obvious. You may notice CPU constantly running at 80-100% even in idle state, when the system does not have any apps running. Such a continuous load is similar to a stress-test, which means an increased risk of overheating and increased wear of PC parts.
Laptop users may see an increased battery discharge when the machine is infected with this virus. Laptops are also designed with much less continuous loads in mind, meaning that their cooling systems are less capable of handling huge amounts of heat. This may lead to even worse wear and even malfunctions.
Detailed Analysis
To understand what we are dealing with, let’s take a closer look at this miner. MicrosoftHost.exe is an XMRig-based miner that is designed to mine Monero. XMRig is a legit open-source coin miner, which is misused by cybercriminals at a massive scale for illegal purposes.
Once the malicious file is executed, several VBS and batch scripts are run that initiate the installation of the miner and the system setup for it. The customization is done by manipulating the registry using the regedit.exe process.
This is a long process that is repeated several times and I won’t go into too much detail about it, but I will still highlight a few things. At some point, MicrosoftHost.exe disables a selection of antivirus software from being launched through PowerShell commands.
- Malwarebytes
- ByteFence
- 360 Total Security
- SpyHunter
- Enigma
- Avast
- AVG
- Norton
- McAfee
The command that the malware uses does a rather simple trick: it changes the user access permissions for the folder of each antivirus program. As a result, one becomes unable to launch the antivirus program.
/c icacls "C:\Program Files\%antivirus_name%" /deny %username%:(OI)(CI)(F)
After all these preparations, the malware with MicrosoftHost.exe executes the following command:
C:\ProgramData\WindowsTask\MicrosoftHost.exe -o stratum+tcp://loders.xyz:3333 -u CPU --donate-level=1 -k -t1
This command runs the miner itself and gives it specific parameters to follow. Among them are mining pool addresses (loders.xyz) with connection parameters, number of CPU threads to be used in mining and some of the minor internal parameters. All these settings correspond to the “vanilla” XMRig miner.
How To Remove?
The removal process of MicrosoftHost.exe takes several steps, due to the complexity of the infection and changes it does to the system. First, we are going to stop the malware, as it overloads the system and obstructs the normal functioning of antivirus programs. Then, we can switch to deleting the virus
Step 1. Switching to the Safe Mode with Networking
You should begin with rebooting your device in Safe Mode with Networking. To do this, press “Start”, hold the “Shift” key, and select “Restart”. This will send you the Windows Recovery screen, which offers a selection of options.
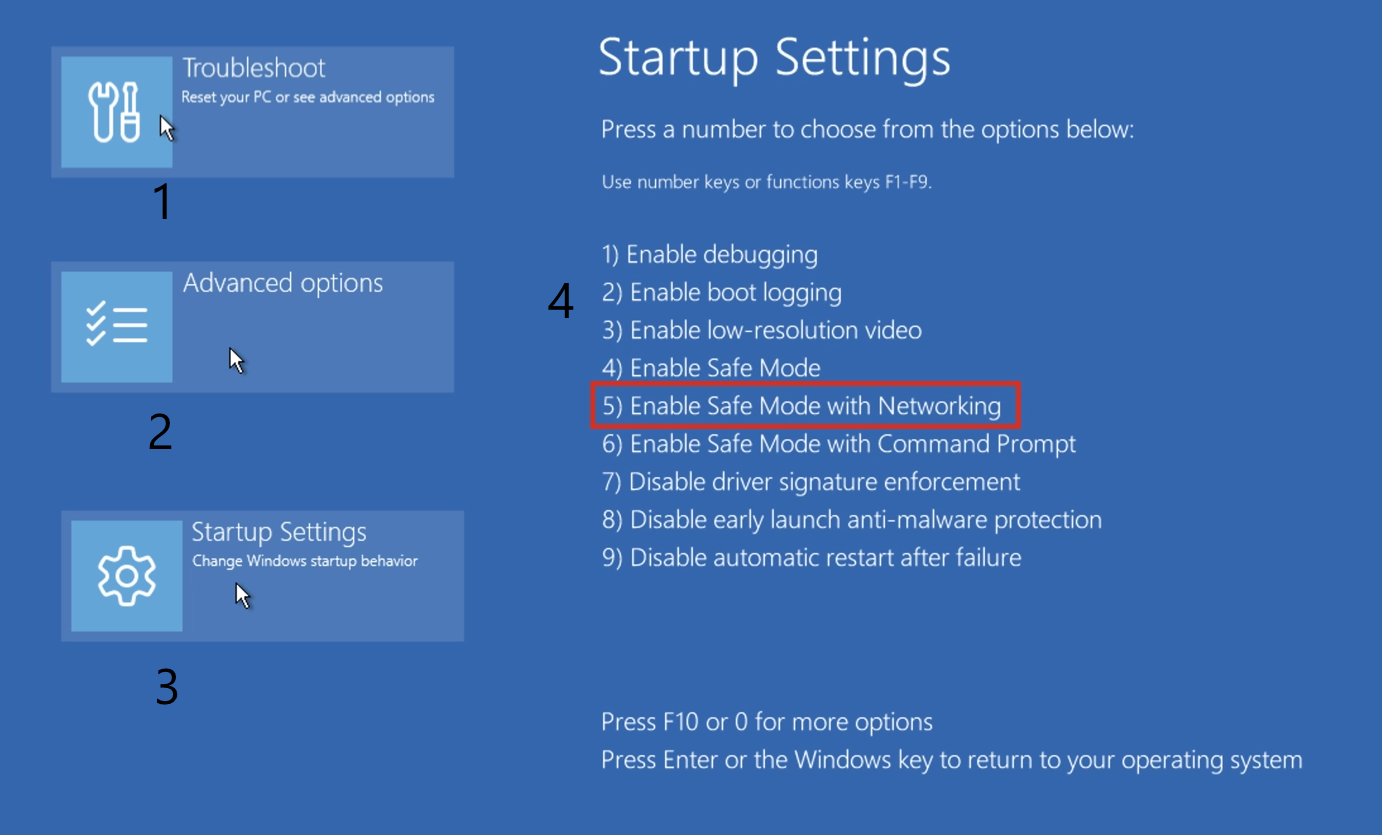
In the menu, go to Advanced Options → Startup Settings, and press the button number that is next to “Enable Safe Mode with Networking” (it may change from one system build to another).
Step 2. Remove the MicrosoftHost.exe Virus
Once in the Safe Mode, you are free from the overhead created by the miner virus. To remove it completely, consider using GridinSoft Anti-Malware: it will detect and remove even the most evasive malicious program, leave alone minor viruses based off of the open-source one. Download it by clicking the banner below and run a Full scan to check even the most remote areas of the system.
Step 3. Revert the Malicious Changes
When the removal is over, you can proceed with undoing the blockages that the malware has created for antiviruses. You will need to find the paths to each folder of the antivirus program, and paste it at the second place.
C:Windows\Windows\system32\icacls “C:\Program Files\%antivirus_name%” /grant Everyone:(OI)(CI)(F)
Run the command for each antivirus you have installed (excluding GridinSoft, as you’ve installed it after the infection). After that, your system will be as good as new.