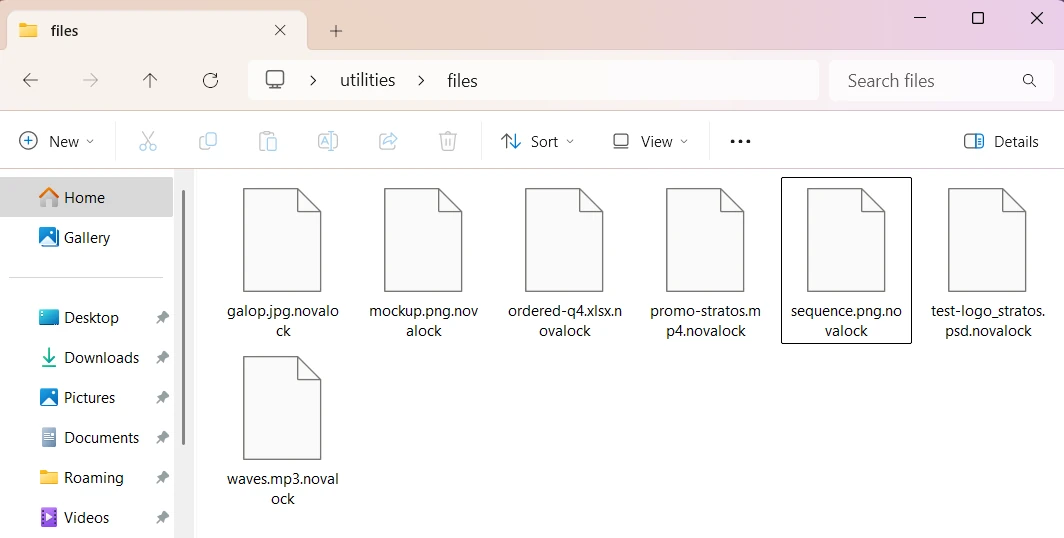
Novalock is a sophisticated form of malware designed to encrypt your files and then demand payment for their release. It belongs to the Globeimposter virus family, and shares a lot of functionality with other samples of the same group. The malware leaves a clear marker: files are appended with a .novalock extension.
This attack is orchestrated by a well-coordinated network of cybercriminals. They create and distribute the ransomware, then collect ransoms from victims. To notify the users about them being attacked, the malware opens a file named “how_to_back_files.html” , which outlines instructions for contacting the attackers and recovering the files.
Ransom Note Breakdown
Ransom note of Novalock virus contains a rather typical manifesto: notification about the system being encrypted, with promises of file decryption after providing ransom payment. Hackers threaten the victims that the files will be impossible to recover shall they stick to a different recovery method rather than their offer.
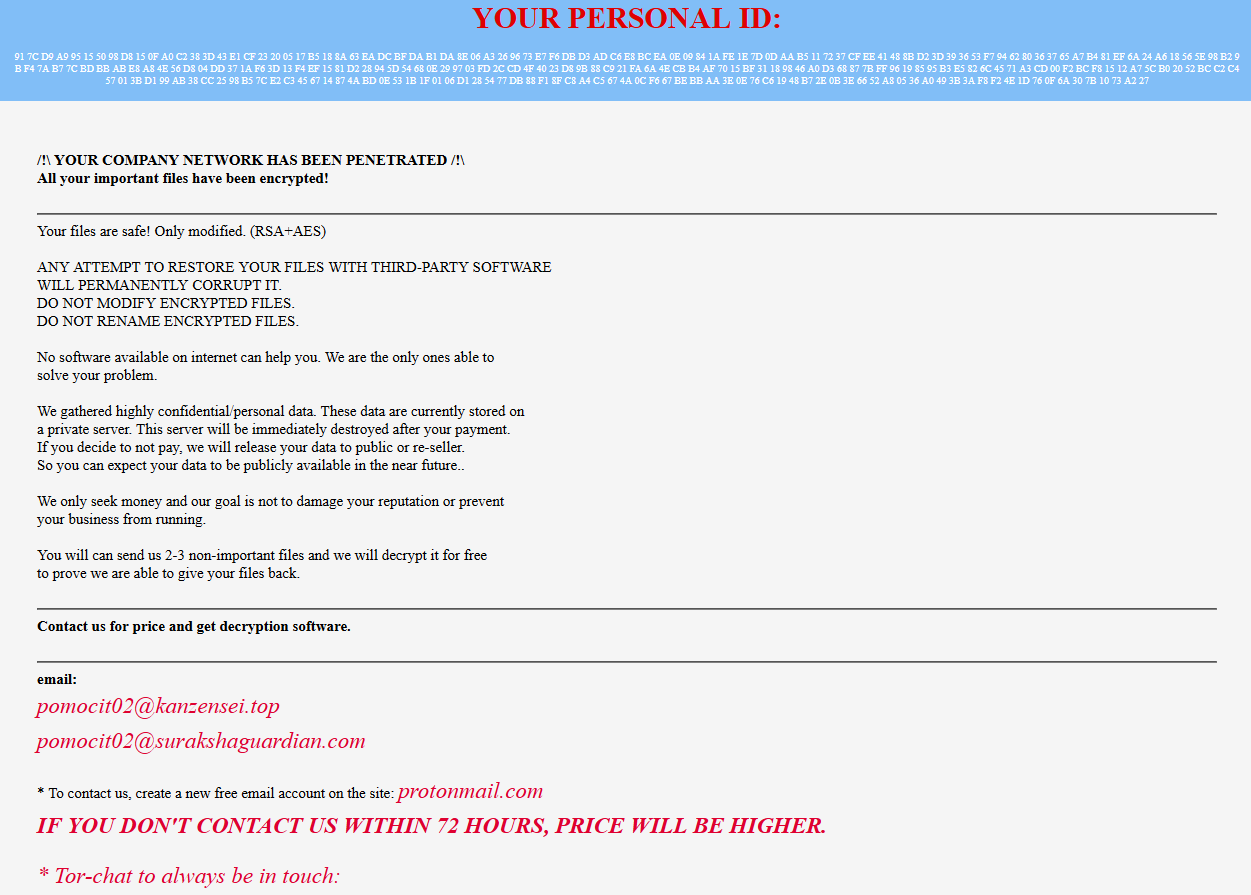
To prove their decryption capabilities, cybercriminals offer the victim to send 2-3 files for them to decrypt for you for free. This trick is widely used by con actors as a way to prove that they really can get your files back.
To arrange all the negotiations, fraudsters provide a Tor website and 2 email addresses – [email protected] and [email protected]. Both the website and email addresses are used by other Globeimposter ransomware samples, meaning that hackers re-use their infrastructure over and over again.
While paying might seem like the quickest solution, I strongly urge against paying the ransom. Funding these cybercriminals motivates their further activities, putting more systems at risk. Furthermore, there’s no guarantee you’ll regain access to your files after payment – hackers may easily take the money and ignore their promises, or ask for even more money.
What Is the Novalock Virus?
Novalock is a ransomware-type malware that encrypts files on infected systems, rendering them inaccessible. It employs robust encryption algorithms, making brute-force decryption virtually impossible. However, this doesn’t mean recovering your files is out of reach.
Before encrypting your data, Novalock tampers with critical system settings, particularly those related to security and file protection. This enables it to bypass built-in defenses and stay undetected for Microsoft Defender, the built-in antivirus.
Even after encryption, the ransomware continues running in the background. This poses an ongoing threat, as newly created or restored files can also be encrypted. A lot of users proceed with file recovery ignoring the malware removal, and get their files ciphered, again. To avoid further damage, it’s vital to remove the malware before attempting file recovery.
Steps to Remove Novalock Ransomware
To safely remove Novalock, I recommend using GridinSoft Anti-Malware. This tool is adept at detecting and eliminating malicious files, regardless of any changes made to your system. Download the program by clicking the banner below, perform a Full scan, and click the “Clean Now” button after the scan to wipe out all the malicious elements.
Recovering Encrypted .novalock Files: Is It Possible?
Unfortunately, no publicly available decryption tool exists for .novalock files at this time. Be wary of anyone claiming otherwise; such offers are often scams or ploys by the ransomware operators to extract additional money.
What you may and should trust is the free recovery ways offered by anti-ransomware agencies. Their help may come in several different forms – from getting the decryption keys directly from hackers to breaking down the encryption mechanism.
- Law enforcement interventions. Arresting key players in ransomware groups often leads to the recovery of decryption keys, which are then shared with victims on demand. We made a post before about exactly this situation happening to LockBit ransomware gang.
- Encryption string flaw. Cybersecurity researchers may discover vulnerabilities in the encryption algorithms, enabling the creation of a free decryptor. Keep an eye on news releases on our website – we will notify as soon as any ability shows up.
Aside from relying on decryption, one may try out the options that circumvent decrypting the files. Among them, using file recovery tools is one of the most prominent. Some ransomware leaves traces that file recovery utilities can exploit. While success isn’t guaranteed, it’s worth trying a reputable recovery tool that supports a wide range of file formats. Our colleagues from HowToFix Guide made a detailed guide for one of such programs – PhotoRec.
One more opportunity is present for people who send their files over the Internet, or keep online backups. Search for unencrypted versions of your files in cloud storage, emails, or other repositories. Even an outdated version can be a lifesaver, especially if you’ve made the backup not so long ago. And overall, it is better to have at least an older version of the file or project than to have none at all.