BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) solutions have two vulnerabilities, identified as CVE-2024-12356 and CVE-2024-12686. These vulnerabilities enable unauthenticated command injection and privilege escalation. This means attackers can execute arbitrary commands and gain full control over enterprise systems.
BeyondTrust Critical Flaw Actively Exploited, CISA Warns
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified a significant security vulnerability in BeyondTrust’s Privileged Remote Access and Remote Support software. The flaw, tracked as CVE-2024-12356, has been added to CISA’s Known Exploited Vulnerabilities catalog due to evidence of its active exploitation.
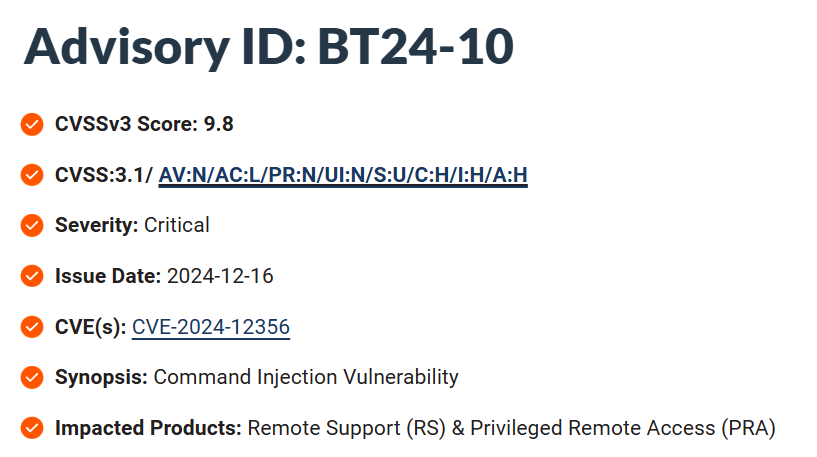
CVE-2024-12356 is a critical command injection vulnerability affecting BeyondTrust’s Privileged Remote Access and Remote Support software. This flaw has been assigned a CVSS score of 9.8, categorizing it as critical.
Commands are executed with the permissions of the “site user”, meaning the attacker does not require valid credentials. This vulnerability arises from the software’s failure to properly validate user input before executing it in system-level commands or scripts.
Affected Software and Fixes
This vulnerability affects PRA and RS software versions 24.3.1 and earlier. Although BeyondTrust has secured its cloud-hosted instances, self-hosted users must apply the following patches to mitigate the issue: Privileged Remote Access BT24-10-ONPREM1 or BT24-10-ONPREM2, and Remote Support BT24-10-ONPREM1 or BT24-10-ONPREM2.
Earlier this month, BeyondTrust revealed a cyberattack targeting its Remote Support SaaS platform. Attackers exploited a compromised Remote Support SaaS API key to reset passwords for local application accounts.
Additional Vulnerability Discovered
During its investigation, BeyondTrust identified another vulnerability, CVE-2024-12686 (CVSS score: 6.6). This medium-severity issue also enables command injection but unlike CVE-2024-12356, requires an attacker to have existing administrative privileges. Fixes for this vulnerability depend on the specific PRA or RS version and include patches BT24-11-ONPREM1 through BT24-11-ONPREM7.
BeyondTrust has not observed active exploitation of the medium-severity vulnerability and has informed all affected customers. The company has engaged a third-party cybersecurity firm to assist with its investigation, but details about the scale of the attack or the identity of the threat actors remain unknown. Organizations using BeyondTrust’s PRA or RS software should immediately review their deployment and apply the necessary patches to prevent exploitation.
As for individual users, it’s reasonable to consider using an additional anti-malware solution for enhanced security. For instance, GridinSoft Anti-Malware can offer an extra layer of protection and help prevent unwanted activity.