Researchers have demonstrated an exploit targeting the speculative execution vulnerability in the Indirect Branch Predictor Barrier (IBPB). Although the flaw, known as Spectre Flaw, is known for quite some time now, modern CPUs from both AMD and Intel are susceptible to it, with it potentially leading to data leaks.
Spectre Flaw Still Haunts Intel and AMD Chips, Putting Security at Risk
Researchers at ETH Zürich, Johannes Wikner and Kaveh Razavi have discovered that the Spectre vulnerability, which first made headlines more than six years ago, still affects the latest Intel and AMD processors. The vulnerabilities in question are CVE-2017-5715 for Intel and CVE-2022-23824 for AMD, in speculative execution protection, specifically the Indirect Branch Predictor Barrier (IBPB).
In a nutshell, this defense mechanism was initially introduced to mitigate Spectre v2 attacks. However, the new results show that attackers can still bypass this barrier, which can lead to the leakage of sensitive information. This information could include hashed passwords from processes with elevated privileges.
Despite the extensive protection measures taken by major x86 CPU manufacturers after Spectre was discovered, a microcode bug in Intel’s latest architectures — Golden Cove and Raptor Cove — retain branch predictions that should have been invalidated by IBPB. This flaw allows for a practical cross-process Spectre attack, enabling attackers to exploit the very defenses meant to protect sensitive data.
It is worth remembering that there were other vulnerabilities, that touch both AMD and Intel CPUs. We have a separate article describing a pack of AMD flaws and Intel Reptar vulnerability – give them a check. Apple Silicon chips are not completely free of bugs either, with GoFetch vulnerability potentially compromising CPU cryptography and exposing personal data.
Technical Details
Spectre utilizes a speculative execution feature in modern processors that allows them to preemptively execute instructions based on predicted paths. I.e., the processor does not execute instructions in order, but rather tries to guess the next action. and consequently pre-loads the data needed for this action.
If the speculatively predicted value is correct, this greatly speeds up the task. However, if the prediction is incorrect, the speculative instructions are discarded before the processor continues the task with the correct value.
This was originally intended to improve performance, but researchers have demonstrated how attackers can access restricted memory areas and sensitive data. Fortunately, successful exploitation requires specific conditions that are challenging to meet.
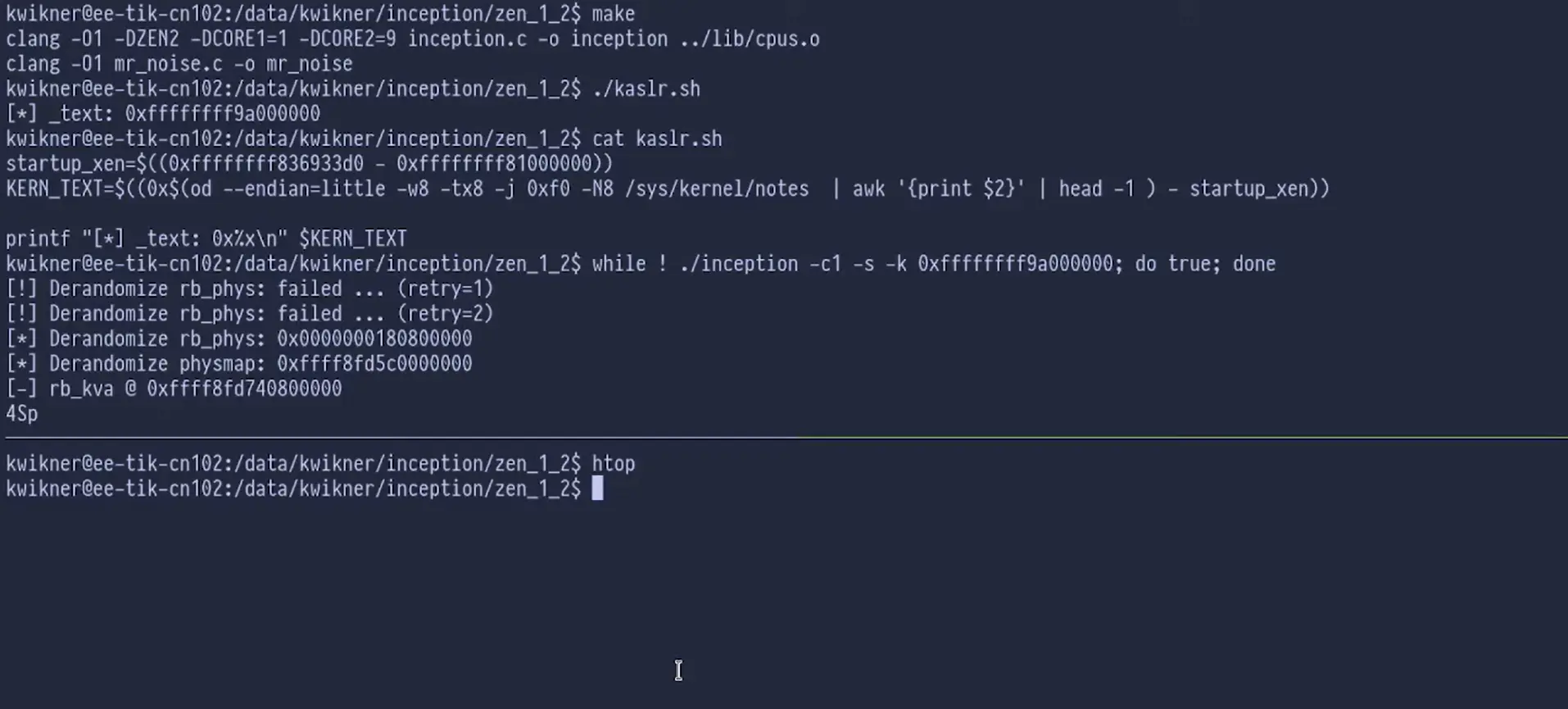
First, the attacker must be able to execute code on the same machine as the target application. Second, the attacker needs information about the target memory addresses. The experts conducted all of their experiments on Linux. This is because they lacked access to source code from other major OS vendors.
Intel
As for Intel processors, an attacker must execute malware alongside the target application. The code triggers speculative execution that accesses sensitive memory areas. A microcode bug allows branch predictions retained after IBPB to leak sensitive information, including the root password hash from SUID processes.
AMD
What about AMD processors, the exploit procedure is similar to the Intel scheme, with the attacker needing to execute code within an unprivileged process alongside a privileged process. The IBPB implementation in AMD processors can be bypassed, allowing attackers to use branching predictions to access sensitive kernel memory.
Notably, on AMD processors, it has been found that the frequency and stability of attacks correlate with system temperature, linked to the RowHammer phenomenon. Experts have found that this effect is particularly sensitive to temperature changes. Thus it is amplified when the temperature rises, which raises the probability of branch prediction errors, potentially increasing the chances of CPU and RAM getting into exploitable state. Higher temperature also leads to an increase in the number of “bit errors” in DRAM cells.
Delayed Patches and Incomplete Fixes
Despite these vulnerabilities being six years old, they still affect 12th, 13th, and 14th generation Intel Core processors, along with 5th and 6th generation Xeon processors. In “red” lineup, Zen 1(+) and Zen 2 processors remain vulnerable.
Intel released a microcode patch in March 2024 to fix the issue, but not all hardware has yet received the update. AMD fixed the issue earlier, in November 2022, by releasing a security advisory.
However, addressing these vulnerabilities requires more than simply applying updates. Intel users need to ensure their microcode is up-to-date and apply updates if necessary. Patch availability varies by system, with particular inconsistencies noted on Linux distributions like Ubuntu.
AMD users should install the required kernel updates. AMD has noted that operating system vendors and hypervisor developers need to take additional steps to fully mitigate these risks.