A critical vulnerability has been discovered in the GiveWP WordPress plugin that leaves thousands of websites exposed. The vulnerability is of a high severity and allows for controlling the entire affected website without any authentication. A fix is currently available to address this vulnerability, so users should update as soon as possible.
Critical RCE vulnerability affects thousands of WordPress sites
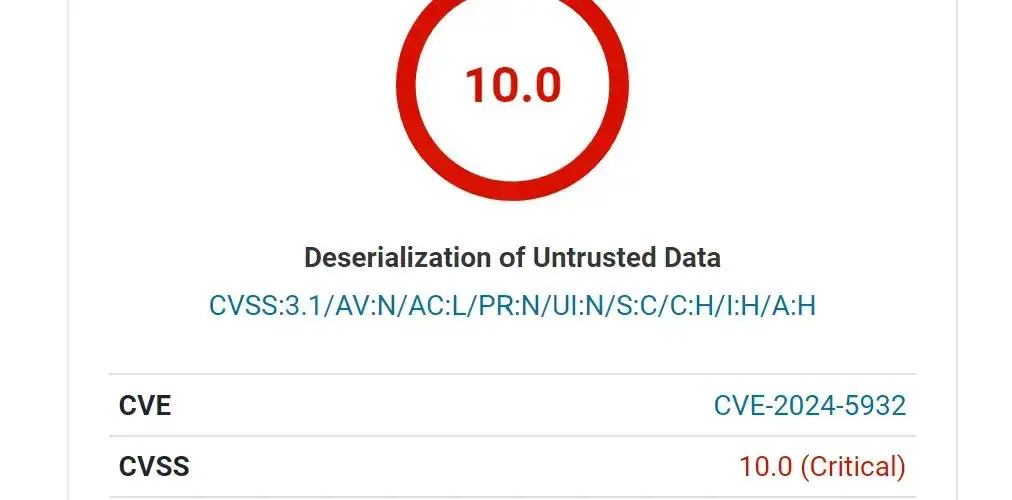
A cybersecurity researcher has recently discovered a critical vulnerability called CVE-2024-5932. It has a CVSS score of 10.0 (max possible), and seriously compromises more than 100,000 WordPress sites using the GiveWP plugin version 3.14.1 and earlier. The issue involves a PHP Object Injection (POI) vulnerability in the GiveWP plugin, widely used by donation and fundraising platforms. The vulnerability is exploited by deserialization of untrusted data, in particular through the ‘give_title’ parameter. Attackers can inject a maliciously crafted PHP object. When combined with an existing object-oriented programming (OOP) chain in the plugin, this leads to full remote code execution (RCE).
In addition to remote code execution (RCE), this vulnerability allows for unauthorized file deletion without any authentication. In practice, this may allow attackers to gain full control over the affected WordPress site by deleting critical files from the server. Given the role of the plugin in managing financial transactions and sensitive donor information, the consequences of such an exploit are exceptionally serious.
Detection And Response
A security researcher nicknamed villu164 discovered the vulnerability on May 26, 2024, and reported it through the Wordfence Bug Bounty Program. On June 13, 2024, Wordfence notified the plugin developer of the vulnerability, but they did not receive any feedback. On July 6, 2024, the company informed the WordPress.org team. A month later, on August 7, 2024, the developer released a fully patched version 3.14.2. Fortunately, there are currently no reports or evidence that the vulnerability has been exploited in the wild. But as it usually happens, the exploitation will inevitably follow the public disclosure of the flaw.
As the plugin is described on the official website, GiveWP is the highest-rated, most downloaded, and best-supported donation plugin for WordPress. With GiveWP, users accept gifts for charity or other purposes through customizable donation forms. The donation plugin also allows you to view donor data and fundraising reports, manage donors, and integrate with various third-party gateways and services. In other words, the site interacts with finance and the people involved. It’s no surprise that it scored 10/10 on the CVSS scale – both the ease of exploitation and the amount of data it can expose are nothing to mess around with.
Recommendations
To protect their WordPress site, site masters should update the plugin to 3.14.2. Since there is no workaround available, websites running older versions remain highly vulnerable to exploitation, especially now that the vulnerability has been made public.
Still, a proactive approach towards picking plugins is a must. Even the well-known apps may be vulnerable, leave alone no-name plugins that were posted 2 years ago and never updated since. Tricks like typosquatting or supply chain attacks are applicable here as well, so stay updated on the latest WP security news.




