In June of this year, a new wave of cyber-attacks and extortion operations, organized by the criminal group 8Base, swept the world. Hackers use a double extortion method: they infect victims’ computers with a ransomware virus that blocks access to data, and then demand a ransom for their restoration. If the victim refuses to pay, the hackers threaten to publish the stolen information on their dark web leak site.
A new rising threat
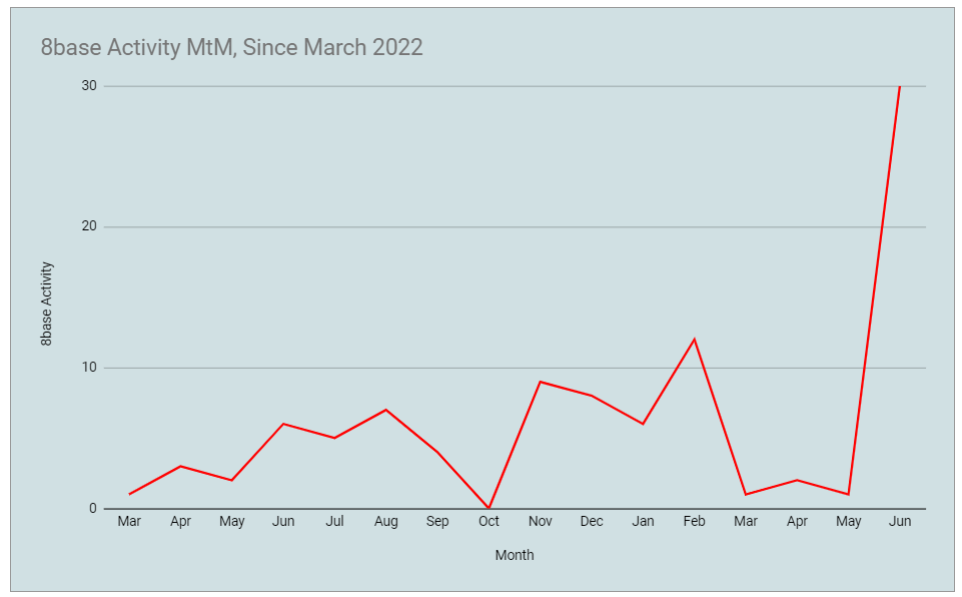
The 8Base group appeared in March 2022, but until June 2023 carried out few and insignificant attacks. However, this summer their activity increased dramatically, and they began to attack many companies in various industries. So far, 8Base has reported 35 victims on its site, sometimes announcing up to six new victims in a single day. The hackers call themselves “honest and simple pentesters” and offer companies “the most loyal conditions” for the return of their data. Though, that’s not something particularly new – LockBit tries to hold the same image.
About 8Base Ransomware
According to VMWare researchers from the Carbon Black team, 8Base’s attack tactics indicate that they are a rebranded version of another well-known ransomware gang, quite possibly RansomHouse.
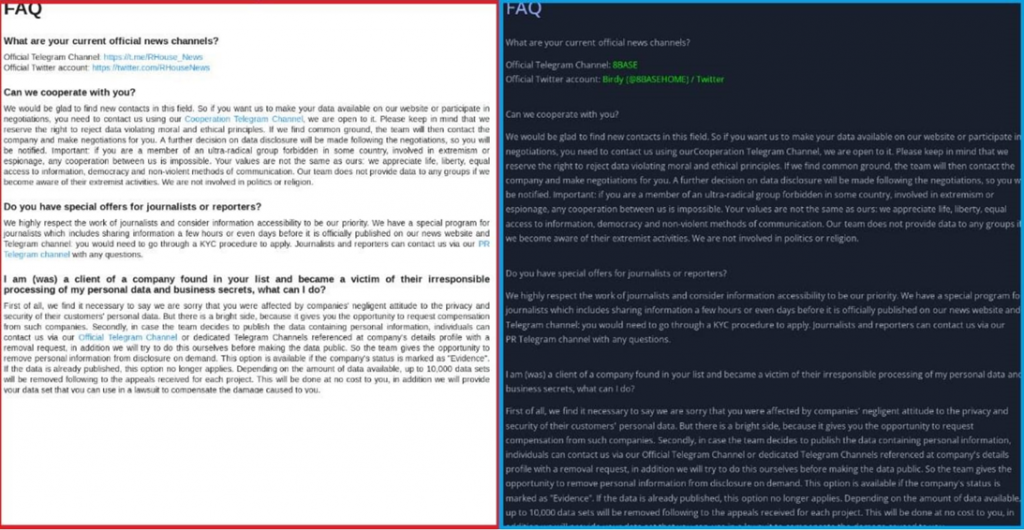
RansomHouse is a ransomware group that claims not to carry out encryption attacks, but only cooperates with other ransomware operations to sell their data. VMware suspects that 8Base is a fork of RansomHouse. Such conclusions were drawn due to the same ransom notes used by both groups, as well as the very similar style and content of the text on the respective data breach sites, where even the FAQ pages appear to be copied.

However, there is no reliable confirmation of the connection between 8Base and RansomHouse. It is not uncommon for cybercriminal gangs to simply copy ransom notes, software, methods and tactics. It helps hackers to save time and effort, and is especially probable if they invite someone from another ransomware group.
Ransomware analysis
8Base attacks use a modified version of Phobos v2.9.1 ransomware, which is loaded via SmokeLoader. Phobos is a Windows-targeting ransomware that first hit cyberspace in 2019, and it also shares many similarities with another ransomware code, Dharma.
During the attack, the virus, launched by 8Base operators, adds the extension of the same name “.8base” to all encrypted files. Ransomware expert Michael Gillespie reported that the Phobos ransomware also used a similar “.eight” extension for encrypted files. In addition, both programs, Phobos and 8Base, use the same email address to contact the attackers – “helpermail@onionmail[.]org”, which also leads to some thoughts about the connection of these malicious operations.
Another notable finding by VMware analysts is that 8Base uses the “admlogs25[.]xyz” domain to host a payload that is associated with SystemBC, a malicious proxy software used by several ransomware groups to obfuscate C2 infrastructure. All of these findings by researchers show that 8Base operators have been carrying out encryption attacks for at least a year, but only recently gained attention after launching their data breach site and a surge in activity. 8Base is just beginning to get the attention of analysts, so many aspects of their technical nature remain unknown or unclear.






I had experience that may files affected by 8base ransomware. How can I solve this kind of virus? And how can retrieve my files? There’s other way to fix it? Thank you and God Bless.
Hello! Removing 8base ransomware is quite easy, you can try out GridinSoft Anti-Malware – it fits great for this purpose.
When it comes to files decryption, however, things are much less positive. 8base ransomware is quite new and there’s no way to decrypt the files, of course, away from buying the decryptor from cybercriminals. However, you can try recovering the files with file recovery tools – they can sometimes do the job even better than the decryptors. Also consider checking out your backcups on Google Drive or OneDrive: potentially, you will find originals of some of the files encrypted by ransomware.