Zimbra has released updates that fix vulnerabilities in its products. One of the vulnerabilities is critical, at a CVSS rating of 9.8, the other is of medium severity. Users of Zymbra Collaboration should install the update as soon as possible.
Zimbra Releases Fixes for SQL Injection, other Vulnerabilities
Zimbra has released critical security updates to address multiple vulnerabilities in its Collaboration software. These flaws, if exploited, could allow attackers to gain unauthorized access to sensitive data.
They could also execute malicious scripts or redirect internal requests to unauthorized endpoints. The most severe of these vulnerabilities, tracked as CVE-2025-25064, has been assigned a CVSS score of 9.8.
Technical Details
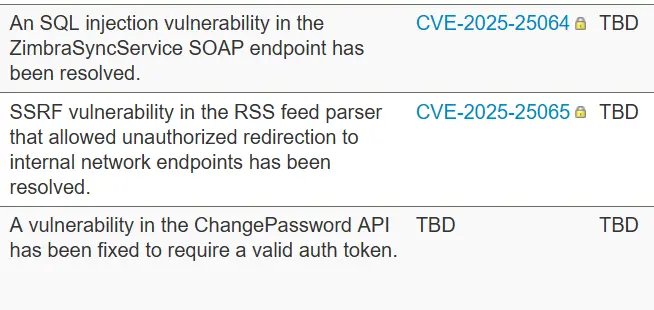
The first, SQL injection vulnerability CVE-2025-25064 (CVSS 9.8). This is a critical vulnerability that affects the ZimbraSync Service SOAP endpoint in Zimbra Collaboration versions 10.0.x before 10.0.12 and 10.1.x before 10.1.4. The flaw stems from improper sanitization of a user-supplied parameter, allowing authenticated attackers to inject arbitrary SQL queries. Exploiting this vulnerability could enable attackers to retrieve email metadata or manipulate database content.
The root cause lies in the failure to neutralize special SQL elements, allowing an attacker to manipulate the query structure. Recommended mitigations include the use of prepared statements, parameterized queries, and strict input validation to prevent unauthorized SQL execution.
Another major issue addressed in this update is a stored XSS vulnerability in the Zimbra Classic Web Client. This flaw has not yet been assigned a CVE identifier. It allows attackers to inject malicious scripts into stored content, potentially compromising user sessions and stealing sensitive data.
Zimbra has strengthened input sanitization mechanisms to mitigate this threat. The vulnerability has been fixed in Zimbra versions 9.0.0 Patch 44, 10.0.13, and 10.1.5.
Another fixed vulnerability is CVE-2025-25065. This is Server-Side Request Forgery (SSRF) Vulnerability that has CVSS 5.3. It exists in the RSS feed parser of Zimbra Collaboration versions 9.0.0 before Patch 43, 10.0.x before 10.0.12, and 10.1.x before 10.1.4. The flaw enables attackers to redirect requests to internal network resources. This could facilitate lateral movement or reconnaissance attacks within the targeted environment.
The SSRF vulnerability has been mitigated in the latest patches, reducing the risk of unauthorized internal resource access.
Response and Mitigation Measures
Zimbra has swiftly addressed these vulnerabilities and released security patches to mitigate potential risks. Users are strongly encouraged to upgrade to the latest versions of Zimbra Collaboration. The SQL injection vulnerability (CVE-2025-25064) has been fixed in versions 10.0.12 and 10.1.4. The stored XSS issue has been resolved in versions 9.0.0 Patch 44, 10.0.13, and 10.1.5. The SSRF vulnerability (CVE-2025-25065) has been patched in versions 9.0.0 Patch 43, 10.0.12, and 10.1.4.
| Affected | Patched In |
|---|---|
| Prior to 10.0.12 and 10.1.4 | 10.0.12, 10.1.4 |
| Prior to 9.0.0 Patch 44, 10.0.13, and 10.1.5 | 9.0.0 Patch 44, 10.0.13, 10.1.5 |
| Prior to 9.0.0 Patch 43, 10.0.12, and 10.1.4 | 9.0.0 Patch 43, 10.0.12, 10.1.4 |
To protect against these threats, administrators should apply the latest patches immediately, restrict access to SOAP endpoints, and monitor for suspicious activity. Administrators should perform regular audits and proper sanitization of user input are essential to mitigate any SQL injection and XSS risks. Given Zimbra’s history of being a frequent target for attackers, delaying updates could expose organizations to cyber threats. Keeping systems up to date with the latest patches remains the most effective way to ensure security.




