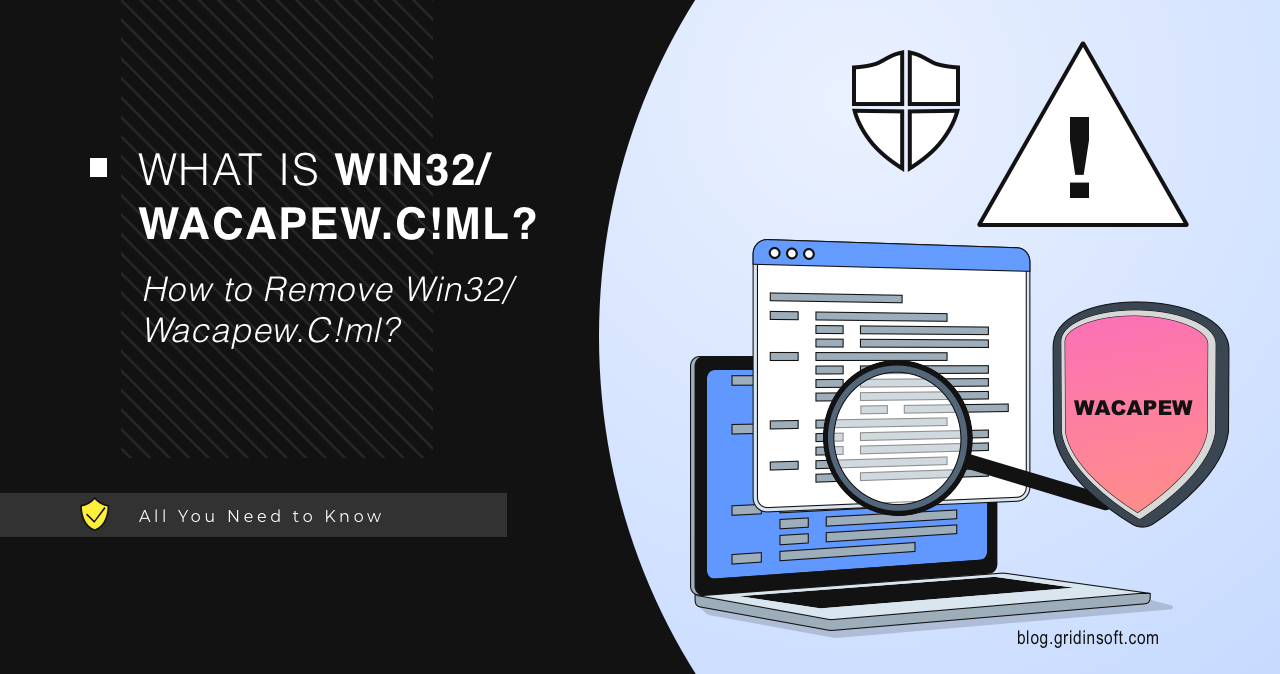
Program:Win32/Wacapew.C!ml detection refers to programs that have suspicious properties. This can be either a false positive or a detection of a program that has its properties & functions border with ones of a PUA. Let’s look into this and find out what this detection is.
What is Win32/Wacapew.C!ml?
Program:Win32/Wacapew.C!ml is a heuristic detection designed to detect a suspicious program. However, it is not a specific virus or malware. Microsoft Defender uses this type of detection to identify a wide range of questionable applications. All programs detected with this name typically exhibit suspicious properties. These include the ability to read and modify specific file properties, download data from remote servers, and rename themselves, which may indicate malicious behavior.
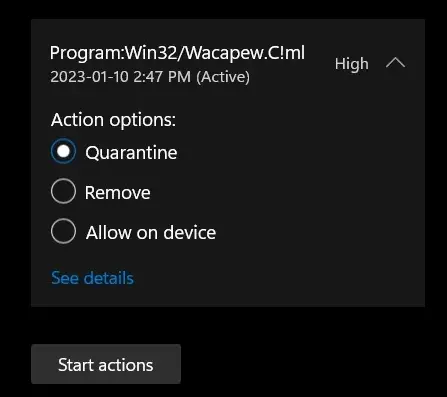
While these functions are barely enough to be sure about the program’s intentions, in the situations when other detection systems can neither prove nor deny the detection, the Defender is obligated to show the Wacapew.C!ml detection. It is more like “I don’t like this program” rather than “It is malicious”.
Among the typical examples of software detected as Wacapew are self-made applications or sketchy applets found on the Web. For instance, Microsoft Defender may flag a Python script converted into an EXE file as Wacapew for the request of admin privileges. Malware creators commonly use this conversion process, hence the suspicion arises.
Is It false positive?
Since detection with an “ml” ending means the use of an AI detection system, there is a possibility of it being a false positive. This adds on top of the blurry definition the Wacapew detection stands for. Normally, other detection systems should reject or approve the detection, leading to a different detection name or no detection at all. This, however, is not how it works in this case.
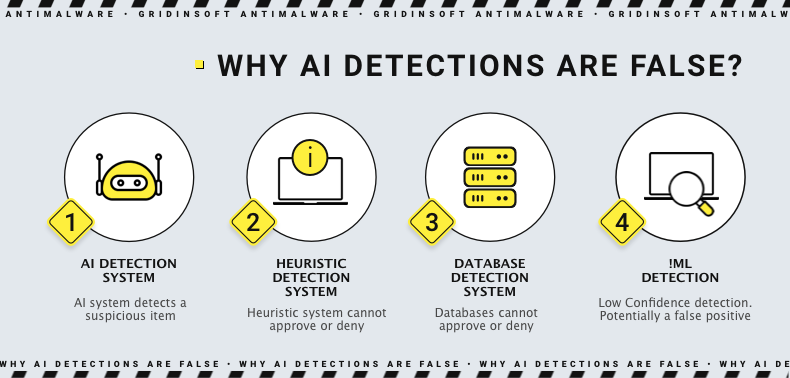
If Microsoft Defender detects a legit program with this name, be sure that you’re dealing with a false positive detection. But if you are not sure about the affected file’s origins and genuinity, consider scanning it with our Free Online Virus Scanner. It will analyze the file using its own detection systems, and give you a verdict whether the file is any dangerous, or not.
Program:Win32/Wacapew.C!ml Examples
The most prominent example of Wacapew detection is the Ollama model AI installer. Users online recon that the reason here is its similarity with Inno Setup-based installers. Inno Setup is a free installer for Windows programs that uses the eponymous script language and allows developers to fine-tune the installation process. However, besides the Inno installers, antivirus software detects installation files created with PyInstaller. In this case, the trigger is the lack of a file signature.
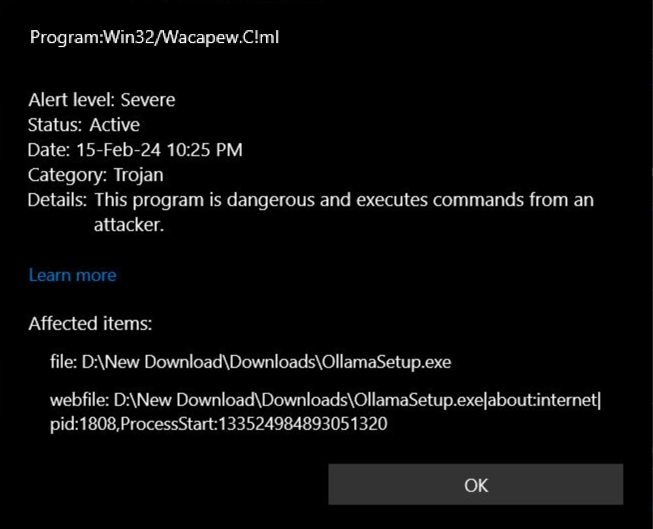
Another striking example is users’ files, such as architectural 3d models created with Enscape. GitHub also contains reports that downloaded files made in this program are detected as Win32/Wacapew.C!ml. In addition to all the above, such detections are not rare in pirated software. Since most of the latter is packaged with the said Inno Setup and may also have other questionable properties, Microsoft Defender starts showing the detection.
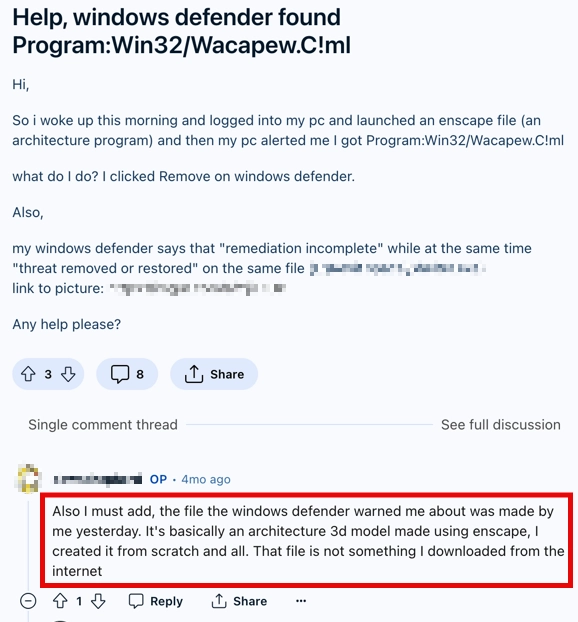
As you can see, any file without a proper signature and/or with something that may resemble a questionable one about it may trigger the Wacapew detection. Nonetheless, I would not recommend you to ignore the detection completely, as sometimes it can point at a genuinely dangerous app.
How to Remove Program:Win32/Wacapew.C!ml?
Unfortunately, some users have problems with Program:Win32/Wacapew.C!ml removal. In some cases, Defender fails to remove malware, showing notifications for files no longer on the device. To make sure your device is clean, I recommend using GridinSoft Anti-Malware. It will detect and remove Wacapew and find other malware. It can also work with Windows Defender to create an additional line of defense.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.