A team of four Google engineers is working on a new project called the Web Environment Integrity API, which will allow sites to block client applications that change their code.
In addition to the obvious security benefits, the new API will actually allow Google and site operators to effectively deal with ad blockers.
As you can easily guess from this introduction, the main goal of the project is to learn more about the person on the other side of the browser, to make sure that he is not a robot, and the browser has not been modified or faked in any way.
The developers say that such data will be useful for advertisers to count ad impressions, help fight bots on social networks, protect intellectual property rights, counter cheating in web games, and also increase the security of financial transactions.
That is, at first glance, the Web Environment Integrity API is designed as a security solution so that sites can detect malicious code modifications on the client side and disable malicious clients. The developers list several scenarios for the possible use of the new API:
- detection of manipulation in social networks;
- detection of bot traffic in ads to improve customer experience and access to web content;
- detection of phishing campaigns (for example, Webview in malicious applications);
- detection of mass takeover or account creation attempts;
- detection of large-scale cheating in web games with fake clients;
- Detection of compromised devices where user data may be at risk;
- detecting account takeover attempts by guessing a password.
At the same time, the authors of the Web Integrity API write that they were inspired by “existing native attestation signals, including [Apple] App Attest and [Android] Play Integrity API.”
It’s worth clarifying here that Play Integrity (formerly SafetyNet) is an Android API that allows apps to find out if a device has been rooted. Root access allows you to take full control of the device, and many application developers do not like this. Therefore, after receiving the appropriate signal from the Android Integrity API, some types of applications may simply refuse to start.
As a rule, banking applications, Google Wallet, online games, Snapchat, as well as some multimedia applications (for example, Netflix) refuse to work in such cases. After all, it is believed that root access can be used to cheat in games or phish banking data. Although root access may also be needed to configure the device, remove malware, or create a backup system, Play Integrity does not consider such uses and in any case blocks access.
As experts now assume, Google aims to do the same across the Internet.
By Google’s design, during a web page transaction, the server may require the user to pass an environment attestation test before they receive any data. At this point, the browser will contact a third-party attestation server and the user will have to pass a certain test. If the verification is passed, the user receives a signed IntegrityToken that confirms the integrity of their environment and points to the content to be unlocked.
Then the token is transferred back to the server, and if the server trusts the tester company, then the content is unlocked, and the person finally gets access to the necessary data.
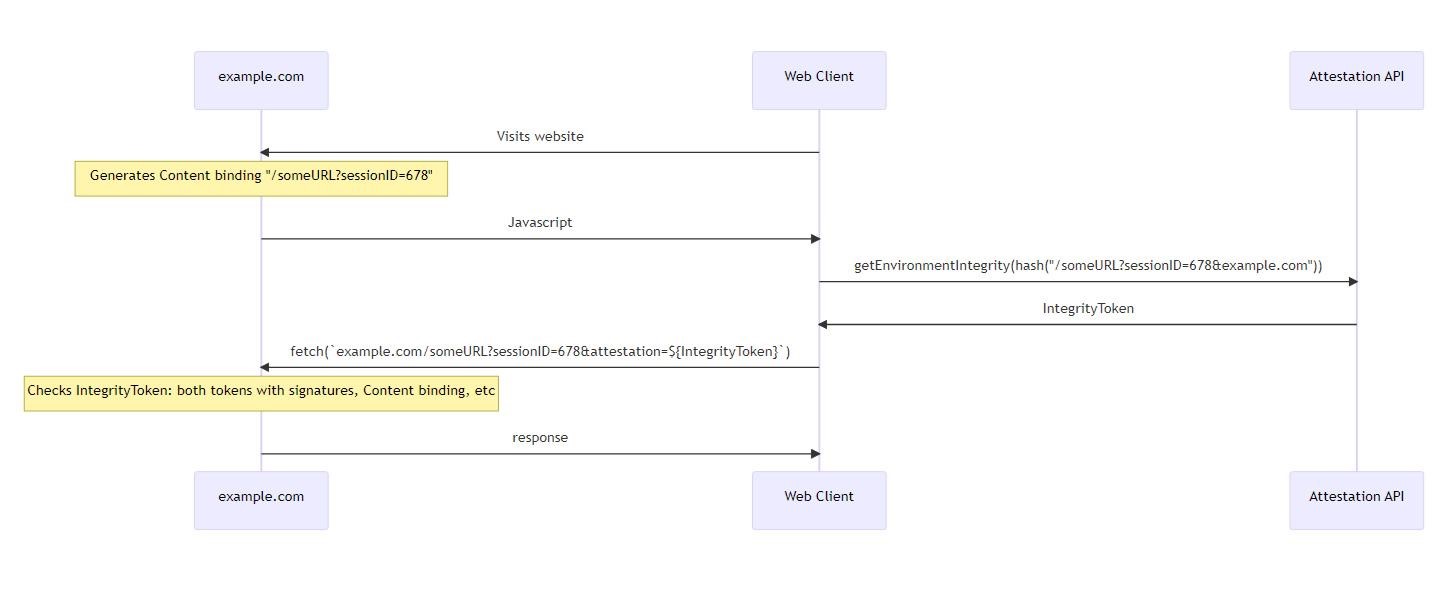
As many now assume, if the browser in this example is Chrome, and the attestation server is also owned by Google, then Google will decide whether or not to allow a person access to sites.
The company assures that Google is not going to use the described functionality to the detriment. Thus, the creators of the Web Integrity API “firmly believe” that their API should not be used for fingerprinting people, but at the same time they want to get “some kind of indicator that allows you to limit the speed in relation to the physical device.”
It also states that the company does not want to “interfere with browser functionality, including plugins and extensions.” Thus, the developers make it clear that they are allegedly not going to fight ad blockers, although the company has been working on the scandalous Manifest V3 for many years, whose goal is precisely this. We, by the way, wrote how the developers will implement these rules. And the new API can be used to detect when an ad blocker is tampering with ad code. After that, the site operator will be free to simply stop providing services.
The discussion of this topic on the network has already provoked a wave of criticism against Google, and the project has been dubbed DRM for the Internet. For example, developers, information security specialists, and ordinary users note that the Web Integrity API project intends to be hosted on GitHub by one of the developers, and Google is trying to distance itself from development that can literally poison existing web standards, helping the company save the advertising business.
The discussion on the project’s Issues page on GitHub also deals primarily with the ethical aspects of what is happening, and Google is accused of trying to become a monopolist in another area and “kill” ad blockers.
You might also be interested in our article on how Google membership rewards scam is a new popular type of online fraud.




