UnitedHealth Group, one of the largest providers of health insurance and health care services in the United States, suffered a cyberattack with the following data breach. The company admitted that the personal data of millions of patients was “stolen” in a cyberattack. This incident is already being called one of the largest in healthcare history. Total volume of data that hackers managed to leak is estimated at 6 terabytes.
UnitedHealth Hacked, Department Leaks Huge Amounts of Data
In February 2024, UnitedHealth Group experienced a massive cyberattack that compromised the data security of Change Healthcare. This division of the corporation processes medical claims and payments. As a result, systems responsible for processing prescriptions, medical claims and electronic payments were affected. This caused major problems for healthcare providers, pharmacies and payment systems across the country.
UnitedHealth Group responded quickly to the incident. They announced their intention to work with law enforcement to investigate the attack and strengthen security measures to protect patient data. The company also began notifying affected customers and offered them free credit history monitoring and fraud protection services as a compensation.
On Wednesday, UnitedHealth Group announced that it has made significant progress in restoring various core systems that were hit in the attack. It in particular caused an outage during the company’s response and impacted more than 100 Change Healthcare IT products and services.
Government Response
Size of UnitedHealth and its importance for the national healthcare industry could not keep the government silent. The U.S. Department of Health and Human Services has opened an investigation into the incident for a violation of the Health Information Protection and Accountability Act (HIPAA). The investigation is aimed at determining whether a breach of patient protection occurred. It also seeks to ascertain whether the relevant legal requirements for confidentiality of information were met.
UnitedHealth Group’s response was quick. They announced their intention to work with law enforcement to investigate the attack. Additionally, they vowed to strengthen security measures to protect patient data. The company also began notifying affected customers and offered them free credit history monitoring and fraud protection services.
BlackCat/ALPHV Claims Responsibility
ALPHV/BlackCat ransomware gang claimed responsibility for this attack earlier this year. Hackers announced that it was able to expropriate 6 terabytes of “highly selective data” regarding Change Healthcare customers. This information covers a wide range of data, including Tricare, Medicare, CVS Caremark, MetLife, and other large companies. It highlights the potential scale of the damage.
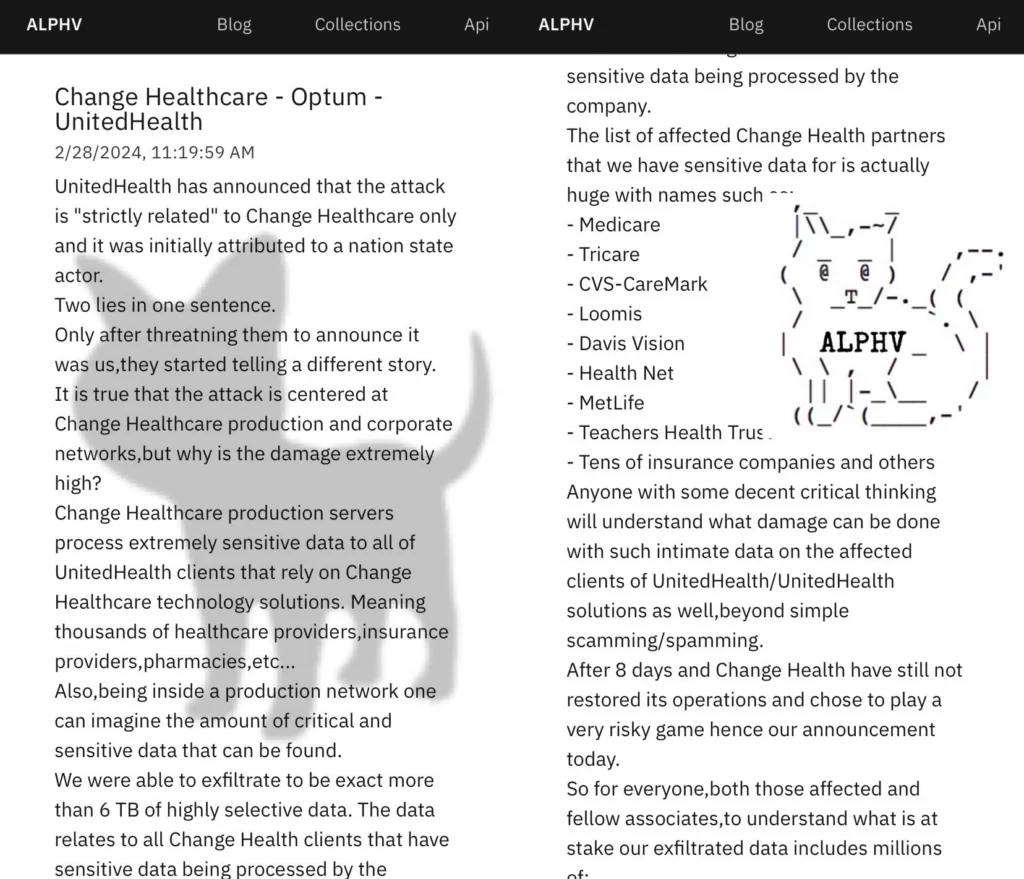
According to their story, UnitedHealth Group paid a $22 million ransom for a decryption key and a promise not to distribute the stolen data. This is a forced measure where the company is forced to pay huge sums to regain access to its own data and prevent further dissemination of stolen information. However, questions remain open as to whether BlackCat actually held the full ransom amount as claimed. Additionally, there are concerns about what assurances there are that the data will not be distributed or used in the future.
At the end of 2023, BlackCat’s infrastructure was seized in a coordinated law enforcement action. This severely disrupted the group’s operations for a period. Though as you can see BlackCat’s continued operations in defiance of law enforcement efforts. Disruption definitely slowed them down, but did not stop the operation entirely.
What stopped though is an exit scam, that group admins managed to pull in early March 2024. Hackers defrauded their partners, quitting the business with all the money of their affiliates. The said UnitedHealth subdivision appears to be one of their last targets – at least under this name. I expect them to resurface in this form or another.





