Tips & Tricks
Cloak Ransomware
Cloak ransomware is malware that encrypts user data and demands ransom. While some ransomware targets giant corporations, this specific instance…
0.31 BTC Promo Code STICKS
Social media users interested in cryptocurrency may have come across a 0.31 BTC Promo Code STICKS, endorsed by Elon Musk…
Norton Subscription Payment Has Failed Scam
Norton Subscription Payment Has Failed Scam is a fraudulent notification that appears on dubious websites designed to trick users into…
Windows Defender Security Center Scam
“Windows Defender Security Center” is a scam message that comes from a fake website. This fraud is built on the…
0.31 BTC Promo Code GRANTX Scam Overview
Crypto enthusiasts and investors may see 0.31 BTC Promo Code GRANTX Scam, promoted by Elon Musk, Bill Gates or another…
How to Get Rid of Spam Emails?
Email spam is an annoying and unwanted mailing of many…
Trojan:Script/Downloader!MSR
Trojan:Script/Downloader!MSR is a malicious script that downloads other malware onto…
How to Remove a Virus From a Computer in Safe Mode
In quite a few cases, you can see advice on…
How to Remove Trojan:Win32/Malgent!MSR from Windows 11
If you’re seeing Trojan:Win32/Malgent!MSR detected by your antivirus, don’t panic.…
Browser Extensions: Are They Safe?
Browser extensions are convenient little utilities that may adjust browsing…
Signs You’re Dealing With an Online Scam
Online scams have existed in one form or another since…
How to Stop and Block Spam Emails
Spam refers to the flood of unwanted emails that clutter…
15 Cybersecurity Myths and Denials
There are many cybersecurity myths, just as in any industry…
How to Secure Windows 10 from Hackers
Windows 10 boasts valuable features, providing comfortable tools for user…
Malware Protection
Many people remain unaware of the substantial benefits of malware…
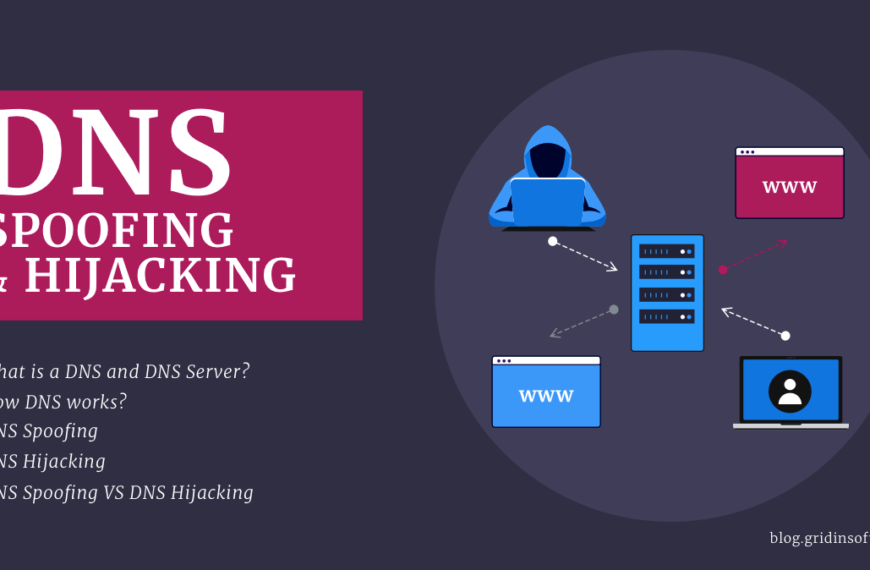
DNS Spoofing vs DNS Hijacking
Domain Name Services (DNS) play a crucial role in our…
Spam Email Revenge: Legal Ways to Fight Back Against Scammers in 2025
Tired of the endless barrage of spam emails flooding your…