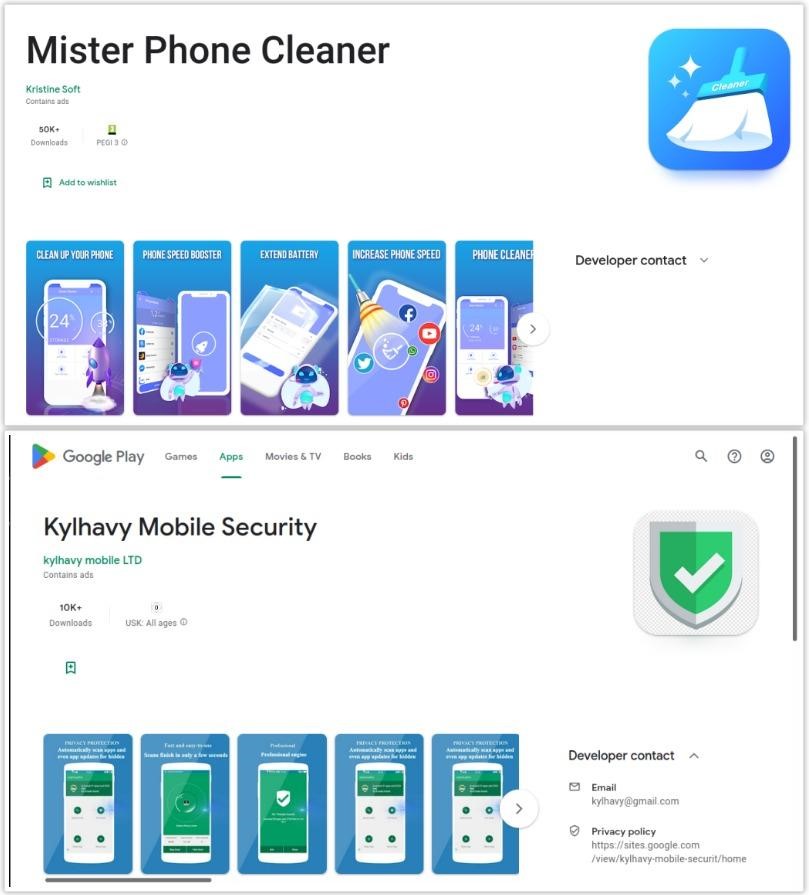
Information security specialists from Fox IT discovered two applications in the Google Play Store that distribute the SharkBot Trojan: Mister Phone Cleaner and Kylhavy Mobile Security were installed more than 60,000 times in total.
Let me remind you that we wrote that Researchers Found 35 Malware on Google Play, Overall Installed 2,000,000 Times, and also that Mandrake malware was hiding on Google Play for more than four years.
Let me remind you that in the spring of this year, NCC Group experts already warned about SharkBot. They said that malware usually disguises itself as antiviruses, actually stealing money from users who installed the application. SharkBot, like its counterparts TeaBot, FluBot, and Oscorp (UBEL), belongs to the category of banking Trojans capable of stealing credentials from hacked devices and bypassing multi-factor authentication mechanisms. For the first time, the malware was discovered by experts in the fall of 2021.
The NCC Group report emphasized that SharkBot’s hallmark is its ability to perform unauthorized transactions through Automatic Transfer System (ATS) systems, which, for example, distinguishes it from TeaBot, which requires infected devices to perform malicious actions in the interaction with a live operator.
As Fox IT experts now write, the applications detected this time do not contain malicious code right out of the box, and thanks to this they managed to deceive Google checks again. SharkBot infiltrates victims’ devices with one of the updates that occurs after the user installs and launches the dropper app.
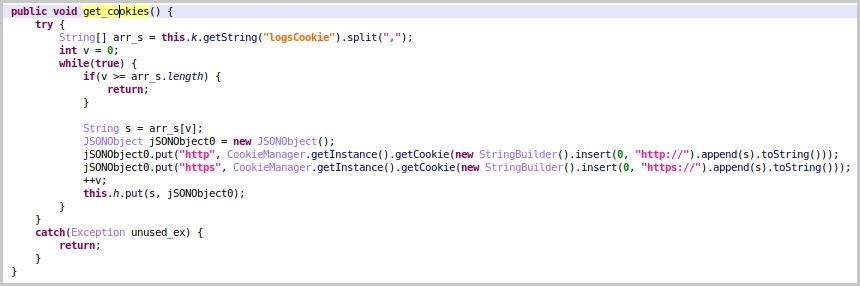
Back in May 2022, researchers from ThreatFabric wrote about the arrival of SharkBot 2, which revealed a DGA, an updated communication protocol, and a completely redesigned code. As Fox IT experts note, they also discovered and studied a new version of the malware (2.25), in which the possibility of stealing cookies appeared, and there was no abuse of Accessibility Services, as it was before.
Now, after installation, the dropper application contacts the control server, requesting the malicious SharkBot APK file. The dropper then notifies the user that an update is available and asks the victim to install the APK and grant him all necessary permissions. To make auto-detection difficult, SharkBot stores the hard-coded configuration encrypted using RC4.
In general, SharkBot 2.25 still uses overlays, intercepts SMS, can control the device remotely and contains a keylogger, but now the cookie stealing feature has been added to all this. So, when the victim logs into their bank account, SharkBot intercepts the session cookie with a new command (logsCookie) and sends the file to their operators.
The researchers write that SharkBot’s new campaigns target countries in Europe (Spain, Austria, Germany, Poland, Austria) and the US. It is noted that the malware is increasingly using a keylogger in attacks and stealing confidential information directly from the windows of real applications.




