SentinelOne experts noticed that the new version of the Sarwent malware opens the RDP ports on infected computers. Researchers believe that this is due to the fact that maware operators can sell access to infected hosts to other criminal groups.
Sarwent is a not-so-famous backdoor trojan, active since 2018. Previous versions of malware had a very limited set of functions, for example, they could download and install other malware on compromised computers.
“Sarwent has received little attention from researchers, but this backdoor malware is still being actively developed, and enforced with new commands. Updates to Sarwent malware show a continued interest in backdoor functionality such as executing PowerShell commands. Updates also show a preference for using RDP. Sarwent has been seen using the same binary signer as at least one TrickBot operator”, — write SentinelOne researchers.
However, the more recent Sarwent variation has received two important updates.
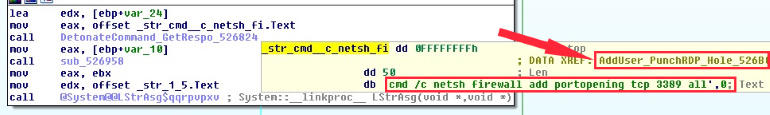
First, the malware “learned” to execute custom CLI commands using Windows Command Prompt and PowerShell. Secondly, Sarwent now creates a new Windows user account on infected machines, enables the RDP service, and then makes changes to the Windows Firewall settings to allow external access through RDP to the infected host.
In fact, this means that Sarwent operators can use the created account to access the infected host and will not be blocked by the local firewall.
Researchers note that so far the new version of Sarwent has been found only as a secondary infection when computers were infected with another malware, for example, Predator the Thief.
It is not yet clear what Sarwent operators do with RDP access on infected hosts.
“Typically, this evolution of the malware indicates a hacker’s desire to monetize the malware with new methods, or the new functionality may be determined by the needs of the customers of the attackers”, – write the researchers.
That is, the group standing behind Sarwent can independently use RDP access (for example, to steal proprietary data or deploy ransomware), or hackers can rent RDP access to infected hosts to other criminals.
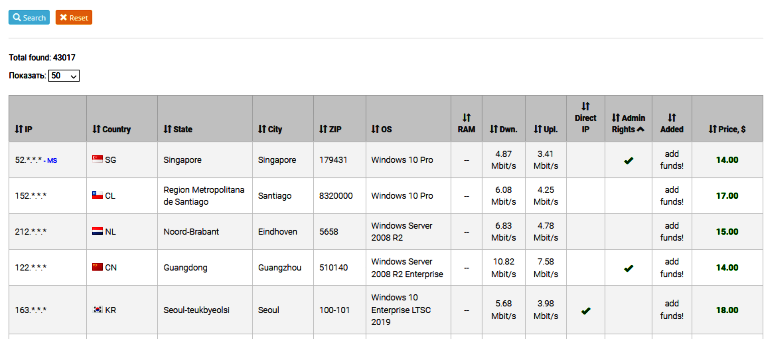
There is also a possibility that RDP endpoints are put up for sale on special trading platforms where they trade access to hacked networks and machines (an example can be seen below).
Let me remind you that due to pandemic, RDP and VPN usage grew by 41% and 33%.




