RDPLocker is a virus that encrypts the files and demands for a ransom payment for their decryption. It was first detected on malware analysis platforms at the very beginning of 2025, and by our observations attacks both individual users and corporations.
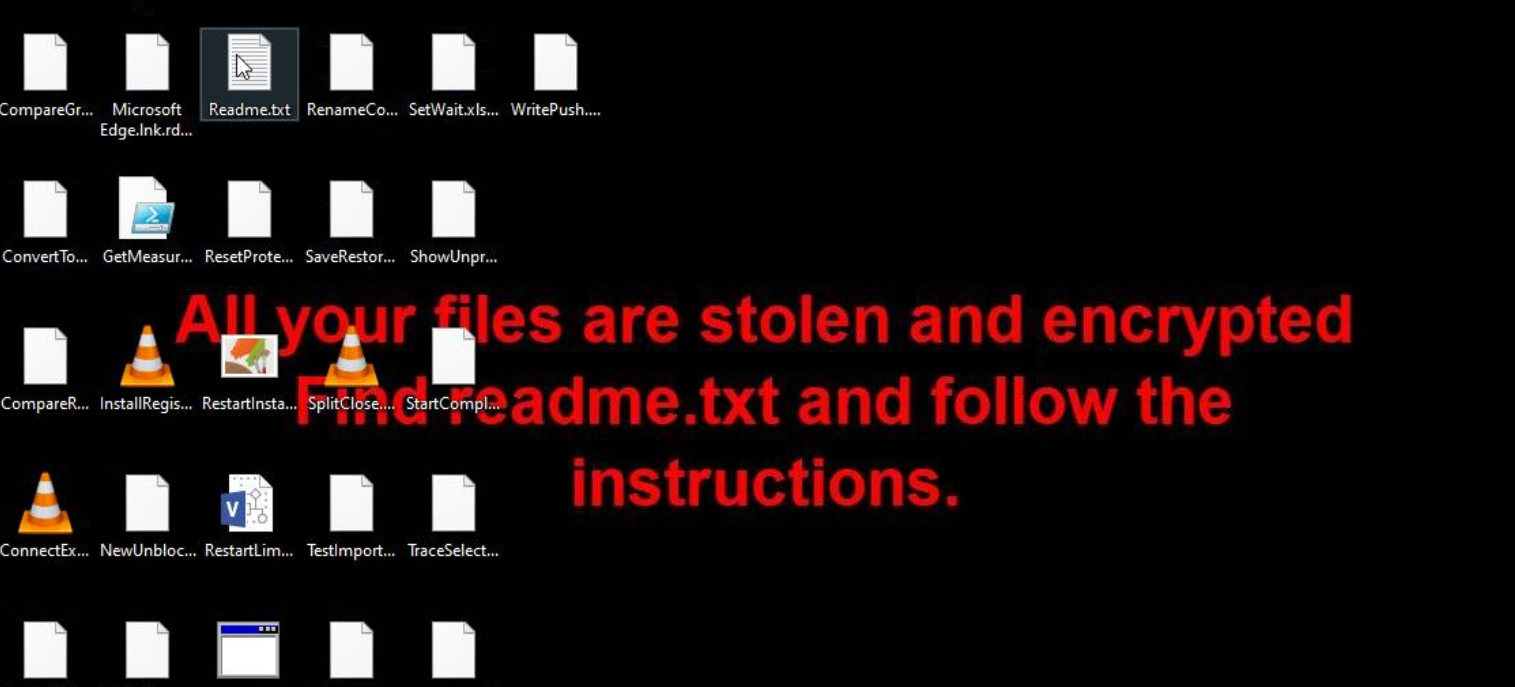
One of the distinctive features of the malware is the changes to system wallpaper: it swaps the original one for a black background with red sign on it. The sign says “All your files are stolen and encrypted. Find readme.txt and follow the instructions”. Users will also notice all the files getting the .rdplocker extension: document.docx will become document.docx.rdplocker, song.mp3 – song.mp3.rdplocker, and so on.
Readme.txt Ransom Note Overview
The mentioned readme.txt file is a ransom note, that contains basic description of what has happened and how one can revert the encryption. It also boasts of using intermittent encryption and describes it as something that makes malware undetectable and enormously fast. In fact, this technique is far from being new, and there are more effective ways to make the file encryption faster.
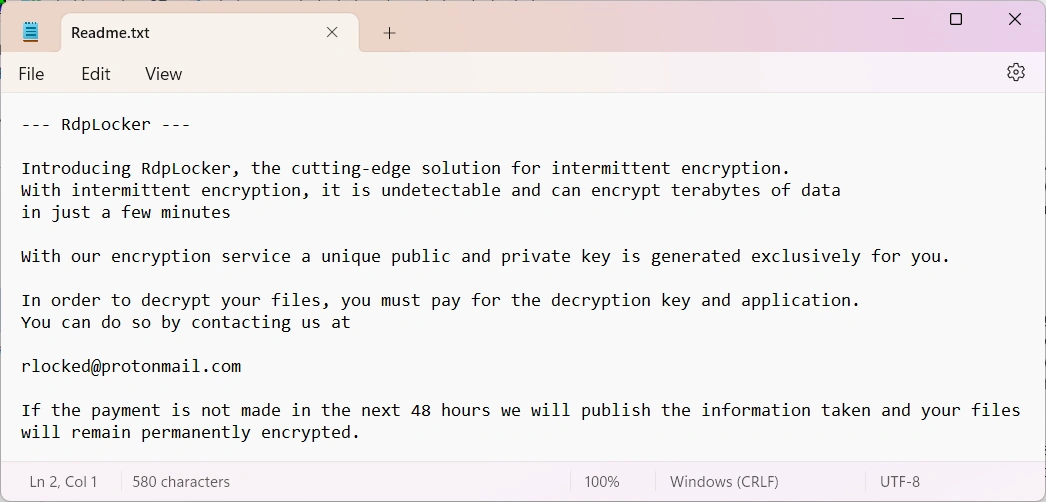
Other parts of the ransom note are fairly generic and consist of threats and promises of file recovery. Hackers say about the need to contact them within a 48 hour deadline, otherwise they will delete the decryption key and publish all the leaked data. For a contact information, they offer a single email address – [email protected]
RDPLocker Ransomware Overview
RDPLocker malware is an example of small-batch ransomware that non-selectively targets corporations and individuals. Typical distribution channels for this malware include email spam and online scams, like the fake human verification pages. Due to the extensive packing and encoding, the malware is highly evasive for static analysis, meaning that standard antivirus software may struggle to detect it.
Upon execution, the malware checks a selection of system characteristics to prevent it from running on virtual machines or in debug environments. After passing these checks, RDPLocker starts its malicious activity by stopping Microsoft Defender and disabling/deleting all the basic Windows backup methods.
Once done with “preparing” the system, the ransomware switches to file encryption. The used encryption algorithm is quite strong and in fact excludes any brute force decryption. Nonetheless, there are options for free file recovery that I will describe in the next section of that article.
The encryption process ends up with adding a ransom note to C:\Users\%username\Links, and changing the wallpaper to its specific one. Simultaneously, the malware assigns the decryption key a timestamp, so malware actors can count 48 hours from that moment.
How to Remove RDPLocker Virus?
Before any recovery attempts, I will heavily recommend one to remove the malware. After finishing the encryption, it remains active, seeking for more files to cipher. As the result, all the recovered files will get encrypted as soon as they end up in the system.
GridinSoft Anti-Malware is a program that will get you covered. Its multi-component detection system will detect and remove the ransomware, regardless of how evasive it is. Download it by clicking the banner below, and run a Full Scan to check the entire system.
How to restore .rdplocker files?
Despite how “cutting-edge” RDPLocker ransomware is, there are several ways to recover the files. Intermittent encryption may hamper the ability to access the file directly, but leaves enough file content untouched to perform recovery operations.
Try running media files (videos, music) with WinAmp. As only certain sections of the file are encrypted, you are likely to be able to run the files with some specific software. Remove the ransomware extension and give it a try. It will expectedly miss the ciphered parts, but that is already better than having no accessible files at all. WinAmp fits the purpose as it ignores file integrity, which is obviously disrupted in the encrypted files.
Large files are often unencrypted. To speed up the process, ransomware may ignore files that are over 500MB in size, only appending its extension to it and moving on to the next file. Archives (7z, RAR, ZIP etc), large videos and some of the MS Office documents can be free of any encryption. All you need is to remove the ransomware extension and try opening them as usual.
Use file recovery tools. One more remedy is using file recovery tools. Depending on the way the malware handles the files during the encryption process, it may be possible to restore them in pre-encryption state. Any tool of your choice will fit; key characteristic is the ability to recover as much file formats as possible.