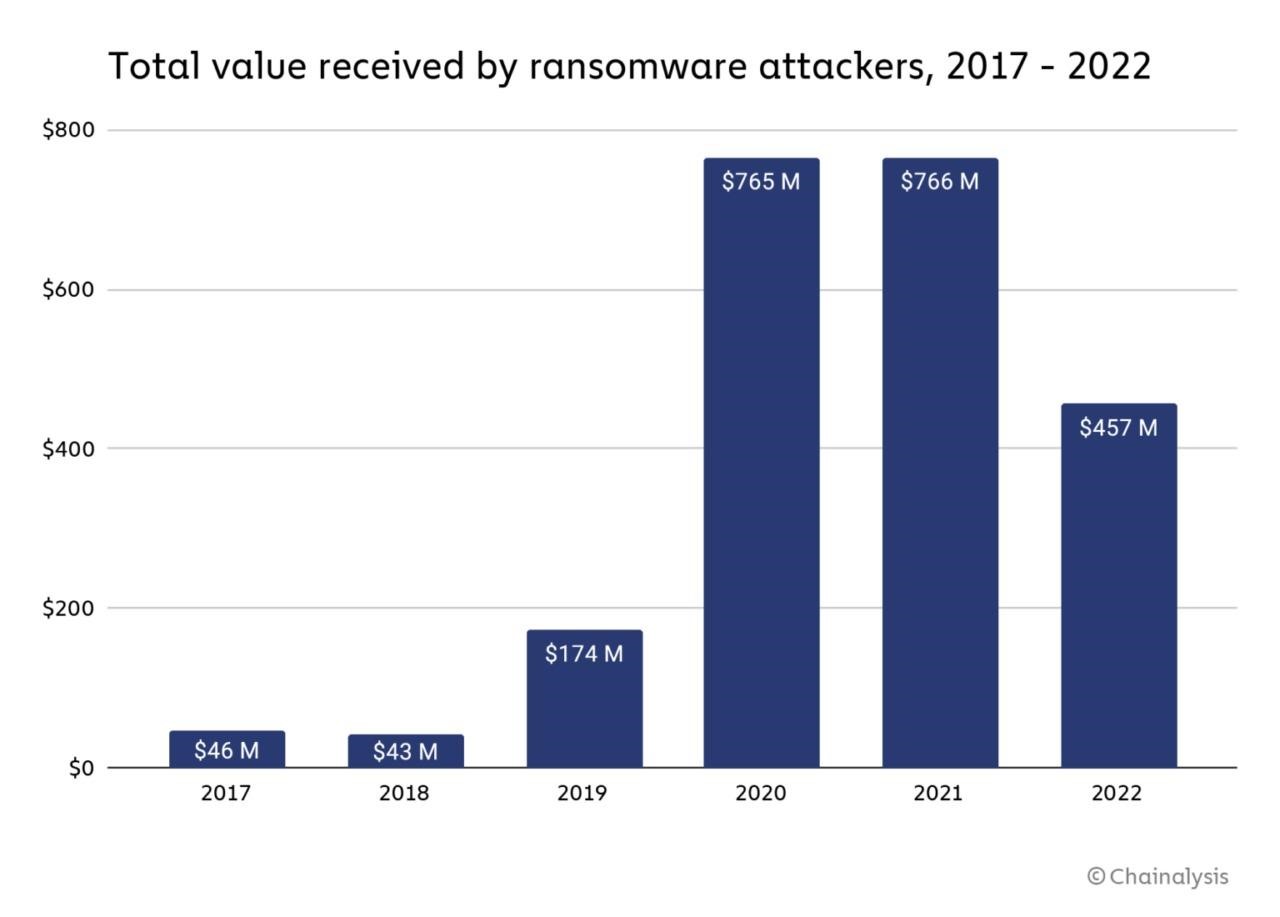
Ransomware revenue (from ransomware attacks) has fallen from $765.6 million in 2021 to $456.8 million in 2022, according to Chainalysis blockchain analysts.
Experts attribute this drop of more than 40% to many factors, but the main reason is simple: more and more victims simply refuse to pay hackers.
Read also: Huge Ransomware List by Gridinsoft Research.
The researchers note that they cannot know about all the wallets used by cybercriminals, but payments clearly show a significant decrease compared to the peak during the COVID-19 pandemic.
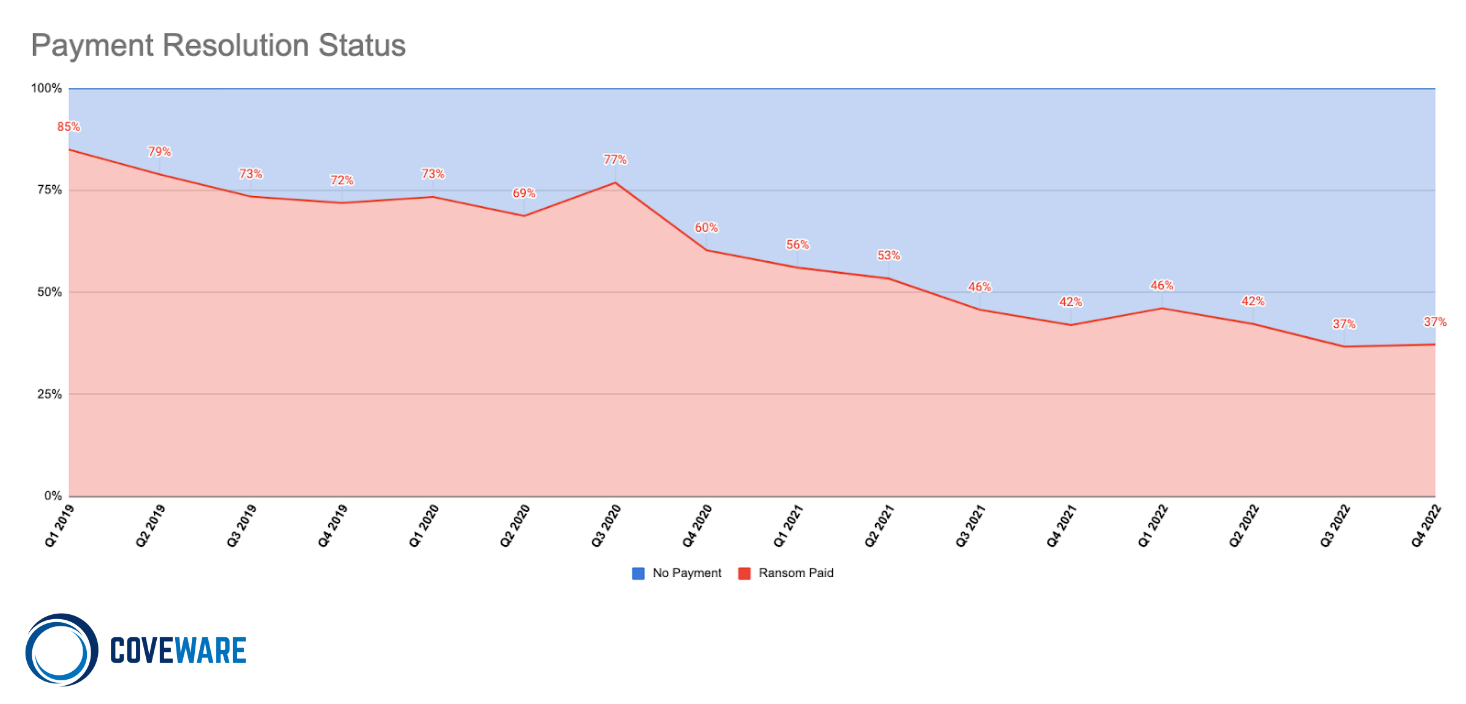
These findings are supported by Coveware researchers, a company that helps organizations respond to ransomware attacks. According to them, the percentage of companies that paid a ransom in 2022 fell to 41% (compared to 50% in 2021 and 70% in 2020).
Coveware researchers attribute the drop in attacker revenues to companies’ investment in security and incident response planning, improvements in law enforcement that are increasingly returning victims’ funds and arresting criminals, and the overall effect of fewer payments pushing ransomware out of the market.
At the same time, it is noted that average and median buyouts increased significantly in the last quarter of 2022 compared to the previous quarter. The average size of a ransomware victim company has also grown, especially in the second half of 2022.
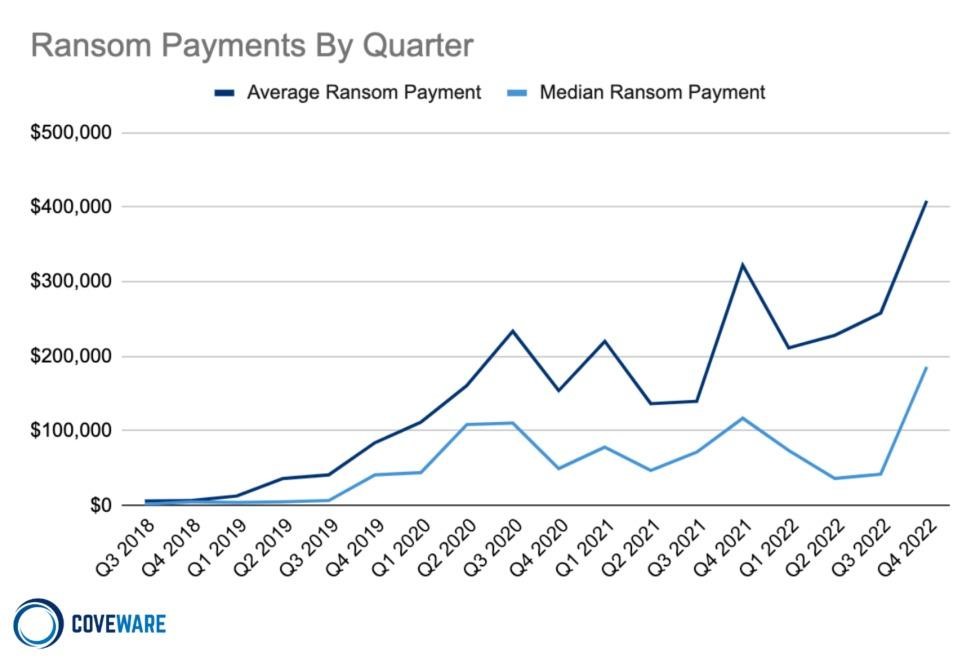
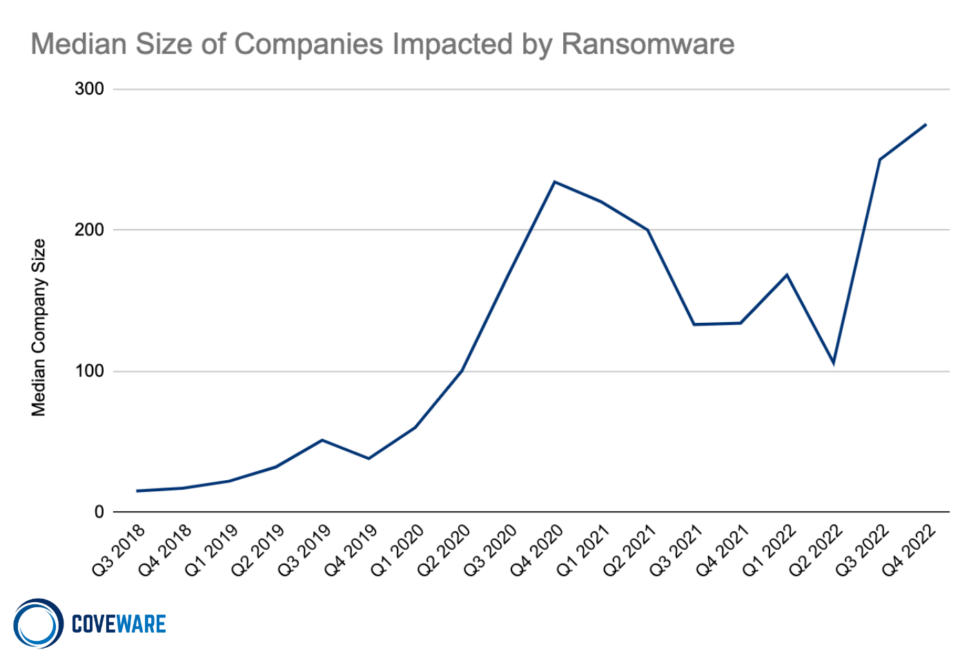
Coveware suggests that this is also a consequence of the fact that attackers have become less likely to pay: attacks on larger companies provide hackers with the opportunity to demand larger ransoms.
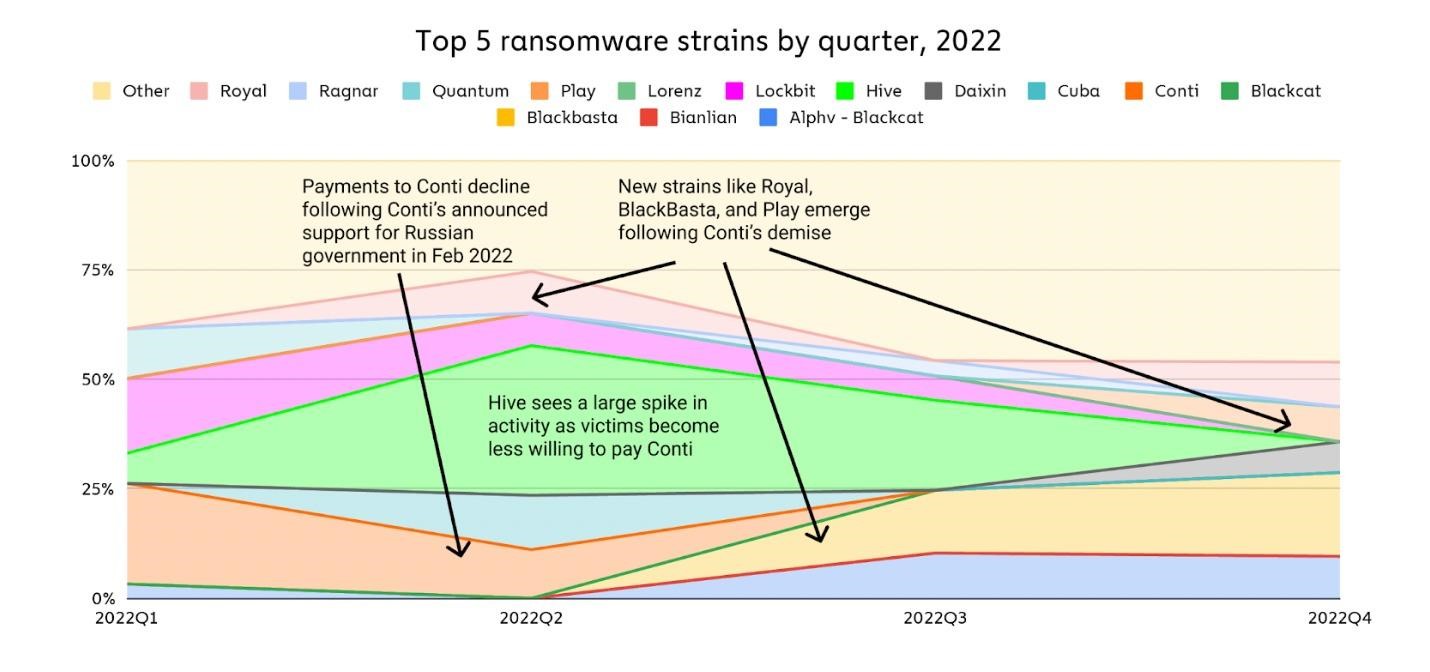
The researchers also note that last year the Conti hack group, which was the leader of this “market”, broke up, after which its members moved to a number of other groups. And while ransomware attacks may look like a huge “market” with thousands of participants, it is actually not a very large area, the group of main participants of which can still be tracked.
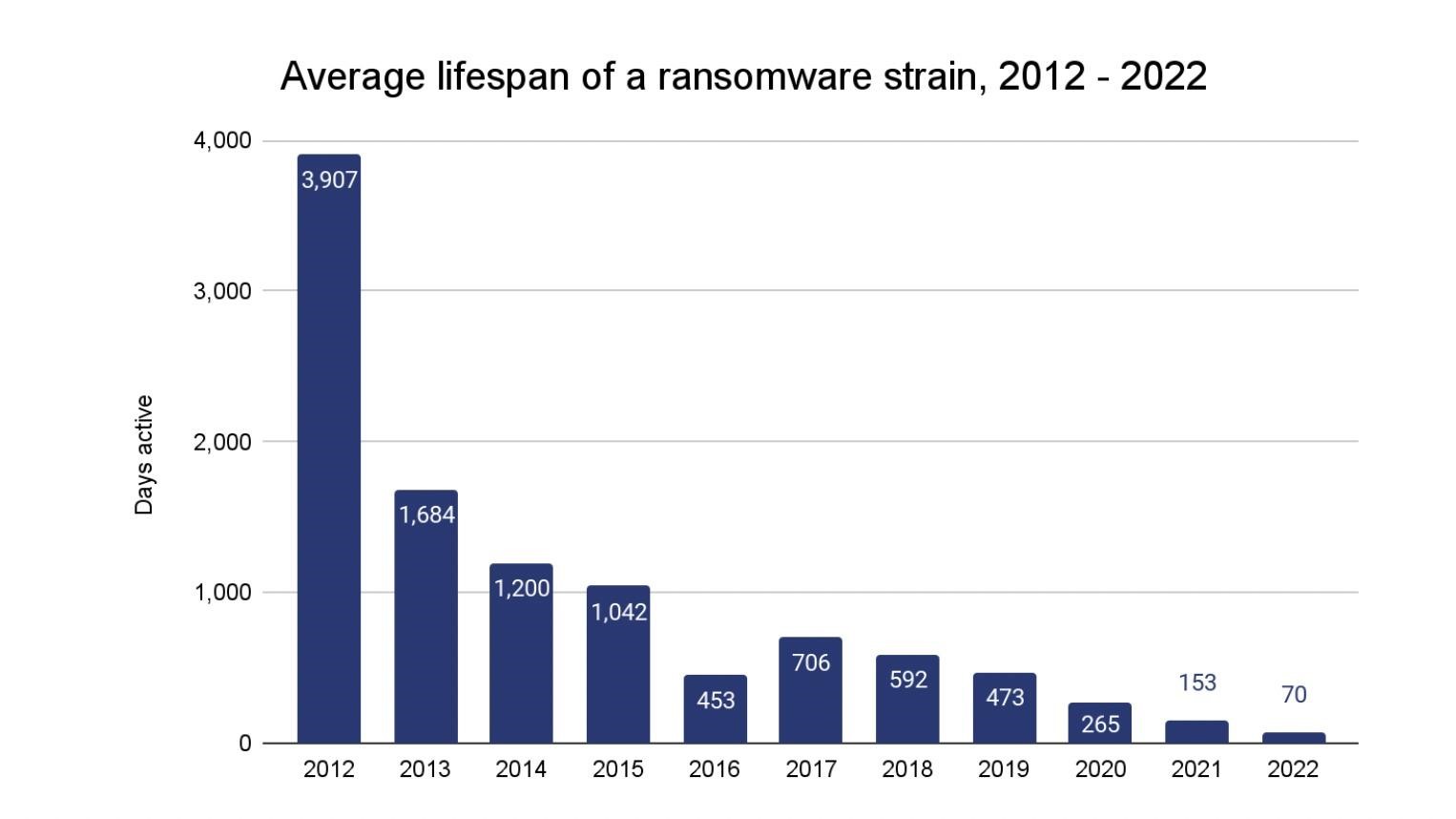
Supporting this theory is the fact that in 2022, ransomware remained active for an average of 70 days, which is much less compared to 153 days in 2021 and 265 days in 2020. Researchers attribute this to the fact that attackers seek to hide their activity and work faster, since many of them work with several strains of malware at once.
In addition, another consequence of what is happening has been a change in the money laundering schemes used by extortionist groups. With law enforcement increasingly shutting down cryptocurrency exchanges and mixer services, hackers are increasingly turning to unnamed major exchanges to launder stolen funds. So, according to Chainalysis, extortionists now send up to 48.3% of all funds received to large exchanges.




