Experts are intestigating activity of the ransomware group Akira, which has compromised at least 63 organizations since March 2023, mostly targeting small and medium-sized businesses. Analysts at Arctic Wolf believe that Akira may be backed by several people associated with the ceased Conti group.
Conti Hackers Work in Akira Ransomware Group
As mentioned above, Akira mainly attacks small and medium-sized businesses, and companies around the world become victims of the ransomware, although hackers focus on targets in the United States and Canada. The gang typically infiltrates target Windows and Linux systems through VPN services, especially if users have not enabled multi-factor authentication. To gain access to victims’ devices, attackers use compromised credentials, which they most likely buy on the dark web.
Once the system is infected, Akira seeks to delete backups that can be used to restore data, and then the ransomware encrypts files with specific extensions, adding the “.akira” extension to each of them. The ransom note that the attackers leave in the system is written in English, but contains many errors. In this message, the group claims that they do not want to cause serious financial damage to the victim, and the amount of the ransom will be determined based on the income and savings of the affected company. Usually Akira demands a ransom of between $200,000 and $4,000,000.
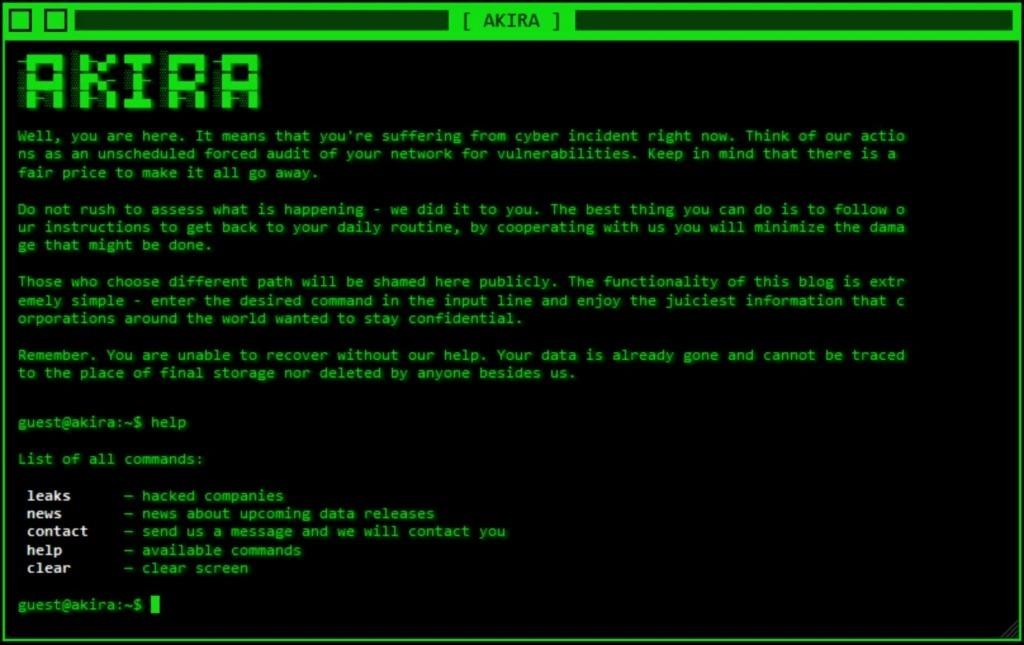
Experts point out that Akira uses “double extortion” tactics, not only encrypting victims’ data, but also stealing information from compromised systems before encryption. After that, the attackers threaten to publish or sell this data to other criminals if they do not receive a ransom.
The Akira ransomware is in many ways similar to the Conti ransomware that was shut down a year ago, the researchers said. The malware ignores the same types of files and directories, and uses a similar encryption algorithm. But it should be borne in mind that at the beginning of 2022, the Conti sources were made publicly available, and now the attribution of attacks has become more difficult.
Back in June, Avast researchers released similar data about Akira’s likely connection to Conti, saying that the creators of the new ransomware were at least “inspired by the leaked Conti source codes.”
There were other news upon Conti members’ activities past the group dissolution. Conti operators participated in attacks on Ukrainian companies. It’s worth noting that earlier this month, Avast released a free decryption tool for files affected by Akira attacks. So far, the tool only works on Windows, and after its release, the malware operators changed the encryption procedure to prevent free file recovery.
Arctic Wolf researchers, in turn, focused on blockchain analysis and found three suspicious transactions in which Akira users transferred more than $600,000 to Conti-related addresses. According to experts, two discovered wallets have previously been linked to the management of Conti, and one of them received payments from several families of extortionists.