Ah, the classic “Professional Hacker” email scam. Someone claims they’ve hacked your computer, recorded you doing embarrassing things, and now demands payment. Welcome to the digital version of “your shoelace is untied” followed by “give me your lunch money.”
What’s This Scam All About?
These emails come with dramatic subject lines like “Your personal data has leaked due to suspected harmful activities.” The message basically says a professional hacker cracked your device, spied on you for months, and caught you in compromising positions. Now they want Bitcoin, or else.
Different versions exist, but they all follow the same script: scare you, claim to have dirt on you, demand payment. It’s like a bad movie plot that somehow keeps getting remade.
The Opening Act: Scary Tech Jargon
The email starts with impressive-sounding claims about “hacking your operating system” or “gaining full access to your account.” To tech-savvy folks, this sounds like someone who learned hacking terminology from a 90s movie. To everyone else, it sounds just scary enough to keep reading.
They throw around phrases that sound technical but make actual IT professionals snort coffee through their nose. It’s the digital equivalent of a kid wearing a trench coat and claiming to be an adult.
The Middle: “I’ve Been Watching You”
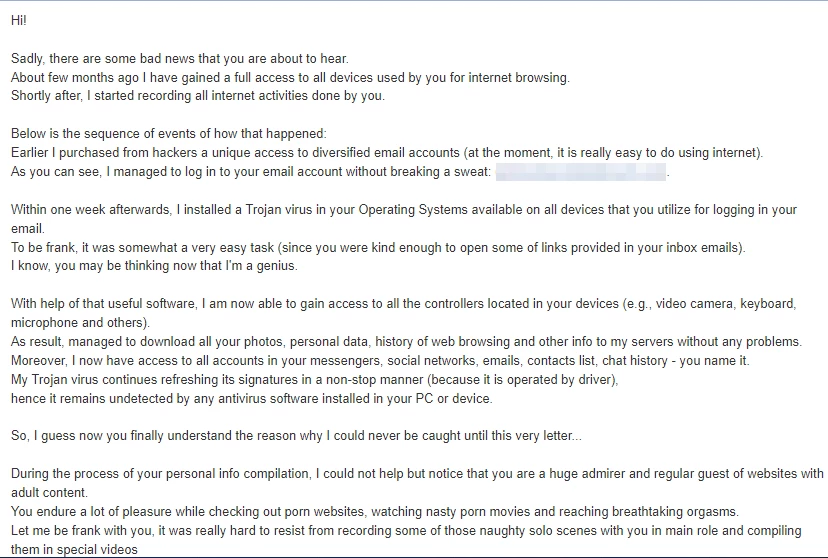
Next comes the creepy part – claims about monitoring your activities for months. According to these “hackers,” they installed malware through adult websites you supposedly visited. This explanation conveniently plays on shame and embarrassment, making victims less likely to discuss the email with others.
In reality, mass-sending these emails is far more profitable than actually spying on random people for months. These scammers are lazy by design – why hack one person when you can scare thousands?
The Password Twist: “Here’s Proof I Hacked You”
Some versions of this scam include a particularly clever trick – they show you one of your actual passwords. Suddenly, their claims seem a lot more credible, right? “If they have my password, maybe they really did hack my computer!”
Here’s what’s actually happening: The scammer purchased your email and password from a data breach. Major sites get hacked all the time, with millions of credentials dumped on dark web marketplaces. These scammers buy these lists in bulk for pennies per thousand emails.
The password they show you is likely from a breach that happened years ago. If you still use that password anywhere, that’s the real security problem – not their imaginary spyware. These scammers have no access to your computer; they just have an old password from a completely different website.
The Climax: The Webcam Recording Claim
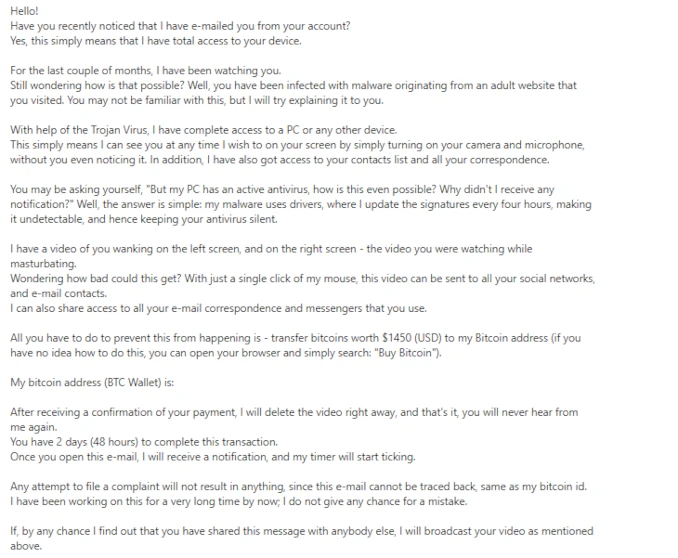
The knockout punch is always about your webcam. Supposedly, they recorded you watching “adult content” and captured your reaction on camera. They even claim to have created a split-screen video showing both you and what you were watching.
It’s a clever claim because it’s nearly impossible to disprove and plays on universal fears about privacy. The email also specifically mentions sextortion – threatening to share the non-existent explicit content unless you pay up.
The Technical Mumbo-Jumbo
To sound legitimate, these emails include technical gibberish about driver-level malware that “refreshes signatures every 4 hours” to avoid detection. This is like claiming your invisible car also makes great espresso – impressive but nonsensical.
Actual malware doesn’t need hourly updates to avoid detection. That would be like a burglar changing disguises every hour while hiding in your closet – unnecessarily complicated and risky.
The Grand Finale: Pay Up or Else
The conclusion is always a ransom demand, typically between $850-2000 in Bitcoin. They set an artificial deadline of 48-72 hours to create urgency. And they always include a Bitcoin wallet address that looks like alphabet soup had a fight with a calculator.
Some versions even warn that if you share the email with anyone else, they’ll immediately release the non-existent videos. Convenient way to isolate potential victims, isn’t it?
Known Scammer Bitcoin Wallets
These scams use numerous Bitcoin wallet addresses. If you receive an email demanding payment to any of these addresses, it’s 100% a scam:
- bc1qzxzazuz7twfx4e0mzfg97606d5dytksue9j3ag
- 1N6TYc2FFJmjMDPnAKQgjRh65ou58EfQNM
- bc1qz3hct7u9x6tfh4guk3e7wyjaxa2gnalzfgr3kh
- 12nEVuGNtRFMVjeVmLtD4nt2sHX68S47yH
- 1Er1bTsfVpy2uZ88hBDJf1i66SuYxQCRKb
- 1HBiRxpSxekVND1Rqwqh1gbUKeZiYBsDkt
- 19AEV6b6SMVTByErnpaQUDCUWK5cN8gYqh
If you spot one of these addresses (or any similar Bitcoin address) in a threatening email, report it to IC3.gov (FBI’s Internet Crime Complaint Center) and your local authorities. Never send money to these addresses – the scammers will likely just demand more once they know you’re willing to pay.
A Real Example of This Nonsense
These scam emails often begin with subjects like “Your personal data has leaked” or “Ihre persönlichen Daten sind wegen des Verdachts auf schädliche Aktivitäten nach außen gelangt” (for German recipients). The messages are often available in multiple languages because scammers are thoughtful like that.
So Is This Real or What?
No, it’s not real. Not even slightly. It’s just a mass-sent scare tactic banking on statistics – send enough emails and eventually you’ll find someone worried enough to pay.
Any professional hacker who managed to compromise your system wouldn’t announce it with a dramatic email. That would be like a burglar sending you a postcard saying “Hey, I stole your TV yesterday!” Real attackers prefer to stay undetected as long as possible.
The technical claims in these emails fall apart under even casual scrutiny. Anyone with basic IT knowledge can spot the nonsense about “driver-based malware” with “4-hourly signature updates.” It’s the cybersecurity equivalent of claiming your unicorn needs special rainbow feed.
The Psychology Behind The Scam
These scammers are amateur hackers but professional manipulators. They use several psychological tricks designed to bypass your rational thinking.
The Authority Card
They open by establishing themselves as “professional hackers” with technological superpowers. This appeal to authority works because most people don’t know exactly what hackers can and can’t do. It’s like claiming to be a “professional ghost hunter” – if you don’t know the field, you might just believe it.
They load the email with technical-sounding terms to reinforce this perceived expertise. Most people won’t recognize that these terms make actual security experts laugh their coffee out.
Shame As A Weapon
The scammers specifically mention adult websites and compromising recordings to trigger embarrassment. They know embarrassed people make poor decisions and are less likely to seek help. It’s a classic manipulation tactic – make someone feel shame, and they’re easier to control.
The genius part is mentioning something many people do privately, making the victim think “But how did they know?” The answer: they didn’t. They just made a good guess.
The Urgency Trigger
The 48-72 hour countdown creates artificial urgency to force quick, emotional decisions. This is the same trick used in those “limited time offer” commercials, except with more blackmail.
When people feel rushed, they make mistakes. The scammers know this and use time pressure to override your critical thinking.
What To Do If You Get This Email
First, take a deep breath. Your secrets are safe, your camera hasn’t been hacked, and no one has been spying on you. This is just digital junk mail with extra intimidation.
Mark the email as spam and delete it. Never respond to these messages – even clicking “unsubscribe” links just confirms your email is active, bringing more spam your way.
If the email includes one of your actual passwords, change that password anywhere you still use it immediately. Then check if your email has been involved in data breaches using services like Have I Been Pwned. This is a good reminder to use unique passwords for every site and enable two-factor authentication on important accounts.
If you’re worried about webcam security, put a piece of tape over it when not in use. It’s low-tech but effective – even Mark Zuckerberg does it.
For extra peace of mind, run a malware scan on your system. Contrary to what the email claims, good security software can detect actual threats. GridinSoft Anti-Malware will spot and remove genuine malware – unlike the imaginary super-stealth malware in the scam email.
Protect Yourself From Real Threats
While this specific email is fake, real cybersecurity threats do exist. Update your software regularly and use strong, unique passwords for important accounts. Consider using a password manager to keep track of them all.
Be skeptical of unsolicited emails, especially those with attachments. A legitimate company rarely sends unexpected attachments, and your bank will never ask for your password via email.
Enable two-factor authentication on important accounts. It’s like having a second lock on your door – even if someone gets your password, they still can’t get in without your phone.
These simple habits will protect you from actual threats, not imaginary hackers with magical malware. And if you ever receive another “professional hacker” email, you can have a good laugh before hitting delete.





The thing this article doesn’t mention about this scam is that sometimes it includes a password that the victim has actually used in the past, and also it may be sent from the victim’s e-mail address to itself, which can make the threat look more real and serious (which is the reason why I myself googled about it, honestly)
Same as Wonchi said, email comes from one’s email address and includes a password that has been used in the past. Tricky for sure but still scam.
Same scam e-mail over here: the scammer stated an old password and it was sent from a @hotmail.com e-mail address.
Indeed felt quite scary in the beginning, but after some google searches, things started to calm down.
Especially this article really made me calm down, thanks.
Nevertheless I changed practically all my passwords into more complicated ones.
But how can I report the scammer? Does hotmail.com have an option for this?