News, Tips, Security Lab
The AI-Controlled Drone Did Not “Kill” Its Operator Even During the Simulation. At Least for Now
At the recent Future Combat Air and Space Capabilities summit, the head of AI testing and operations at the US…
Russian Hacker Sells Terminator Tool That Is Allegedly Able to Bypass Any Antivirus Programs
A tool called Terminator appeared on one of the Russian hacker forums, and, according to its author, can destroy any…
What is Business Email Compromise (BEC) Attack?
Business email compromise attack, or shortly BEC, is a relatively new vector of cyberattacks. Dealing primary damage by exposing potentially…
MOVEit MFT 0-day Vulnerability is Used to Steal Corporate Data
MOVEit managed file transfer (MFT) solution appears to contain a 0-day vulnerability, already exploited by hackers. Progress, the developer of…
New iOS Vulnerability Allows “Triangulation” Attack
New iOS vulnerability allows executing a zero-click malware delivery through the built-in iMessage messenger. The breach was discovered by Kaspersky…
The FBI believes that the HelloKitty cryptor is controlled by operators from Ukraine
A medical organization from Oregon, which recently reported a breach and data leak, accidentally made it clear that, according to the FBI, HelloKitty (FiveHands) malware is controlled by operators from…
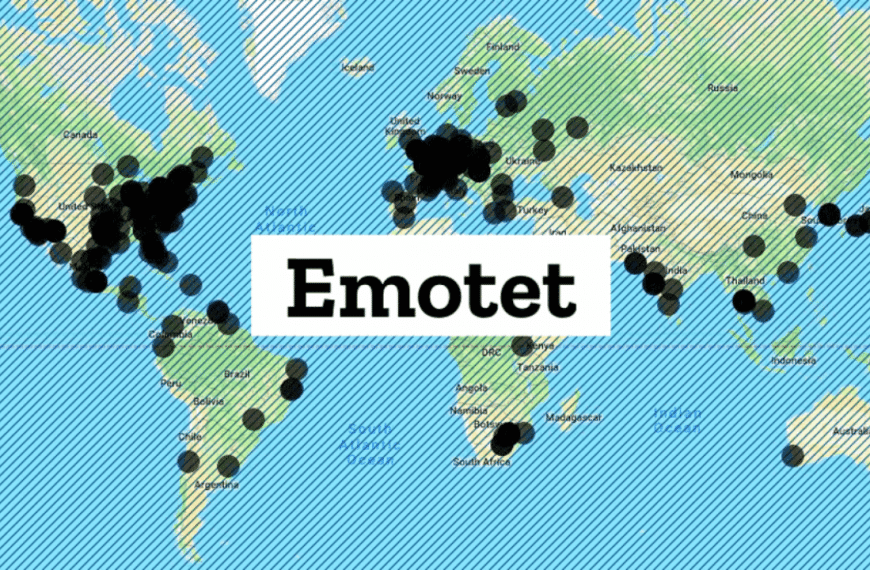
Microsoft patches Windows AppX Installer vulnerability that spreads Emotet malware
The latest of this year, December’s patch Tuesday brought fixes for six 0-day vulnerabilities in Microsoft products, including a bug in the Windows AppX Installer that uses Emotet malware to…
How to Remove a Virus From a Computer in Safe Mode
Most widespread viruses can be removed from your PC without any additional setups. However, some “serious” examples of computer viruses can block the anti-malware software usage or just load the…
Experts are already fixing attacks on the Log4Shell vulnerability
Security researchers are already scanning the network looking for products affected by a dangerous bug in the Log4j library and are fixing the results of cybercriminals’ attacks on a Log4Shell…
Major corporations teamed up to fight AI bias
American corporations have teamed up to form the Data & Trust Alliance, which has developed a software assessment system to fight AI bias. When hiring employees, HR departments are increasingly…
0-day In Log4j Library Poses A Threat To Many Applications & Servers
The Apache Software Foundation has released an emergency security update that fixes a 0-day vulnerability (CVE-2021-44228) in the popular Log4j logging library, which is part of the Apache Logging Project.…
Emotet now installs Cobalt Strike beacons
The researchers warn that Emotet now directly installs Cobalt Strike beacons on infected systems, providing immediate access to the network for attackers. Those can use it for lateral movement, which…
Google Stops Glupteba Botnet and Sues Two Russians
Google representatives said that they stopped the work of the Glupteba botnet: they deleted the accounts, and also disabled the servers and domains associated with it. In addition, the company…
Vulnerability in Apple iCloud puts billion users at risk
Security of over a billion iPhone owners and users of popular instant messengers is at risk due to a vulnerability in Apple iCloud. As the Forbes reports, private messages sent…
US Cyber Command confirms cyberattacks against ransomware
The United States Cyber Command has publicly recognized the use of offensive actions (cyberattacks) in order to neutralize cybercriminal groups that attacked American companies using ransomware programs. The Head of…
Unlocking the Secrets of Messaging Apps: An In-Depth FBI Study Guide on Accessible Data for Law Enforcement
An FBI study guide has been made publicly available as part of a Freedom of Information law request filed by Property of the People, an American non-profit organization that deals…
Hackers introduced a web skimmer on the site of the Sealand Principality
The Record reported that unknown hackers attacked the site of the Sealand Principality (a self-proclaimed virtual state in the North Sea) and introduced a web skimmer on it. The attackers…