US authorities have detained a developer associated with the LockBit group, one of the most active ransomware creators. Investigators allege he has been working as a programmer for the notorious hacker group since January 2022. Israeli law enforcement took him into custody, and the U.S. is now seeking his extradition.
LockBit Developer Rostislav Panev Charged
In February 2024, UK and US law enforcement seized the infrastructure, including its servers and websites. Thousands of decryption keys and victim-related information were obtained by the authorities. Affected companies are now being encouraged to seek assistance in recovering their stolen information.
Rostislav Panev, 51-y.o. dual Russian-Israeli citizen, has been charged in the U.S. for his alleged role as a developer of LockBit, specifically the cryptor and data extraction tools, and also maintained the gang’s infrastructure. His brainchild is what enabled cybercriminals to deploy ransomware without advanced technical skills by offering pre-built tools and infrastructure.
Panev, who was active in the operation from 2019 to February 2024, was arrested in Israel in August 2024 and is currently awaiting extradition to the U.S. This is a rather unusual situation as Israel typically refuses to proceed with extradition of their citizens. Yet it seems this time the guy is way too bad for Bagatz to cover him.
What is LockBit Ransomware?
LockBit is a ransomware-as-a-service (RaaS) platform that allows cybercriminals to deploy ransomware without requiring advanced technical skills. It provides pre-built tools and infrastructure, enabling attackers to encrypt data and demand ransoms. It has several versions and we have a separate post dedicated to LockBit ransomware.
Although the suspect’s lawyer, Sharon Nahari, is prepared to vigorously defend his client and claims he was merely a developer communicating with the group via Telegram, an analysis of cryptocurrency proceeds suggests otherwise. Panev is alleged to have earned $230,000 between June 2022 and February 2024 through cryptocurrency payments tied to his work with LockBit.
Evidence recovered from his computer indicates that he had access to source code and tools, including StealBit. StealBit is a data exfiltration tool used to steal sensitive information before encrypting victims’ systems. His involvement went beyond coding; he also provided technical guidance and worked closely with Dmitry Khoroshev, known as LockBitSupp.

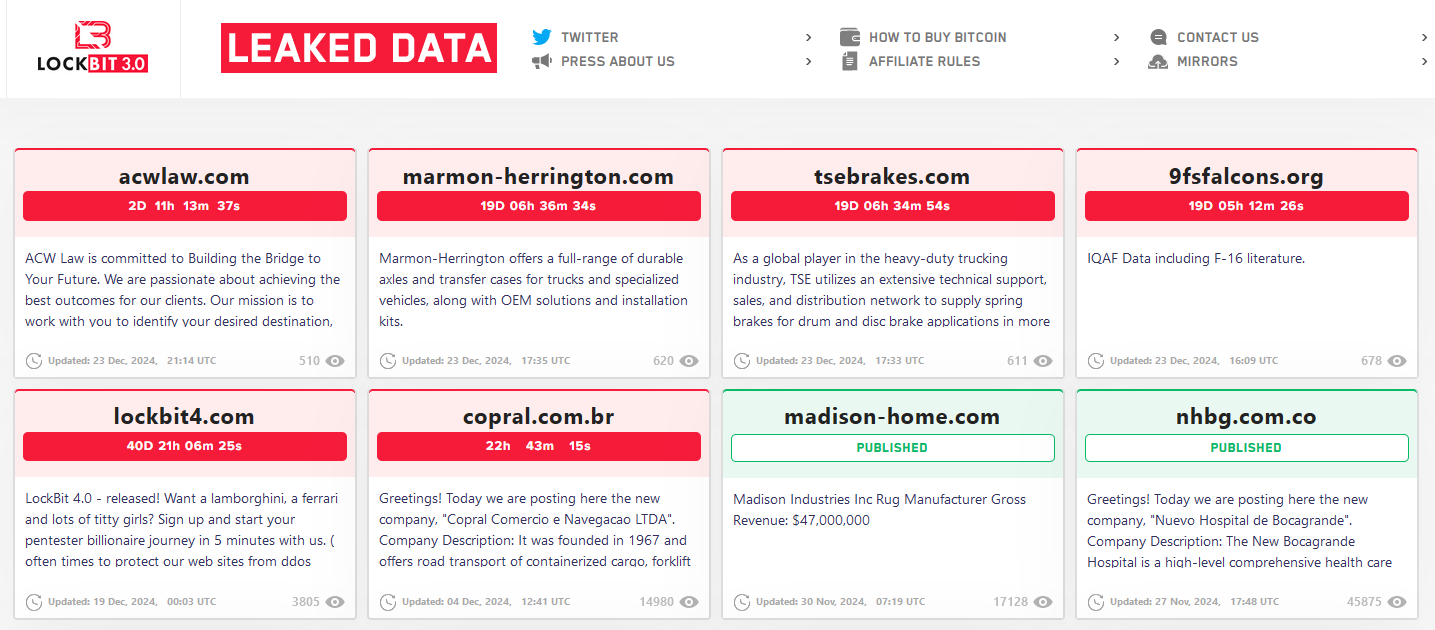
How about victims, the LockBit attacked over 2,500 entities across 120 countries, targeting victims ranging from small businesses to critical infrastructure. The group reportedly generated $500 million in illicit profits. Despite a major law enforcement operation, ‘Cronos,’ which dismantled its infrastructure in February 2024, the group has announced plans for a resurgence with LockBit 4.0, expected in February 2025.
LockBit 4.0 Released
Despite losing their key developer, the ransomware group managed to release a new version of their ransomware. They’ve announced the release on their Darknet leak pages, and also launched a whole new affiliate hiring campaign. It is not new for the gang to perform such actions in a pompous manner, yet it looks strange considering all the previous events.




