Cybersecurity researchers have reported the creation of a first-of-its-kind UEFI bootkit for Linux systems. The tool, called Bootkitty, is considered a proof-of-concept (PoC) and, according to experts, has not been employed in real attacks.
UEFI Bootkitty Bootkit Targeting Linux Systems
ESET analysts have reported the discovery of a new UEFI bootkit named Bootkitty, targeting Linux systems. Although currently a proof-of-concept, the malware signals a growing attacker focus on Linux bootkits. This area has traditionally been dominated by Windows-based threats, but as *NIX-based OS gains more and more user share, hackers switch their attention here.
Bootkitty was uploaded to VirusTotal in November 2024 under the file name bootkit.efi. Researchers found that the malware is in the early stages of development, with limited effectiveness against specific Ubuntu versions. Its numerous technical flaws suggest that Bootkitty is not yet ready for real-world deployment. Experts believe it is being tested as a proof-of-concept.
Written in C, Bootkitty is designed to bypass Linux kernel signature verification. It uses a self-signed certificate, making it ineffective on systems with Secure Boot enabled unless the attackers’ certificates have already been installed. The malware specifically targets systems with certain versions of GRUB and the Ubuntu kernel. Indicators of compromise related to this malware have already been uploaded to GitHub.
During execution, Bootkitty exploits UEFI protocols (EFI_SECURITY2_ARCH_PROTOCOL and EFI_SECURITY_ARCH_PROTOCOL) to bypass Secure Boot integrity checks. It manipulates the GRUB bootloader using functions like start_image and grub_verifiers_open to disable binary signature checks, including those for the Linux kernel. It also interferes with the kernel decompression process, modifying the module_sig_check function so that all kernel modules are falsely verified as secure.
To load its malicious components, the malware replaces the first environment variable with LD_PRELOAD=/opt/injector.so. This ensures that the malicious shared library is loaded into processes during system startup.
Real-World Attacks
In the known attack cases, hackers exploit the LogoFAIL flaw and other well-known vulnerabilities in UEFI firmware to install Bootkitty. For instance, certain exploits target improper input validation during the processing of splash screen images, which can result in arbitrary code execution.
What Is UEFI Bootkit?
UEFI Bootkit is a type of threat that aims to modify or spoof components of the UEFI, the system that controls the booting of an operating system. The main danger of a bootkit is that it operates at the level of the computer’s boot process. This means it gains control before the operating system starts and can persist even after the operating system is reinstalled.
Removing such a threat with anti-malware is not really an option. Complete bootkit malware removal requires either reinstalling the UEFI, which does not always guarantee complete removal of the threat, or flushing the UEFI with a programmer. In some cases, replacement of the motherboard may be required.
Possible Links to BlackCat
The user who uploaded Bootkitty to VirusTotal also submitted a kernel module named BCDropper, which installs an ELF file called BCObserver. This module functions as a rootkit, hiding files and processes while opening specific ports on the infected system.
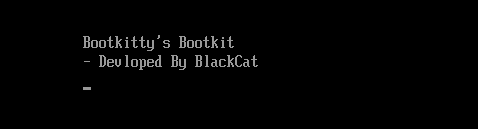
The code of Bootkitty and the module contains multiple references to “BlackCat”. One of the key clues is a phrase “Developed by BlackCat” that appears in some execution logs and in BCDropper’s code. However, the researchers caution that this does not confirm a connection to the eponymous ransomware group, especially considering it being deceased after its creators pulled a scam escape on their affiliates.





