Gridinsoft Security Lab
Funny Tool Redirect Extension Virus – Easy Removal Instructions
Funny Tool Redirect is a malicious browser extension that you may see installed in your browser. It spreads through dodgy websites and does a rather unusual mischief: blocking access to the Chrome Web Store. While being not a big deal at a first glance, its unwanted appearance, along with other extensions (like JsTimer) that spread […]
Trojan:Win64/Reflo.HNS!MTB
Win64/Reflo.HNS!MTB is a detection of a malware sample that aims at stealing confidential information. It usually spreads through game mods and works as quietly as possible. That virus may belong to any malware family, as it is a behavioral detection of a specific action that it does in the system. Win64/Reflo.HNS!MTB Overview Trojan:Win64/Reflo.HNS!MTB is a […]
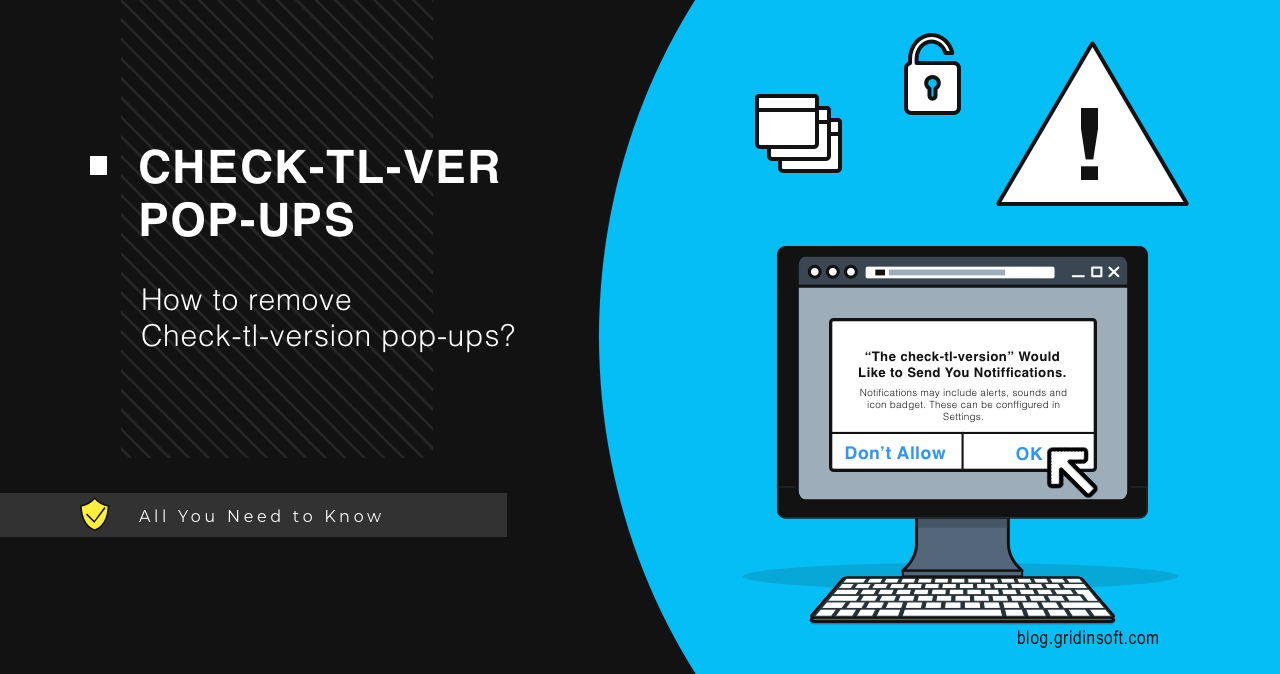
Check-tl-ver Pop-Up Virus
Analysis shows a hike in the number of malicious pop-ups that come from Check-tl-ver websites. It is a rather common strategy of aggressive marketing that aims to spam users after forcing them to allow sending notifications from the aforementioned websites. Let’s figure out what this scam is, and how to stop Check-tl-ver pop-ups. What are […]
Trojan:PowerShell/CoinStealer.RP!MTB
Trojan:PowerShell/CoinStealer.RP!MTB is a detection of Microsoft Defender, that normally flags malware that can steal cryptocurrency wallets. You may see it popping up after downloading a program from the Web or running a dodgy PowerShell script. More precisely, it collects credentials of different applications, and crypto wallets are among its primary targets. The Stealthiness of this […]
PUABundler:Win32/DriverPack
PUABundler:Win32/DriverPack is potentially unwanted software that claims to install or update drivers. In fact, it floods the system with unwanted software and changes browser settings without the user’s consent. In this post, I will explain the dangers behind this unwanted app and show the ways to remove it from the system. PUABundler:Win32/DriverPack Overview PUABundler:Win32/DriverPack is […]
Virus Alert (05261) Scam
“Virus Alert (05261)” is a scam pop-up message you can see on a website that looks like a Microsoft page, but with a strange URL. It tries convincing people about their system being in trouble. As proof of it, they show a banner saying about outdated apps, incorrect privacy settings, and more critical problems. The […]
Movidown Unwanted Application
Movidown is an Unwanted Application that initially mimics a utility for controlling fan speed. However, beneath this shell, it has the capabilities of a dropper malware, which it right away uses to deploy browser hijackers. This functionality, together with the deep access to the system, creates potential risks for much more severe malware to get […]
“Managed by Your Organization” – How to Remove From Chrome?
“Managed by your organization” is a line that appears when the web browser is attacked by browser hijackers. This malware abuses a legitimate Chrome policy to make itself impossible to delete. And it turns out to be pretty effective – without a special approach, all browser plugins remain untouchable after this line appears. In this […]
PUA:Win32/SBYinYing
PUA:Win32/SBYinYing is a potentially unwanted application (PUA) that is often bundled with certain cracked games. It may display ads to users or redirect them to potentially harmful websites, which puts it in the same line with adware and browser hijackers. Most often, user get infected with that malware after downloading cracked software. PUA:Win32/SBYinYing Overview PUA:Win32/SBYinYing […]
How to Disable Windows Defender: Windows 10 & 11 (With Safety Warnings)
Disabling Microsoft Defender is a common request from Windows users worldwide, often driven by performance concerns or conflicts with third-party security software. While Microsoft Defender has evolved into a capable security solution, there are legitimate scenarios where users need to disable it temporarily or permanently. This comprehensive guide explains safe methods to disable Windows Defender […]
Trojan:Win32/Qhosts
Trojan:Win32/Qhosts is malware that provides remote access to the target system and modifies the Hosts file. It is primarily distributed through illegal activation tools found on torrent and warez sites. While the mentioned interaction with the system configuration file as a definitive feature, it is capable of much, much more unpleasant activities. Trojan:Win32/Qhosts Overview Trojan:Win32/Qhosts […]
PUABundler:Win32/YandexBundled
PUABundler:Win32/YandexBundled is a detection of potentially unwanted application (PUA) associated with the Russian company Yandex. It is typically distributed as bundled software with repackaged or free programs. While being less dangerous than malware, it can still threaten both the privacy and normal operations of one’s computer. What is PUABundler:Win32/YandexBundled? PUABundler:Win32/YandexBundled is a generic detection name […]