Gridinsoft Security Lab
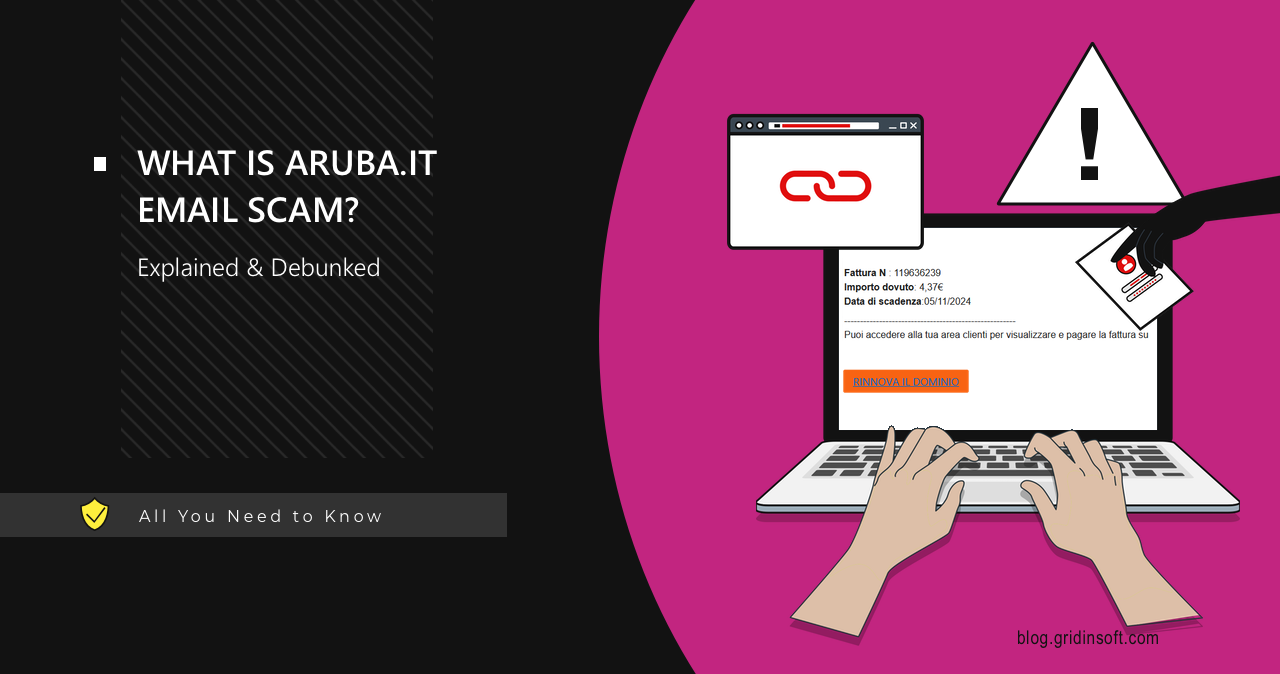
Aruba.it Email Scam
The Aruba.it email scam is a phishing campaign using fake emails that appear to be from Aruba S.p.A., a well-known Italian company providing domain and web hosting services. Scammers aim to deceive recipients by posing as Aruba and requesting urgent action, such as domain renewal, on a fake website that mimics the official aruba.it page. […]
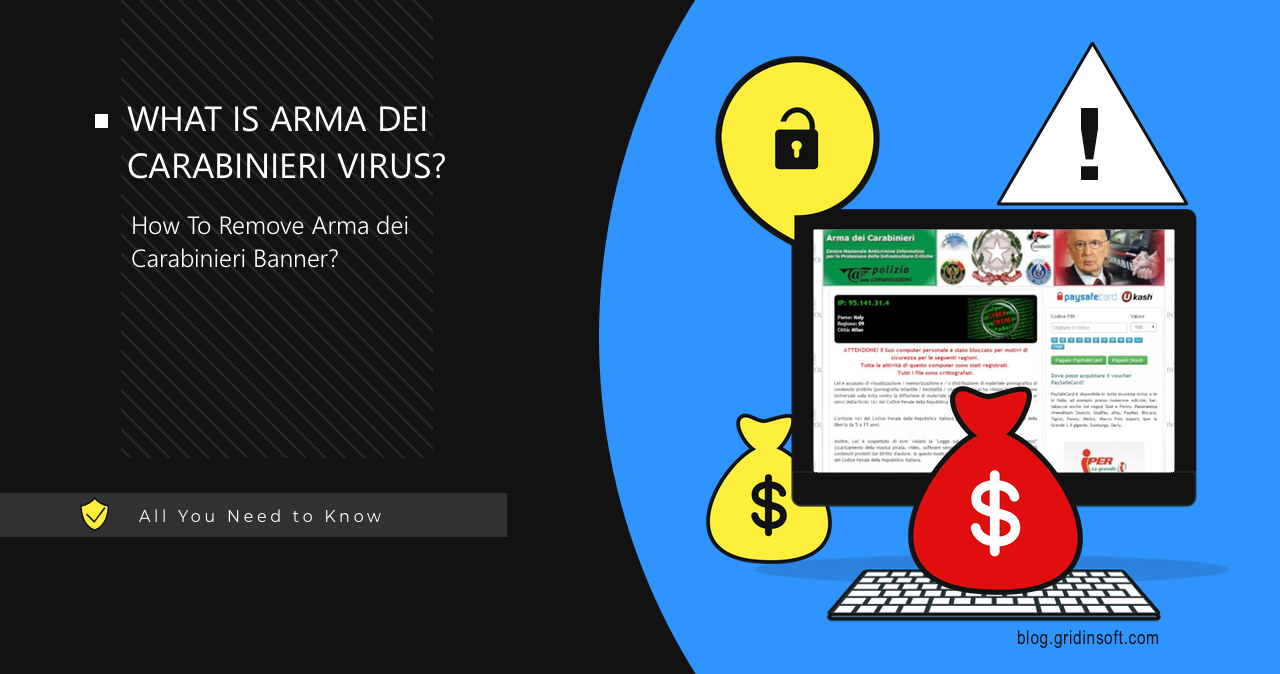
Arma dei Carabinieri Virus
The *Arma dei Carabinieri* message is a banner that may appear on your PC, attempting to mimic notifications from Italy’s national gendarmerie. Cybercriminals use their name and authority to convince users from Italy into paying a non-existent fine to unlock their computers. In this post, I will describe the principle of how this malware works […]
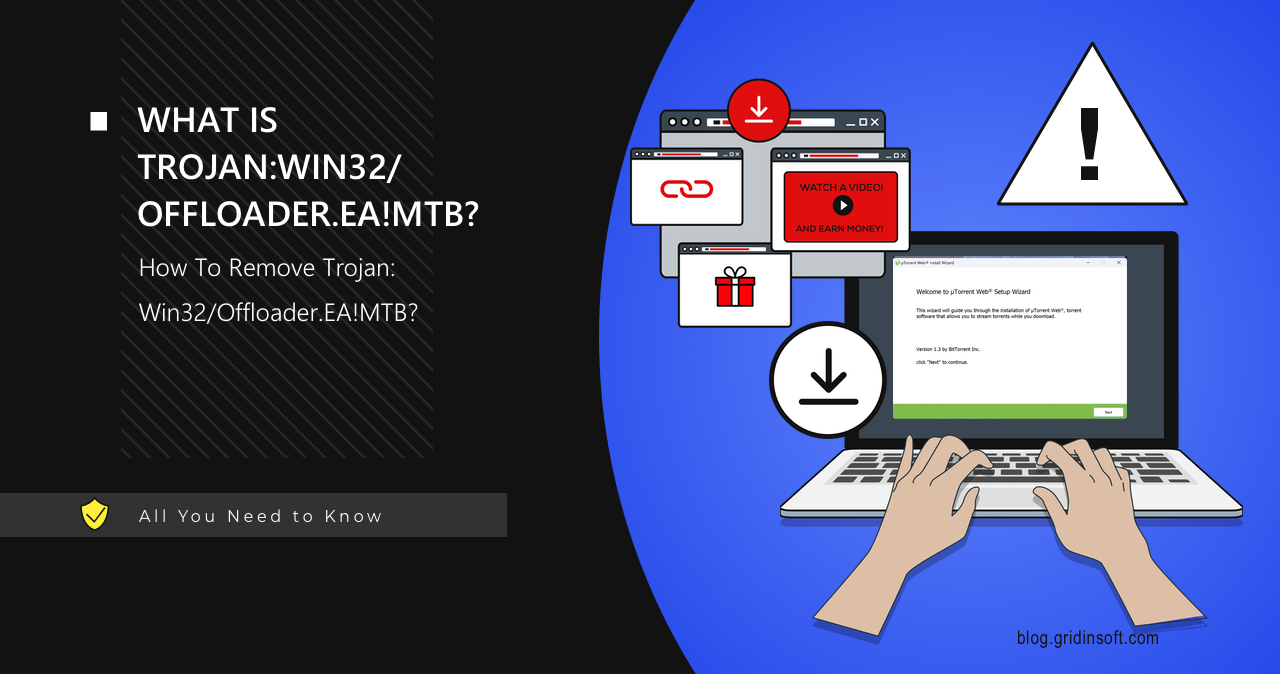
Trojan:Win32/Offloader.EA!MTB
Trojan:Win32/Offloader.EA!MTB is malware designed to establish unauthorized access to a target system or deliver a payload of additional malware. This detection is sometimes associated with uTorrent installers, and in such cases, it is more likely a false positive. Let me describe each of these cases and explain how to remove the actual threat. Trojan:Win32/Offloader.EA!MTB Overview […]
UC Browser – Is it Legit? Analysis & Verdict
While browsing the Web, you can at some point find yourself with an installer file for a program called UC Browser. This dubious program appears as a normal web browser, although it has some strange quirks to it. But in fact, it is a rather dangerous app that only looks like a web browser – […]
PUA:Win32/Webcompanion
PUA:Win32/Webcompanion is a potentially unwanted program positioned as a malicious link blocker. In fact, it modifies browser settings and installs additional unwanted software and browser extensions. The program is commonly distributed as bundled or recommended software alongside freeware programs. PUA:Win32/Webcompanion Overview PUA:Win32/Webcompanion is a Microsoft Defender detection associated with a potentially unwanted program called Adaware […]
PUA:Win32/DNDownloader
You can witness a PUA:Win32/DNDownloader detection while installing a certain software. This detection refers to a potentially unwanted software that attempts to run unwanted apps along with the “main” installation. In this article, I explain how to remove it and show the dangers related to that threat. Detection Overview PUA:Win32/DNDownloader is a heuristic detection of […]
PUABundler:Win32/MediaGet
PUABundler:Win32/MediaGet is a Russian potentially unwanted program designed for accessing pirated content. Like most similar software, it installs some unnecessary programs onto the system during installation and also turns the device into a proxy server in exchange for an ad-free experience. MediaGet Virus Overview PUABundler:Win32/MediaGet is a detection of potentially unwanted software associated with the […]
PrimeLookup Extension Removal Guide
PrimeLookup is a Chrome extension that may unexpectedly appear among your browser’s add-ons, causing your search queries to be redirected. As a browser hijacker, it poses a subtle threat to anyone who continues using the affected system. Removing this unwanted extension isn’t easy, so in this post, I’ll explain its origins and guide you through […]
Removal Guide For The ZoomFind Chrome Extension
ZoomFind is a Chrome extension that may unexpectedly appear among the others, causing the browser to redirect your search queries. It belongs to the class of browser hijackers and poses a less obvious danger to anyone who keeps using the system. Removing this unwanted extension is not an easy task, so in this post, I […]
Removal Guide For The SwiftSeek Chrome Extension
The SwiftSeek is a browser extension that may unexpectedly appear among the others, causing the browser to redirect your search queries. It belongs to the class of browser hijackers and poses a less obvious danger to anyone using the system. Removing this extension is not easy, so in this post, I will explain its origins […]
Trojan:Script/Obfuse!MSR
Trojan:Script/Obfuse!MSR is a generic detection of a malicious script that abuses command interpreters to execute commands or binaries. What distinguishes this threat from others is its emphasis on a high degree of obfuscation. In this article, I will explain how much of a danger this detection means and how to remove it. Trojan:Script/Obfuse!MSR Overview Trojan:Script/Obfuse!MSR […]
What is the Hkbsse.exe Process?
Hkbsse.exe is a name of a process related to Amadey Dropper, that you can observe while browsing through the system. This malware delivers other malware to the target system, disables security solutions and does a lot of other dirty things that harm the system pretty badly. In this article, I will explain how to remove […]