Malware is tricky. Even after running a full scan with Gridinsoft Anti-Malware, you might still experience strange behavior on your computer — slowdowns, pop-ups, or unexpected issues. Sometimes the scan shows no threats, but you’re sure something isn’t right. Other times, the scan detects something, but you’re not sure how to interpret the results.
This is where our Support Team comes in. To give you the best possible help, we need to see what’s happening on your system. The good news? Gridinsoft Anti-Malware has built-in tools that make sharing this information quick, easy, and completely transparent.
Why We Need Your System Information
Think of it like taking your car to a mechanic. They can’t just guess what’s wrong — they need to look under the hood. The same applies to computer issues. When you share your system information with us, we can see:
- What version of Windows you’re running and how it’s configured
- Which drivers and programs are installed
- What processes and services are currently active
- Details about your network setup and security software
This helps us understand why certain threats might not be detected, why files weren’t deleted, or what’s causing conflicts with other software. Without this information, we’re essentially troubleshooting in the dark.
How to Collect System Information
Gridinsoft Anti-Malware makes this process straightforward. Here’s what you need to do:
Open the program and navigate to the Tools tab. You’ll see an option called Collect system information — click on it.
The program will spend a few seconds gathering data about your PC. Everything it collects is displayed right there on your screen — no hidden uploads, no surprises. You can review every single line before deciding what to do with it.
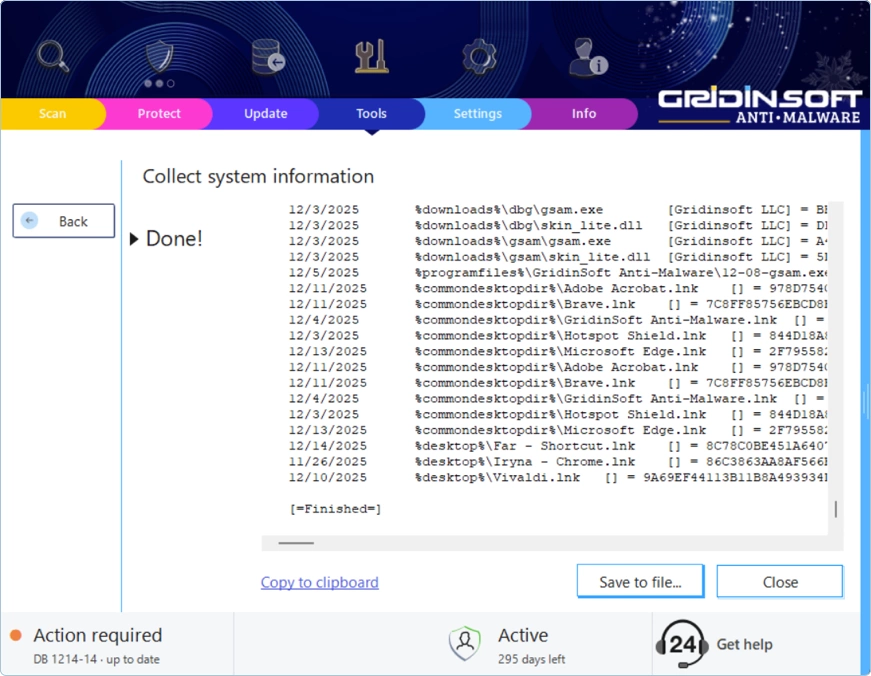
Once collection is complete, you have a few options. You can Copy to clipboard and paste the information directly into an email or support ticket. Alternatively, click Save to file… to create a .log file that you can attach to your ticket. If you change your mind, just hit Cancel and nothing gets saved.
Understanding the Different Log Files
Besides the general system information, Gridinsoft Anti-Malware maintains three types of logs that can be incredibly useful for diagnosing specific problems. You’ll find all of them in the Tools tab.
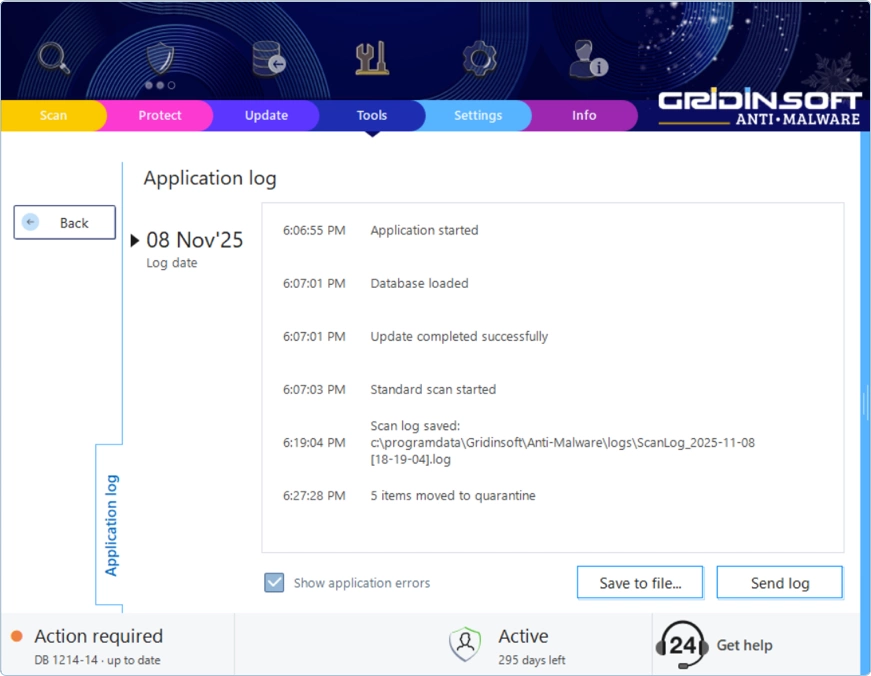
Application Log
This log tracks everything the program does — when it starts, what happens during scans, and any errors that occur. If Gridinsoft Anti-Malware crashes, freezes, or behaves strangely, the Application Log is the first place we look. It often reveals the exact moment something went wrong and why.
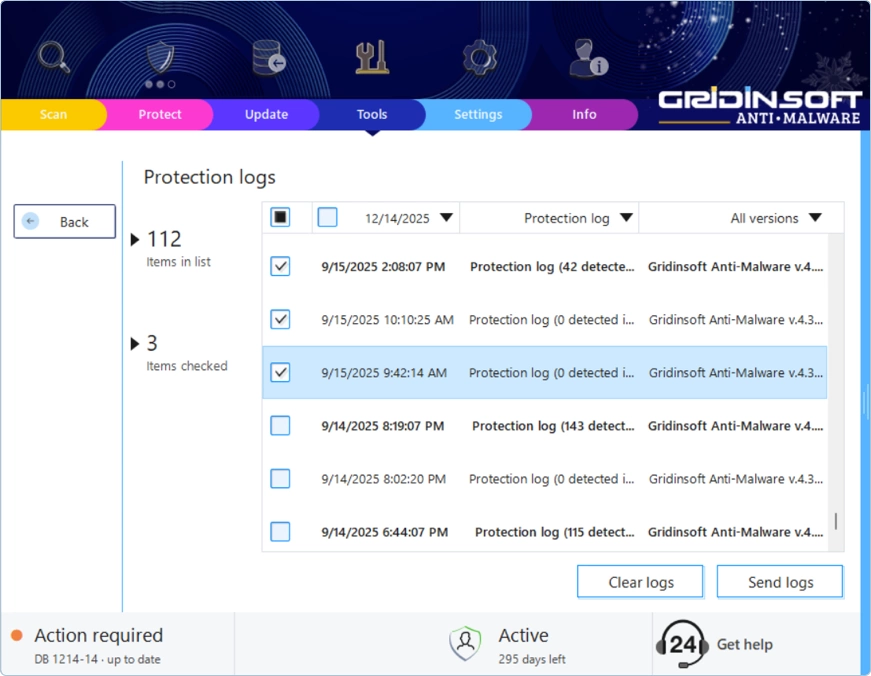
Protection Log
Running real-time protection features like Internet Security or On-Run Protection? This log records everything those guards catch (or miss). It’s particularly valuable when you suspect the protection might be conflicting with another program on your system. We can see exactly what happened and when.
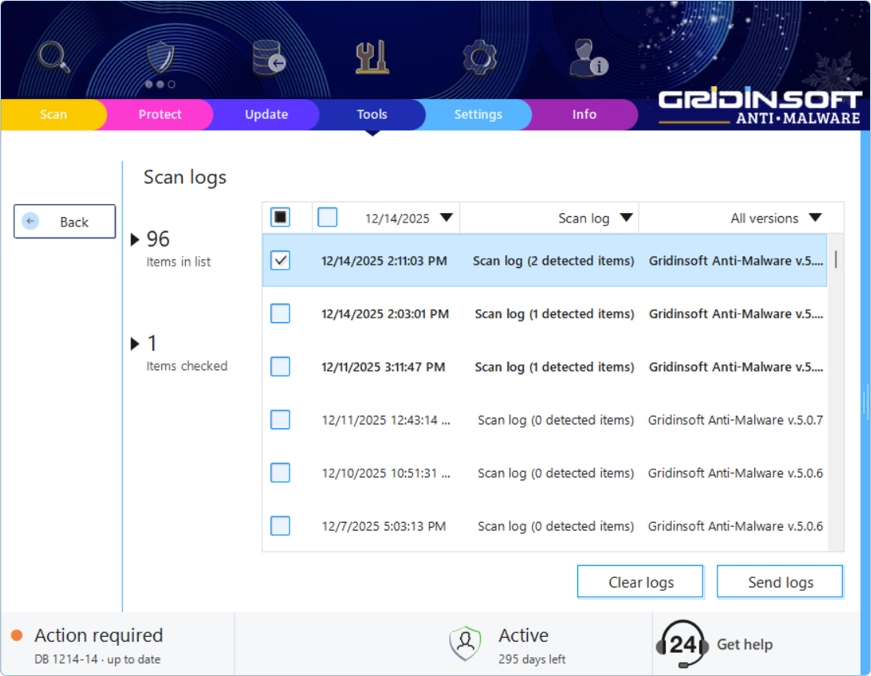
Scan Log
Every time you run a scan, the details get recorded here — the date and time, which type of scan you ran, what areas were checked, and what threats (if any) were found. If you’re wondering why a particular scan didn’t catch something, or you need to reference past scan results, this is where to look.
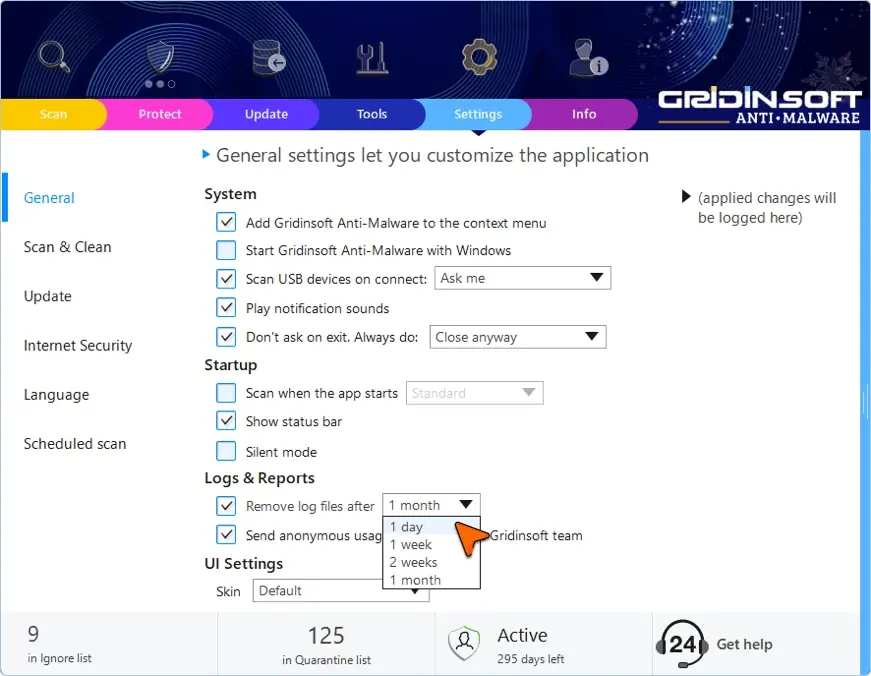
Managing Your Logs
By default, log files are stored for a certain number of days before being automatically deleted. You can adjust this in the program settings under Logs & Reports. If you’re dealing with an ongoing issue, consider turning off automatic deletion so you don’t lose important historical data.
Your Privacy Is Protected
We understand that sharing system information might feel uncomfortable. That’s why Gridinsoft designed this feature with transparency in mind. The collected data includes only technical details needed for troubleshooting:
- Windows version and build number
- Installed drivers and their versions
- Running processes and services
- Startup programs
- Network adapter information
- Gridinsoft Anti-Malware version and configuration
- Other security software detected on your system
What we don’t collect: your personal documents, saved passwords, browser history, emails, chat messages, or financial information. The data you send us is purely technical — nothing personal leaves your computer.
Getting the Most Out of Your Support Ticket
When you reach out to our support team, including the right information from the start can dramatically speed up the resolution process. Along with your system information and relevant logs, try to include:
- A clear description of the problem — error messages, symptoms, what you expected vs. what actually happened
- When the issue started — did it begin after a Windows update? A new program installation? A driver change?
- What you’ve already tried — restarting, reinstalling, running different scan types
- Your order ID or license email — helps us locate your account quickly
The more context you provide, the faster we can identify the problem and get you back to a clean, smoothly-running computer.



