The Cereals IoT botnet appeared in 2012, and reached its peak in 2015, when there were about 10,000 infected devices. All these eight years, the Cereals botnet only downloaded anime for its creator.
All this time, Cereals exploited only one vulnerability and attacked D-Link’s NAS and NVR, combining them into a botnet.
For many years, the botnet has eluded the attention of information security professionals, and now it has almost ceased to exist.
“The fact is that the vulnerable D-Link devices on which Cereals parasitized began to become obsolete and out of order, that is, they are becoming smaller and smaller. In addition, the ransomware Cr1ptT0r accelerated the decay of the botnet, which destroyed the competing malware on infected devices and removed the Cereals malware from many D-Link devices in the winter of 2019”, — say Forcepoint researchers.
Now, as the botnet and the vulnerable devices that it has exploited are disappearing, Forcepoint experts decided to publish a report on the activities of the malware, because they can no longer be afraid that the study will draw the attention of other criminals to vulnerable devices and provoke the emergence of new botnets.
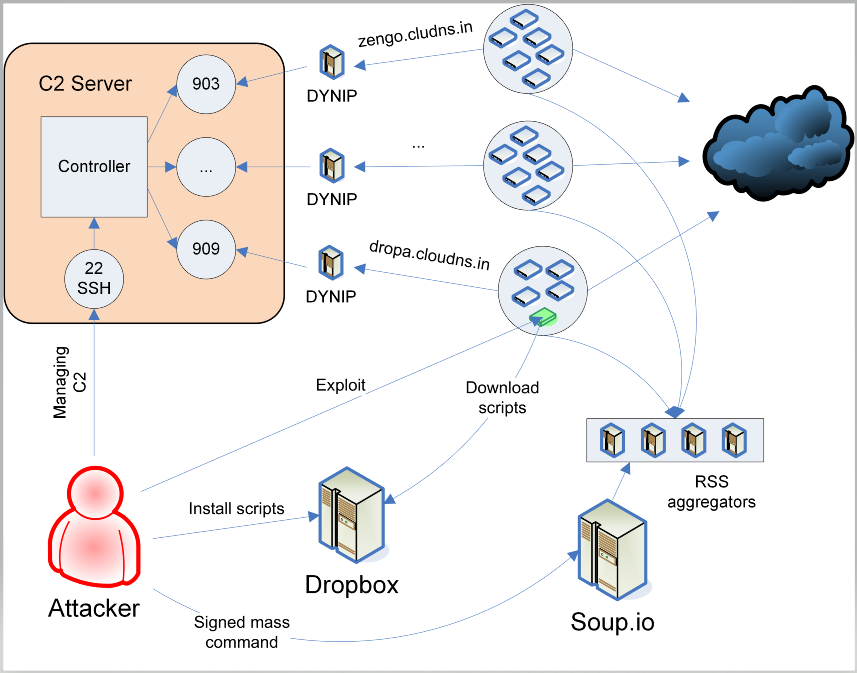
Experts write that Cereals can be called a unique phenomenon, since the botnet used only one vulnerability throughout all eight years of its “life”.
This vulnerability was related to the SMS notification feature that was present in the D-Link NAS and NVR firmware. The bug allowed the creator of Cereals to send malicious HTTP requests to the embedded servers of vulnerable devices and execute commands with root privileges. In this way, the botnet operator infected the devices with its malware.
“The botnet was very advanced in its functionality. Therefore, if the attack succeeded, Cereals supported up to four active backdoors on the devices, tried to patch the attacked devices so that other attackers could not attack them, and distributed bots on 12 small subnets”, – say the researchers.
However, all these efforts, in fact, were a waste of time. Forcepoint analysts believe that Cereals was someone else’s hobby or a project created as a joke (it is assumed that the author of the malware is called Stefan and he lives in Germany).
The fact is that the botnet did not engage in DDoS attacks, did not try to attack any other devices other than the above, did not try to access user data stored on infected devices. Instead, all these years Cereals just methodically downloaded anime.
However, this is the cutest botnet I talked about on this blog – others are mostly not like that, for example, read an article about Hoaxcalls botnet, that attacks Grandstream devices.




