Experts warned that an exploit for two high-profile vulnerabilities in Microsoft Exchange, which are collectively called ProxyNotShell, has appeared in the public domain.
Vulnerabilities have been used by hackers before, but now there may be more attacks.
Initially, ProxyNotShell problems (CVE-2022-41040 and CVE-2022-41082) were discovered in September by analysts from the Vietnamese company GTSC. Let me remind you that the bugs affected Microsoft Exchange Server 2013, 2016 and 2019 and allowed attackers to elevate privileges to run PowerShell in the system context, as well as achieve remote code execution on a compromised server.
As Microsoft soon confirmed, hackers have already exploited these problems. Experts wrote that at least one group used bugs against about 10 companies around the world.
Let me remind you that we also reported that US and UK accused China for attacks on Microsoft Exchange servers.
The interest in ProxyNotShell turned out to be so great that experts kept almost all the technical details of the vulnerabilities secret (so that even more attackers would not exploit them). However, scammers did not fail to take advantage of this situation and started selling fake exploits for ProxyNotShell online.
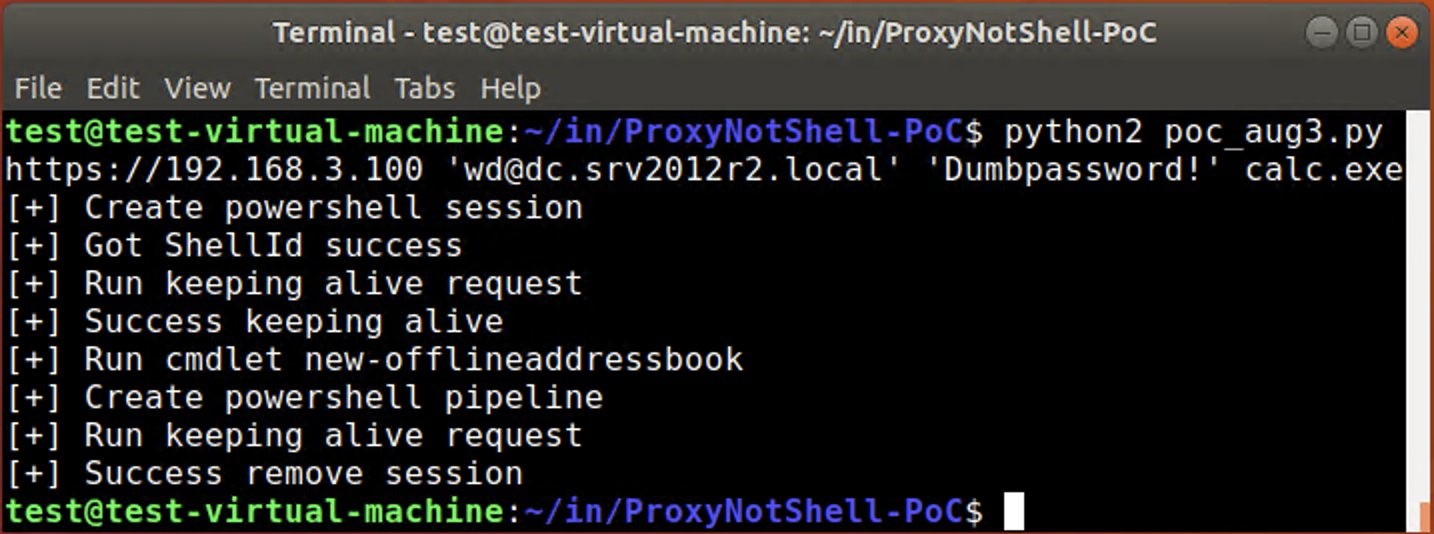
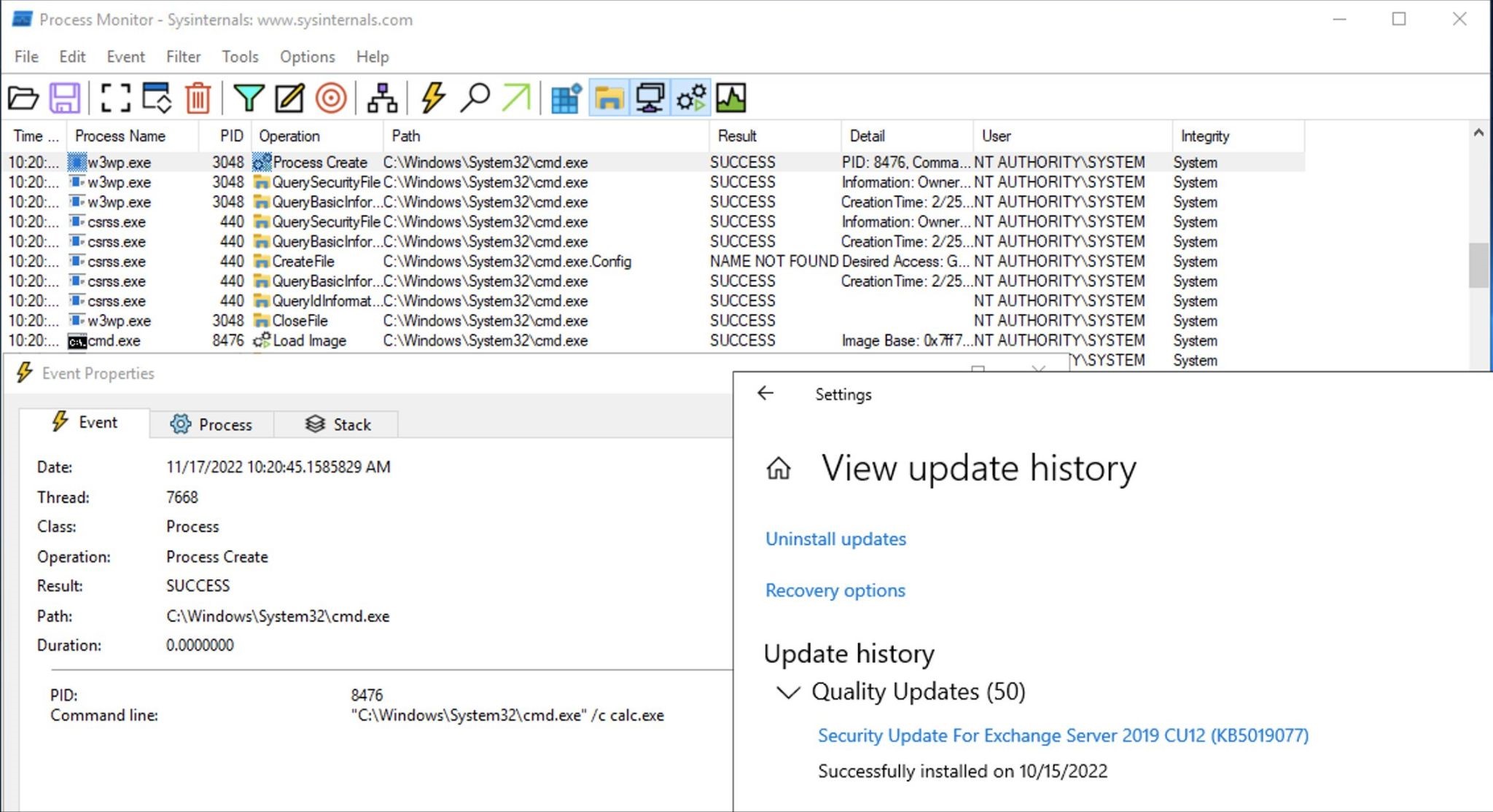
Now, after the vulnerabilities have finally been fixed (with the release of the November updates), the information security researcher known by the nickname Janggggg has published a PoC exploit that the attackers used to attack Exchange servers in the public domain.
The authenticity and operability of this exploit has already been confirmed by a well-known information security specialist and analyst at ANALYGENCE, Will Dormann. He said that the exploit works against systems running Exchange Server 2016 and 2019, but the code needs some work before attacks on Exchange Server 2013.
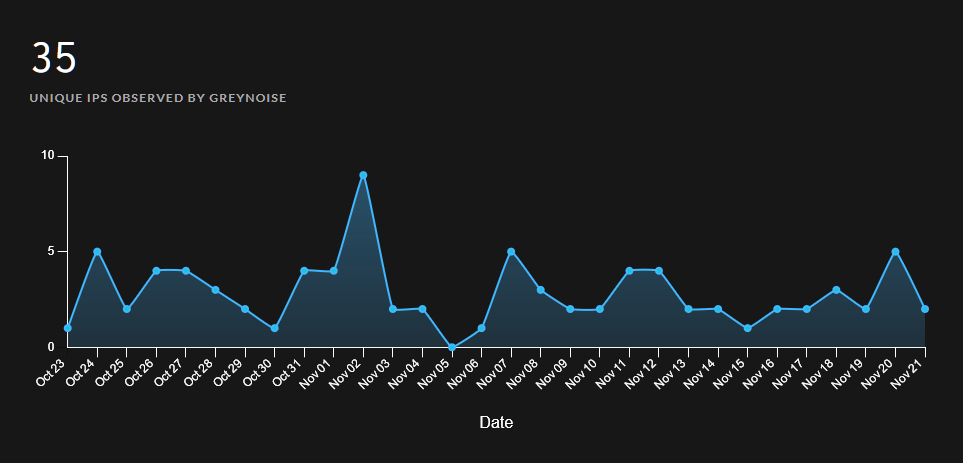
According to researchers at Greynoise, who have been tracking ProxyNotShell usage since late September, the vulnerabilities are still being attacked, and there may be more of them after the exploit is published.
Let me remind you that attackers use bugs to deploy China Chopper web shells on compromised servers in order to gain a foothold in the system, steal data, and also organize lateral movement in the networks of victims.




