A decryptor for a Donex ransomware, also known under the name of Muse, DarkRace and LockBit 3.0, has been released by Avast specialists. They used a flaw in the cipher known for almost half a year to help with decryption privately, and now make the decryptor tool available to everyone. This is yet another ransomware family that has become decryptable since the beginning of 2024.
Donex a.k.a Muse/DarkRace/LockBit 3.0 Decryptor Released
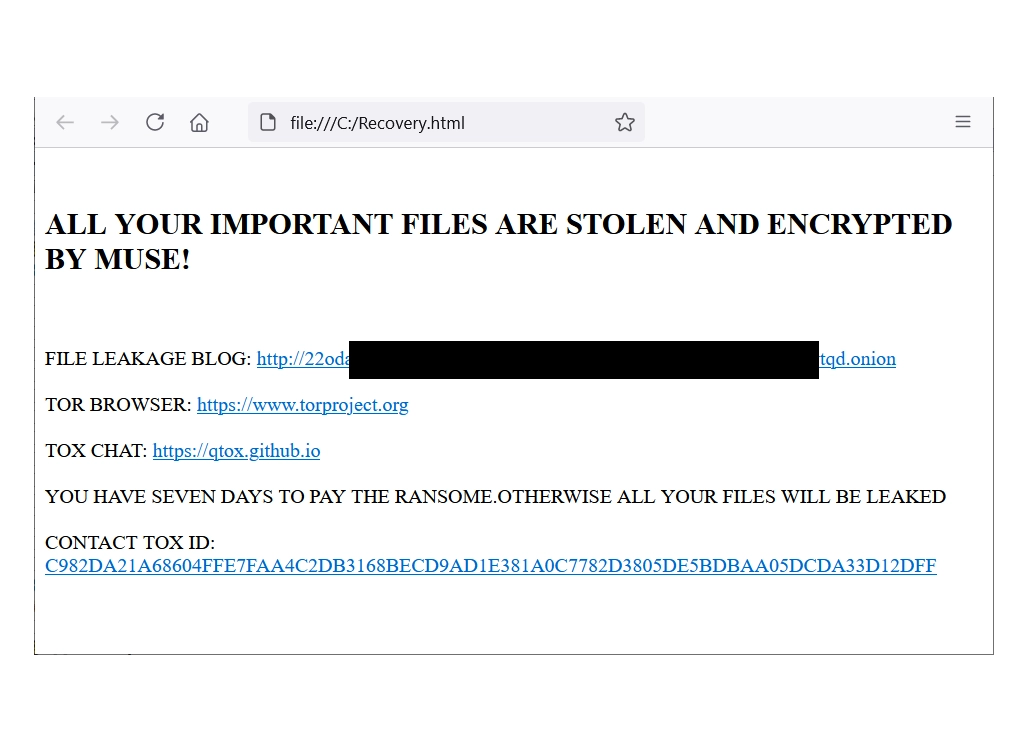
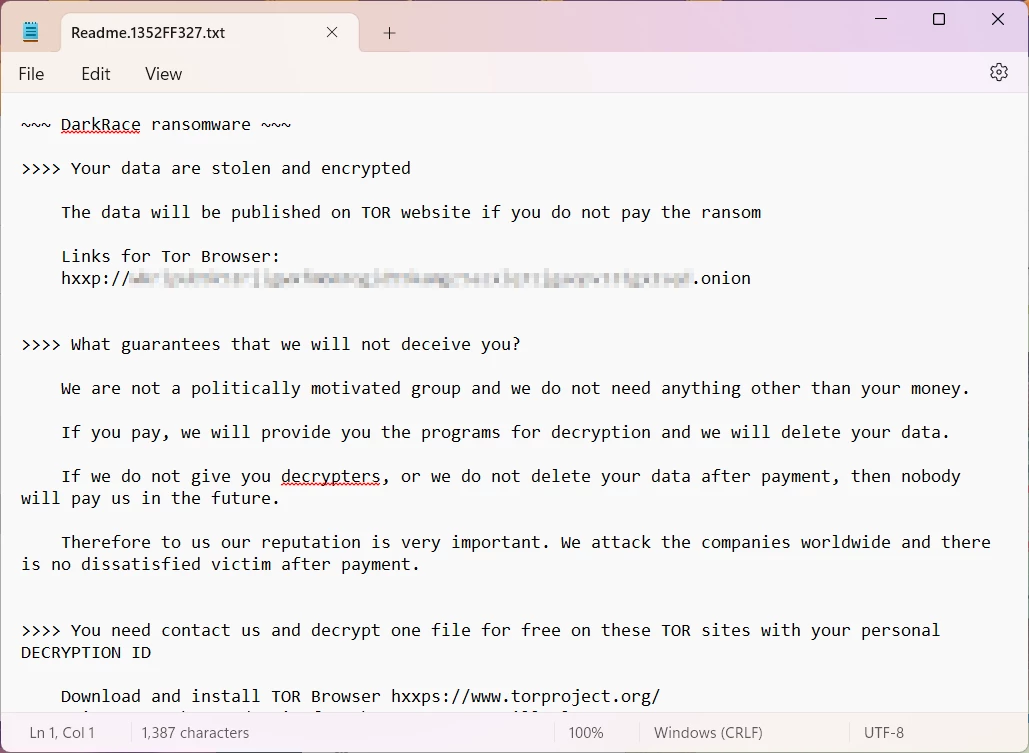
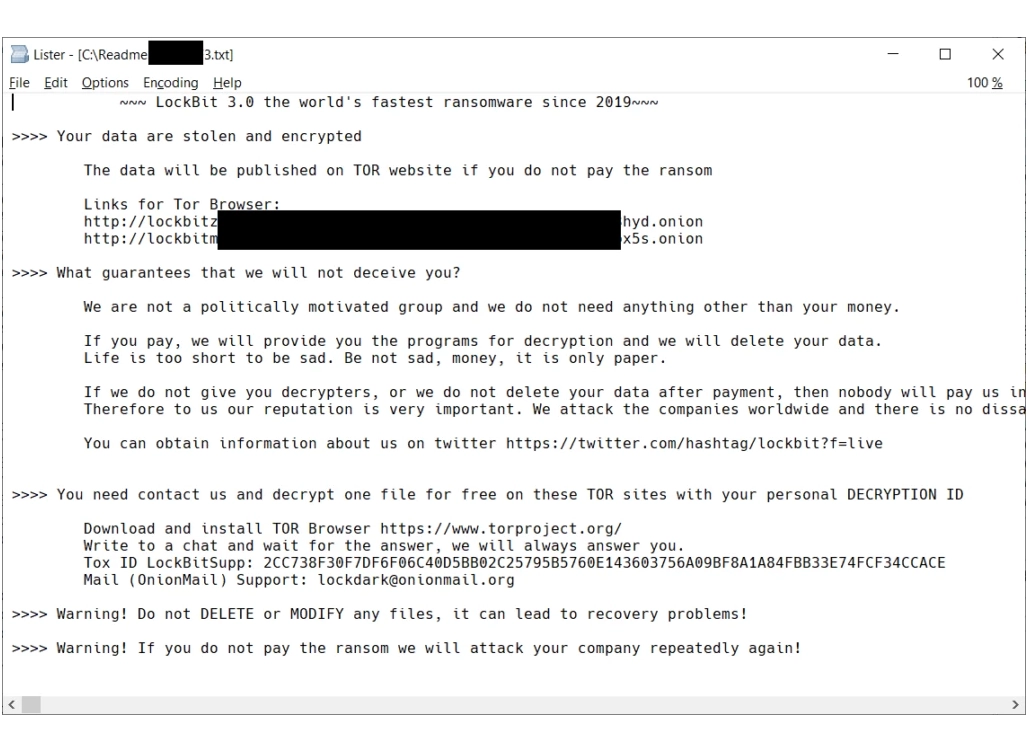
On July 8 2024, researchers from Avast Decoded published a decryptor tool for DoNex ransomware. This malware family has been active since April 2022, originally bearing the name “Muse ransomware”. In November of the same year, they started mimicking the LockBit 3.0 ransomware, following the leak of the builder tool of this infamous malware. About half a year later, the threat actor opted for the name DarkRace, which changed once again in March 2024 to Donex ransomware. That March rebranding appears to be the last in the group’s existence, as no new samples appear since May of that year. And now, all its victims will get their files back to normal without paying a copper.
For almost half a year, since March 2024, Avast had the decryptor on hand, using it without public disclosure. This allowed them to save money for quite a few companies that fell victim to the malware, while the hackers had no clue that something was going on. But now, a few months past the last sign of Donex ransomware activity, they decided to make the decryptor public. The entire case of having the effective and working decryption solution is possible due to the flaw present in the ransomware encryption mechanism.
Why didn’t they just make it public as soon as they discovered that flaw? Well, that would have given the hackers a clue about where exactly there has been a vulnerability, leading to it being patched, which would consequently render the decryptor useless. What cybercriminals have seen instead is a slow-but-steady decrease in the number of victims that have paid the ransom. And even though this may be a clue itself, there’s no guidance on where the issue is exactly.
How do I use the decryptor?
The program that the researchers released has a friendly interface that is not hard to deal with even for an ordinary user. After downloading it from the developers’ website, one will see an interface with detailed description for each step to come through. The only requirement is to have a so-called file pair: a version of a file in an encrypted and “normal” state. This would allow the tool to figure out the decryption key.
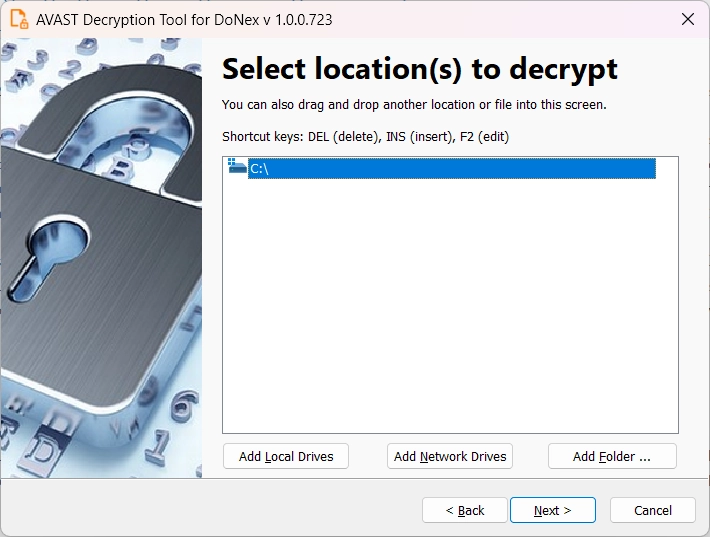
Once this manipulation with the key is complete, the program will automatically proceed with the rest of the files. Time elapsed for this procedure depends on the amount of files, and, obviously, the system’s calculation power. Unfortunately, there is no mass-decryption tool that will allow lifting the encryption from the entire network, for example. Still better than nothing though, especially considering that the frauds are no longer active and will likely ignore even genuine contacts for payment or negotiations.
The decryptor for one more ransomware is yet another reason to emphasize: you should never pay the hackers. Sooner or later, there will be a solution that will manage to get your files back. For now, make your infrastructure protected and always have a backup stored in a reliable place.