Attackers are actively exploiting a critical vulnerability in the Docker Engine that may allow for authentication bypass in a chain attack. This vulnerability allows attackers to bypass AuthZ authorization plugins, effectively mutilating any auth control. For this and several other reasons, the flaw got the max severity score possible (10.0).
Critical Docker Engine Flaw Allows Attackers to Bypass Authorization Plugins
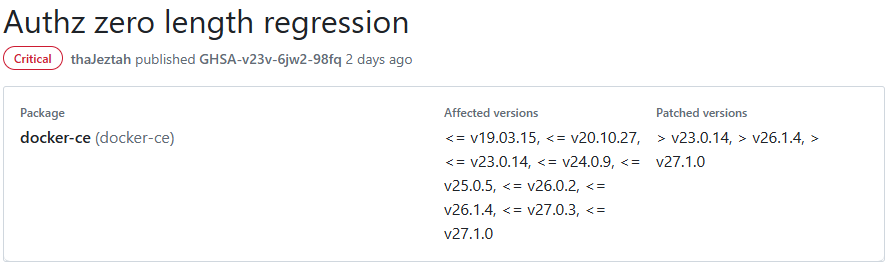
Docker has reported a critical vulnerability in a selection of versions of their Docker Engine. This vulnerability enables threat actors to bypass authorization plugins (AuthZ) under specific conditions. The vulnerability in question is CVE-2024-41110, rated at CVSS score: 10.0.
The “predecessor” of this flaw in fact appeared back in 2018, and patched in January 2019. However, in April 2024, the flaw re-surfaced in modern versions of the software suite. The developers explain that this happened because they have missed to transfer the fixes to newer versions of the program.
In summary, CVE-2024-41110 allows attackers to send a specially crafted API request with a Content-Length of 0, tricking the Docker daemon into bypassing the AuthZ plugin. Typically, API requests contain a body that the authorization plugin checks to make access control decisions. When the Content-Length is set to 0, the plugin receives the request without a body, preventing proper validation and potentially leading to the approval of unauthorized actions, including privilege escalation.
And that explains the max CVSS score. Authentication bypass vulnerabilities are as bad as RCE/ACE ones, and may have similar application areas. Adversaries can easily use them to gain initial access, or perform lateral movement. At the very least, frauds can access the data stored on Docker and leak it to someone on the outside.
Risk Group & Vulnerability Patches
As for the potential risks, the versions at risk include Docker Engine v19.03.x and later versions that use authorization plugins for access control decisions. Ones who do not run any auth plugins should be safe from any attacks of that vector. Additionally, there is a limited risk for Docker Desktop users up to version 4.32.0. However, for this to be exploited, the threat actor must have local access to the host machine, or the Docker daemon must be insecurely exposed via TCP.
On the other hand, versions of Engine suite, commercial products of the developer, and internal infrastructure that do not rely on authorization plugins for access control decisions, as well as users of all versions of Mirantis Container Runtime, are not vulnerable.
Docker devs have released an update (docker-ce v27.1.1) that fixes the flaw, and strongly recommend that users update Docker Engine. If the update cannot be applied for some reason, the developers recommends at least to disable AuthZ plugins until the update can be applied.