Cybercriminals are running a two-pronged attack targeting both travelers and hotel staff through the Booking.com platform, according to security research and incident reports from affected organizations.
The campaign hits travelers by compromising hotel booking systems to steal money, while targeting hotel staff with fake CAPTCHA websites that install malware. The attack exploits trust in booking platforms.
How the Traveler Scam Actually Works
Security researchers documented a case involving Robert Woodford, a recruitment marketing specialist who got burned while booking a hotel in Verona through Booking.com.
After completing a booking, Woodford received what looked like an official message through Booking.com’s messaging system asking for “missing details” and a prepayment. The message appeared in the same thread as his previous hotel communications, and the payment link contained “bookingcom” in the URL.
Here’s the kicker: the hotel’s booking system had been compromised. This gave cybercriminals access to guest data and payment information. They could impersonate hotels using messaging platforms. They communicated directly with customers through official channels and manipulated payment processes within trusted systems.
Woodford logged into Booking.com directly rather than clicking links, but he still found the same fraudulent message in the official system. The payment link appeared legitimate because it contained booking-related terms in the URL structure. He only realized the merchant’s name was incorrect after making the payment.
Meanwhile, Hotel Staff Get Hit Too
While travelers are getting scammed, cybercriminals are hitting hospitality staff with fake Booking.com emails and CAPTCHA websites.
Hotel staff receive convincing fake Booking.com emails about new reservations. The emails contain booking details with check-in dates just days away, creating urgency. Staff are told to copy and paste a URL into their browser. The URL leads to a fake CAPTCHA website asking for “verification”. The fake verification tells users to press Windows Key + R, then Ctrl + V, then Enter. This sequence runs malicious code that infects systems with information stealers or trojans.
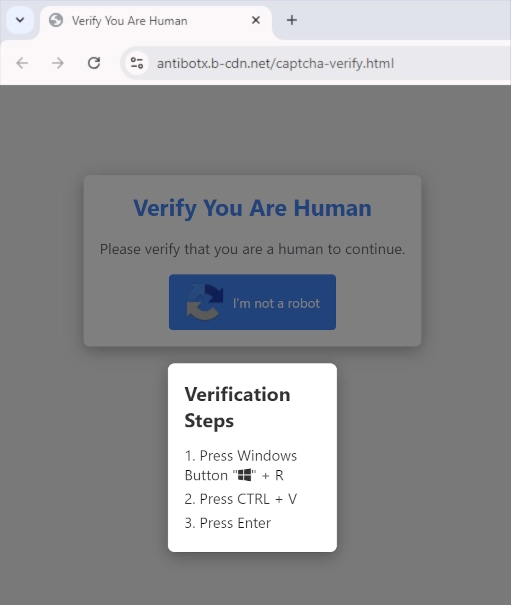
The fake CAPTCHA sites use Windows clipboard manipulation to execute PowerShell commands without users realizing what’s happening. The commands download and install malware that can steal browser credentials, cryptocurrency wallet data, and email accounts. This technique exploits the widespread use of fake CAPTCHA sites to spread malware.
Industry Response and Real Incidents
The Swiss National Cyber Security Centre (NCSC) has reported similar attacks where hotel staff were tricked into installing malware through fake CAPTCHAs and malicious clipboard commands.
Arcona Hotels & Resorts, a German company operating leisure and boutique hotels, discovered “technical irregularities” and disconnected several locations from central IT services. They brought in ResponseOne GmbH, an IT forensics specialist, to handle the situation. The company operates properties focusing on leisure and holiday hotels, boutique hotels, and 5-star properties across Germany.
The timing suggests a connection to the broader campaign targeting hospitality infrastructure, though Arcona hasn’t released details about what type of attack they experienced or whether customer data was compromised.
What Makes These Attacks Work
The coordinated nature shows a threat actor with social engineering skills for creating convincing fake booking emails and payment systems. They have technical infrastructure for hosting fake CAPTCHA sites and payment processing systems. They understand how hotels and booking platforms work. They’re targeting multiple hotels and platforms at once.
The attacks exploit trust between hotels, booking platforms, and travelers, turning communication channels into fraud vectors. The attackers use the booking platform’s own messaging system, making detection harder because the communications appear to come from verified sources.
The fake CAPTCHA component targets hotel staff who handle bookings daily and are trained to respond quickly to reservation requests. The urgency created by check-in dates just days away pressures staff to act without verifying the requests through alternate channels.
Why This Matters
These attacks hit the hospitality industry because they compromise trusted booking platforms and create financial losses for hotels and travelers. They damage trust in online booking systems and give attackers access to customer data. The stolen data enables follow-up attacks using credentials.
The two-sided approach lets attackers profit from both ends while maintaining access to compromised systems. Once inside a hotel’s booking system, criminals can monitor future reservations and target additional guests with payment scams.
The hospitality industry processes millions of booking transactions daily, making it a target for cybercriminals seeking financial gain and customer data. Hotels often use integrated systems that connect reservation platforms, payment processing, and customer communications, creating multiple attack surfaces.
If You Think You’re Compromised
Immediately disconnect affected systems from networks to prevent further data exfiltration or lateral movement by attackers. Contact law enforcement and cybersecurity specialists who can help with incident response and forensic analysis.
Notify affected customers and booking platforms about potential data exposure, following breach notification requirements in your jurisdiction. Preserve evidence for forensic analysis by avoiding changes to affected systems until specialists can examine them.
Implement temporary manual processes for critical operations while investigating the extent of the compromise and rebuilding affected systems with updated security controls.
The Technical Details
The fake CAPTCHA websites use domain names that mimic booking platforms and employ HTTPS certificates to appear legitimate. The malicious PowerShell commands typically download additional payloads from command-and-control servers hosted on compromised websites or cloud platforms.
The clipboard manipulation technique works because Windows automatically copies text when users select and copy URLs from emails. The fake CAPTCHA instructions trick users into pasting and executing this content through the Windows Run dialog, bypassing browser security protections.
Information stealers installed through these attacks typically target browser stored passwords, cryptocurrency wallet files, email client credentials, and two-factor authentication backup codes. The stolen data gets sold on darknet markets or used for additional attacks against the victims’ other accounts.
Bottom Line
The coordinated attacks targeting Booking.com users and hospitality staff show how cybercriminal operations are getting more sophisticated. The multi-vector approach demonstrates the evolving nature of these threats.
Both travelers and hospitality organizations need to adapt their security practices. These attacks show the need for verification procedures, staff training, and incident response capabilities.
The hospitality industry faces the challenge of maintaining customer trust while implementing stronger security without compromising user experience. How the industry responds to this campaign may well define cybersecurity standards for travel in the years ahead.
Organizations dealing with similar attacks should consider deploying security solutions like information stealer detection tools and conducting thorough system audits to identify potential compromises.