Danish researchers have published a report on the Cable Haunt vulnerability that threats millions of cable modem with Broadcom chips.
According to experts, the problem threatens more than 200 million cable modems only in Europe. Moreover, it is impossible to determine the exact number of vulnerable devices, because the vulnerability was found in the reference software, which, most likely, was copied by many cable modem manufacturers.
“The exploit is possible due to lack of protection in proper authorization of the websocket client, default credentials and a programming error in the spectrum analyzer. These vulnerabilities can give an attacker full remote control over the entire unit, and all the traffic that flows through it, while being invisible for both the user and ISP and able to ignore remote system updates”, — write Lyrebirds ApS researchers.
The vulnerability is associated with one of the standard components of Broadcom chips, which is called a spectrum analyzer. It protects the device from signal surges and interference and often used by Internet service providers to debug a connection.
Researchers write that the spectrum analyzer does not have protection against attacks such as DNS rebinding, and contains a vulnerability in the firmware (this is especially true with default credentials). Moreover, the component itself is available only on the internal cable modem network, but not directly via the Internet.
Therefore, implementation of the attack is actually very difficult, moreover, in the end the attacker will need to direct the user to a malicious web page in order to use the browser to operate the vulnerable component.
However, in case of success an offender will be able to:
- Change the default DNS server;
- Conduct remote man-in-the-middle attack;
- Instantly and completely replace the code or firmware;
- Download, install and update firmware without user’s awareness;
- Disable the firmware update by the provider;
- Change the configuration file and settings;
- Get and set SNMP OID values;
- Change all MAC addresses;
- Change serial numbers;
- Operate the device in a botnet.
Considering pervasiveness of the problem, experts were not able to test all possible devices for vulnerabilities to Cable Haunt, but the tests, of course, were conducted, and their results can be seen in the table below.
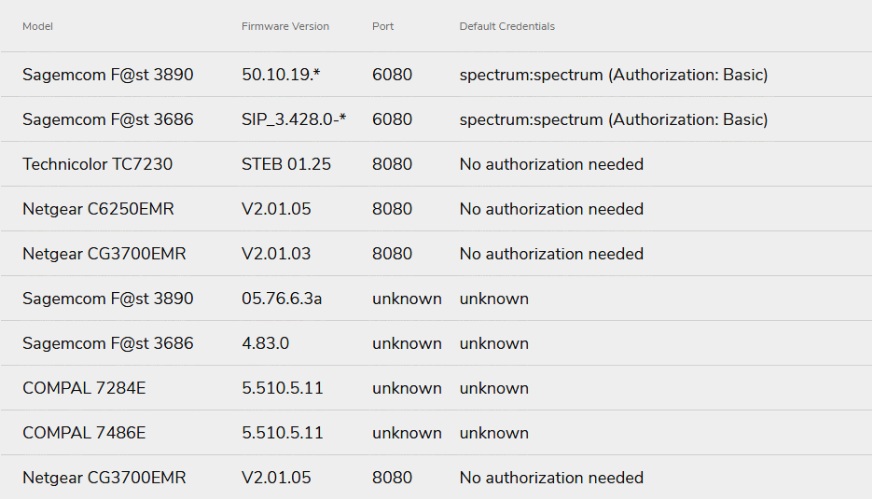
Additionally, experts have already published a PoC exploit, which providers can use to test their devices.
Don’t trust your modem anymore? Take a look at your smartphone too! Recently, researcher demonstrated how he could hack an iPhone using only one vulnerability.




