Tips For You To Recognize Fake Hacking
Fake hacking is a provocation or hacking that presupposes and notifies that…
Is It Safe to Use a Password Manager in 2022?
What’s the Idea Behind Password Managers? In the cybersecurity world, everyone knows…
Dangerous Injection Attacks
Today, Injection attacks are a significant problem and top the list of…
Chinese Hacker Group Revealed after a Decade of Undetected Espionage
The New Chinese Spying Threat Actor Identified SentinelLabs, an American cybersecurity company,…
Joint Operation: SSNDOB Personal Data Darknet Market Seized
What SSNDOB Was Before Its Servers Were Seized The US Department of…
Beware: New SpaceX Bitcoin Giveaway Scam
Crooks Make Elon Musk a Bait for Wannabe Cryptotraders Scammers again use…
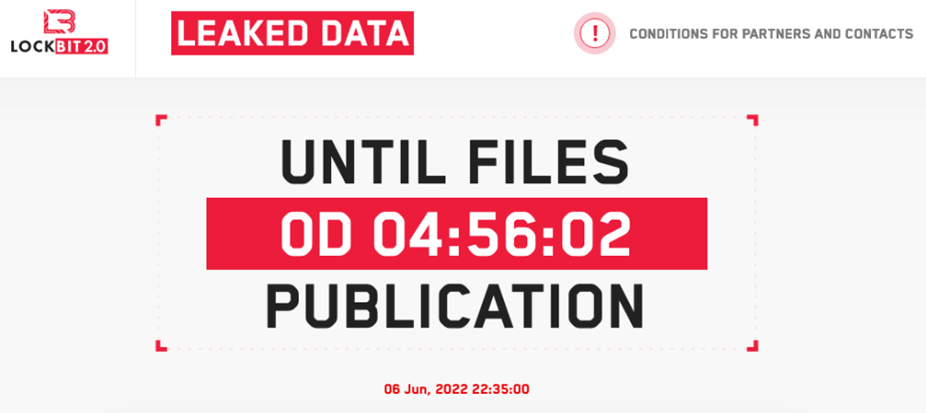
LockBit 2.0 Promises to Leak Mandiant Data
LockBit 2.0 announcement: real thing or vengeful trolling? On June 6, on…
11 Types of Spoofing Attacks
Spoofing is a kind of cybercrime in which attackers impersonate a trusted…
Attackers Exploit MSDT Follina Bug to Drop RAT
Security specialists caution users about the exploitation of the recently disclosed Follina…
New Cuba Ransomware Variant Involves Double-Extortion Scheme
What's new in April Variant of Cuba Ransomware The Cuba ransomware family…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet users. This…
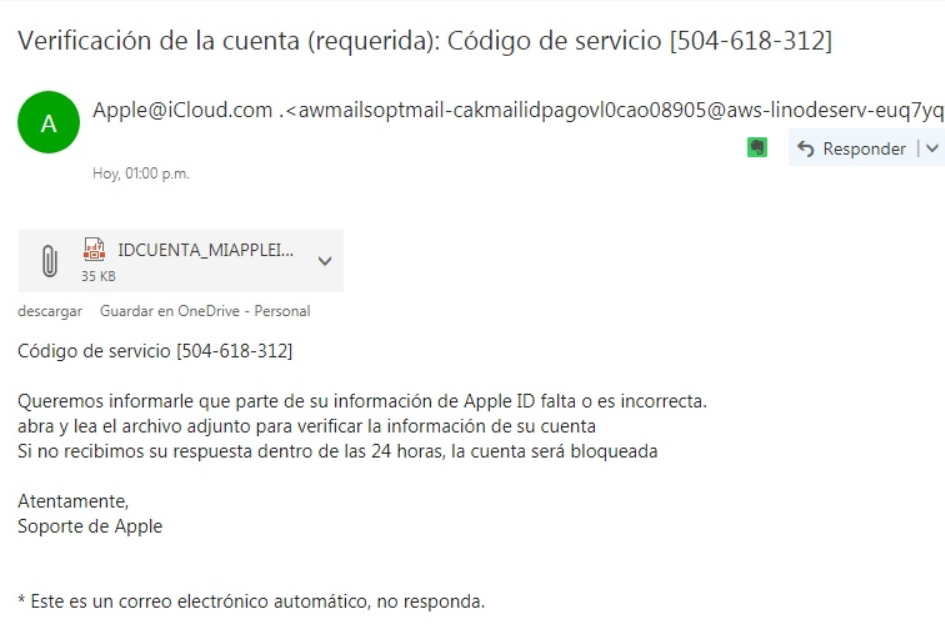
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several Spanish-speaking countries…