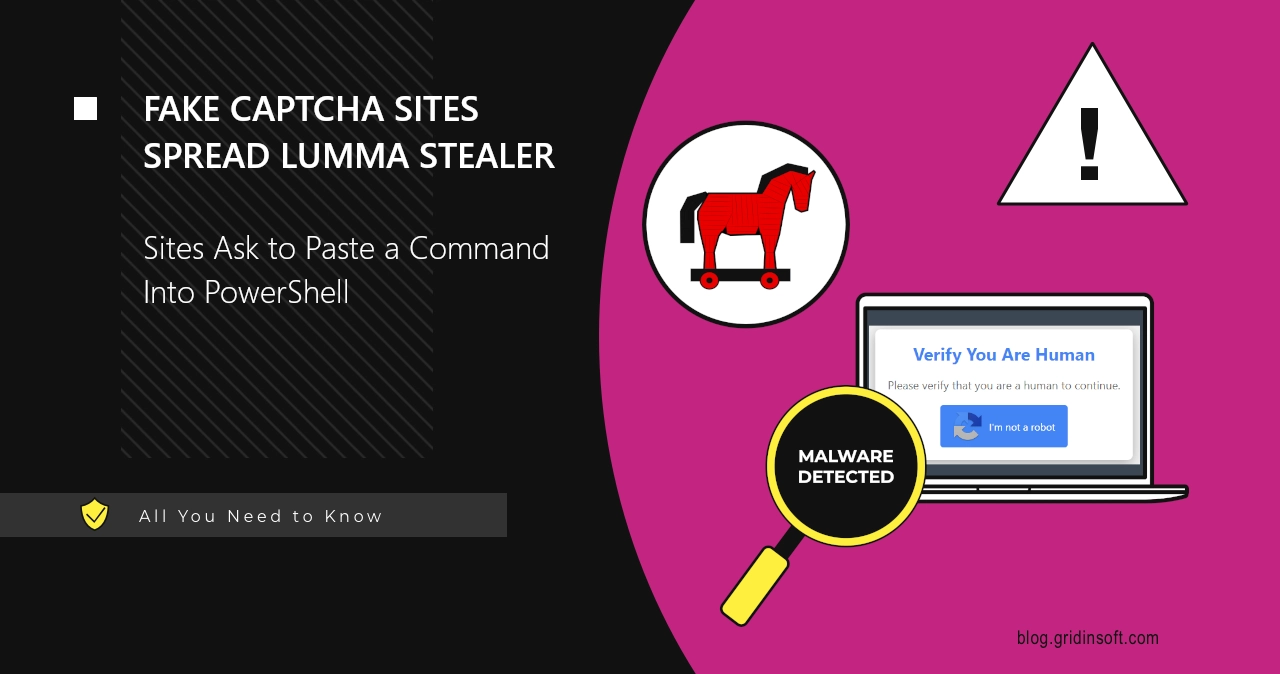
Fake CAPTCHA Sites Trick Users to Run Malicious Code, Install Lumma Stealer
New malware spreading campaign now picks up steam on the Internet, luring…
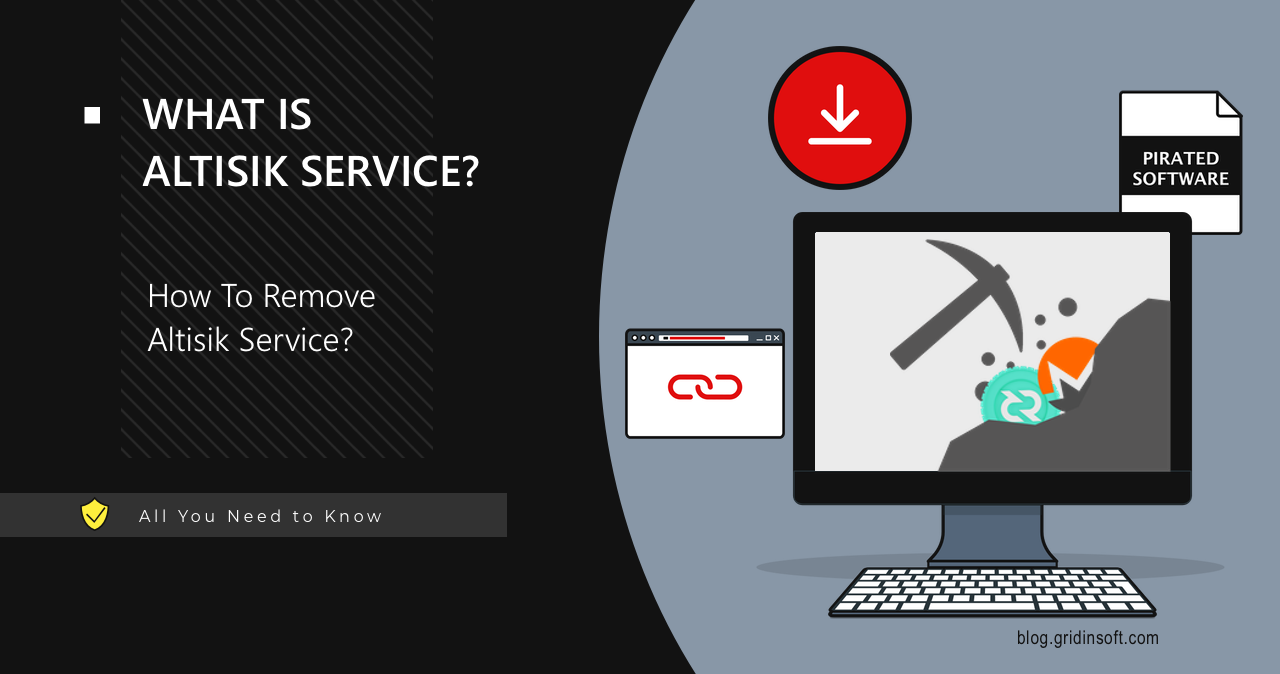
Altisik Service Virus Analysis & Removal
Altisik Service is a malicious coin miner that usually installs and runs…
What are Facebook Job Scams and How to Avoid Them?
Facebook job scams are a relatively recent but fast-growing type of scam…
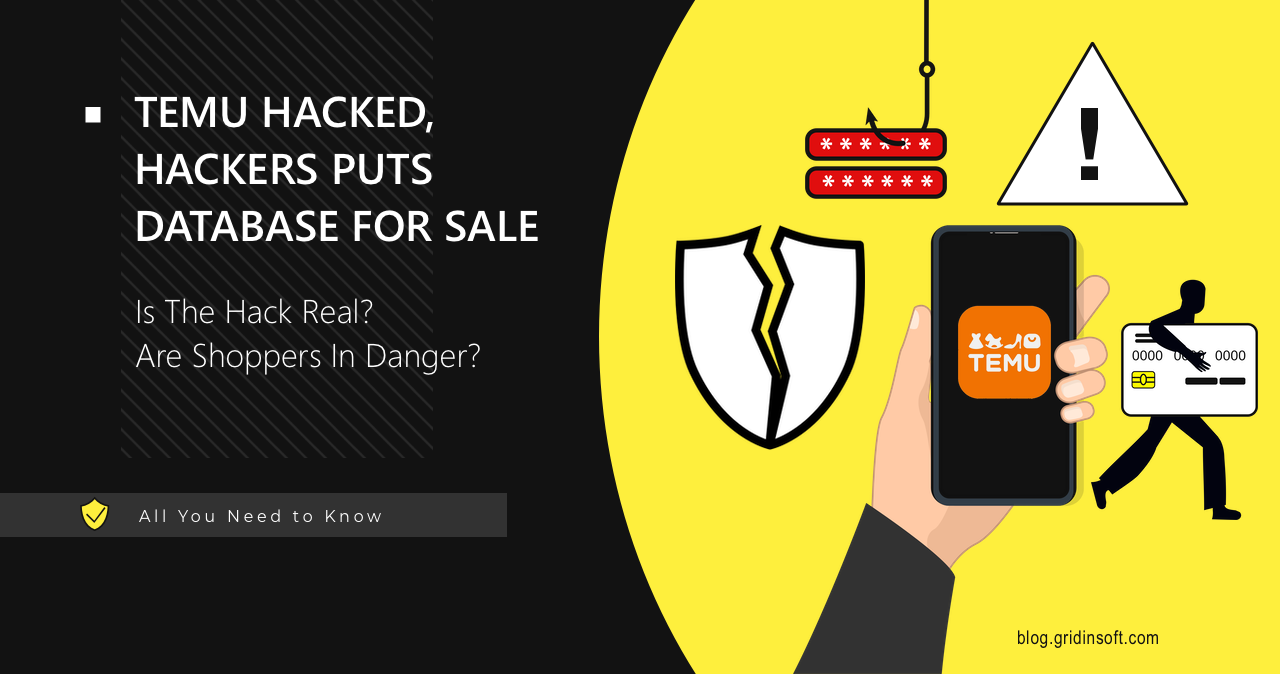
Temu Allegedly Hacked, Data Put on Sale On The Darknet
Chinese retailer Temu allegedly suffered a huge data breach. Hackers have put…
Critical VMWare vCenter Server RCE Vulnerability Fixed
On Tuesday, September 17, Broadcom released a security update that fixes a…
Amazon Prime Day Scams and Fake Amazon Websites
Amazon Prime Day scams is a name for fraudulent schemes that parasite…
Top 3 Vulnerabilities of 2024: How to Block and Prevent
Any successful remote cyberattack starts with penetration of the target network. Regardless…
Trojan:Win32/Fauppod!ml
Trojan:Win32/Fauppod!ml is a detection that is based on machine learning and is…
Crypto Recovery Scams: How to Protect Yourself from Secondary Fraud
Crypto recovery scams are a specific type of fraud targeting individuals who…
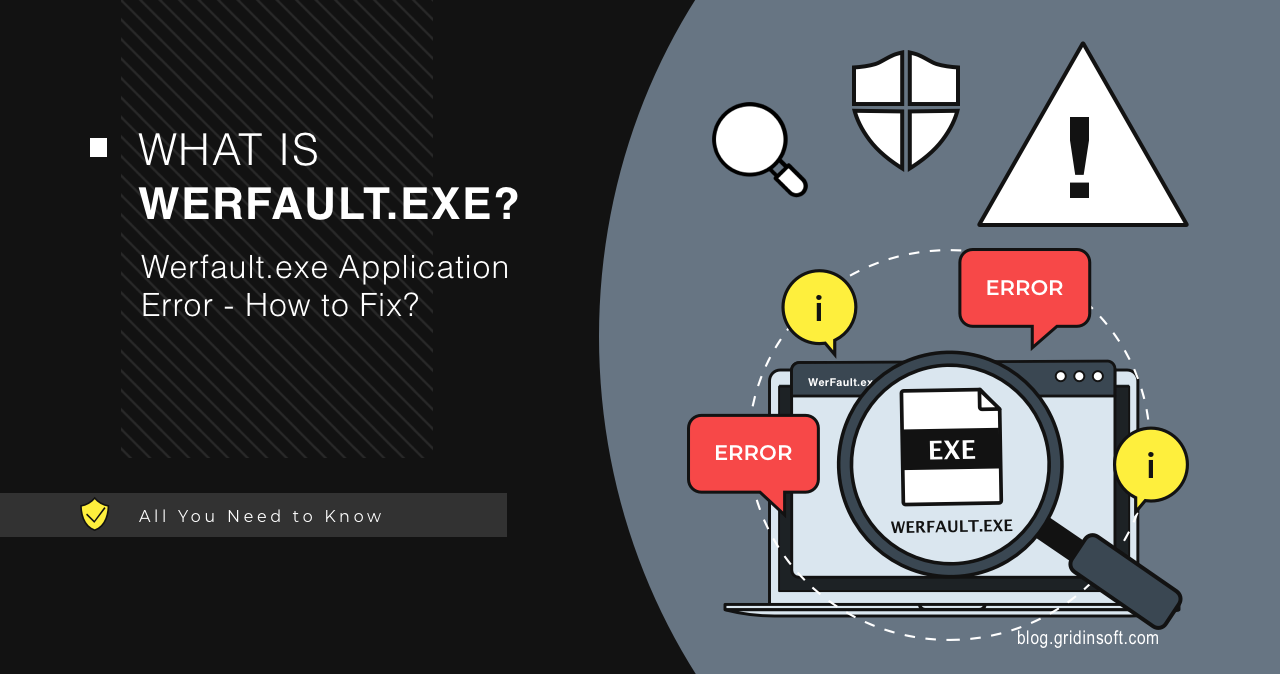
Werfault.exe Error
Werfault.exe is a system process used to collect information about program errors,…
McAfee Scam Email
The McAfee email scam is a dangerous form of phishing fraud targeting…
Ads(exe).finacetrack(2).dll Virus Explained
Ads(exe).finacetrack(2).dll is a detection name that you can see on websites pretending…