A vulnerability, CVE-2024-38856, has been discovered in Apache OFBiz that allows unauthenticated remote code execution. A patch is currently available, and the developer heavily recommends installing it, as hackers will not hesitate exploiting the issue after the disclosure. Considering the high CVSS score of the flaw, not much more motivation should be given.
Critical Apache OFBiz Flaw Allows Unauthorized Code Execution
Cybersecurity researchers have discovered a critical zero-day vulnerability in Apache OFBiz. The authorization flaw, identified as CVE-2024-38856, has a CVSS score of 9.8 and affects versions up to 18.12.14. Successful exploitation allows attackers to execute arbitrary code on vulnerable systems without authentication.
Apache OFBiz is an open-source framework for enterprise resource planning (ERP). It includes web applications that cater to common business needs such as accounting, human resources, inventory management, customer relationship management, marketing, and more. Companies like United Airlines, Atlassian JIRA, HP Development Company, and Upwork Global Inc., among approximately 170 others, use this service. Organizations using it have been advised to promptly address this critical vulnerability.
CVE-2024-38856 Overview
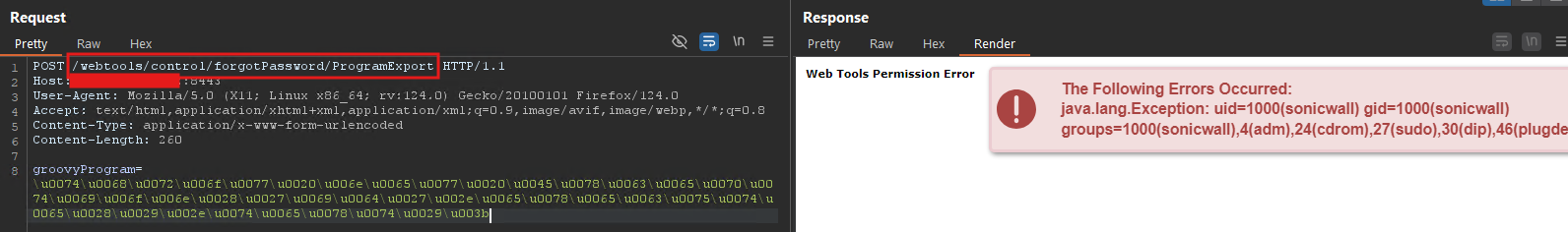
During analysis, researchers observed that an attacker could gain control of the system and execute screen rendering code under certain conditions without proper authentication.
The issue stemmed from certain parts of the system failing to correctly verify authentication. This allowed unauthorized access to specific system components. This happens because the application does not check for any authentication for the command, relying on endpoint configurations instead.
This, in fact, is not the first vulnerability in Apache OFBiz in recent months. The previous vulnerability, CVE-2023-51467, also had a CVSS score of 9.8. It was related to the login function and resulted from an incomplete fix of a previous critical vulnerability, CVE-2023-49070. The latter was a flaw that also allowed for RCE, potentially leading to complete server control and theft of sensitive data.
RCE/ACE vulnerabilities have their deserved place among the most dangerous flaws. Being capable of providing both initial access and lateral movement, they are a desired thing for any adversary, at any attack stage. And considering the placement of the CVE-2024-38856 flaw, its successful exploitation may be a key to leaking tons of important internal information.
Apache OFBiz Flaw Patched
Unlike the mentioned vulnerabilities, which attackers actively attempted to exploit, there have been no reports of CVE-2024-38856 being exploited in the wild at the time of writing. Though there is an obvious tendency for hackers to start exploiting the flaw soon after the disclosure. That happened with some of the previous vulnerabilities in Apache products, and I have no doubt that this will happen to this one, too.
Regardless, the Apache OFBiz team released a patch for CVE-2024-38856 within 24 hours after the disclosure. Companies that use OFBiz should update to version 18.12.15, which addresses the vulnerability. Unfortunately, no workaround is available, meaning that applying the update is the only fix option.