A young security researcher has found a vulnerability in Cloudflare’s caching system. This flaw allowed attackers to get approximate users’ locations because of CDN server address exposure. By exploiting some messengers, attackers could analyze cached file or emoji requests even without the direct user interaction.
0-Click Deanonymization Attack Exploits Telegram, Signal, Discord And Other Apps
A 15 year old cybersecurity researcher who names himself Daniel has uncovered a chilling 0-click deanonymization attack targeting popular platforms like Signal and Discord. By exploiting Cloudflare’s caching mechanisms, the attacker can uncover the location of the receiver. The method relies on Cloudflare’s geographically distributed datacenters, which are placed near large cities to improve content delivery times. Analyzing cached data to reveal where a user is accessing the internet. So, your secret bunker might not be as secret as you think.
In brief, the attack works by analyzing caching behaviors triggered by routine actions, like receiving message attachments or friend requests. In Signal, even a push notification could betray your location. While on Discord, a custom emoji or avatar might as well be a homing beacon. The researcher even created a bot to automate the process to literally demonstrate the capabilities of this theory.
How Does It Work?
By analyzing the “cf-cache-status” and “cf-ray” headers in HTTP responses, an attacker can identify the specific Cloudflare datacenter serving a user’s request. The response appears regardless of user participating in the communication in any way, all that should happen is a successful message delivery. Since these datacenters are geographically distributed, pinpointing the one gives an estimate of the user’s location.
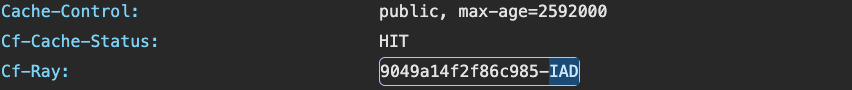
To bypass Cloudflare’s anycast network restrictions, a tool called Cloudflare Teleport was created. This tool, based on a bug in Cloudflare Workers, allowed HTTP requests to be routed to specific datacenters. However, Cloudflare patched the vulnerability later.
Real Test
The first practical application of this method involved Signal. An attacker exploited the caching of message attachments served via Cloudflare. When a user received and opened a message containing an attachment, their device downloaded the file, causing it to be cached in a local datacenter. By analyzing which datacenters cached the file, the attacker could approximate the user’s location.
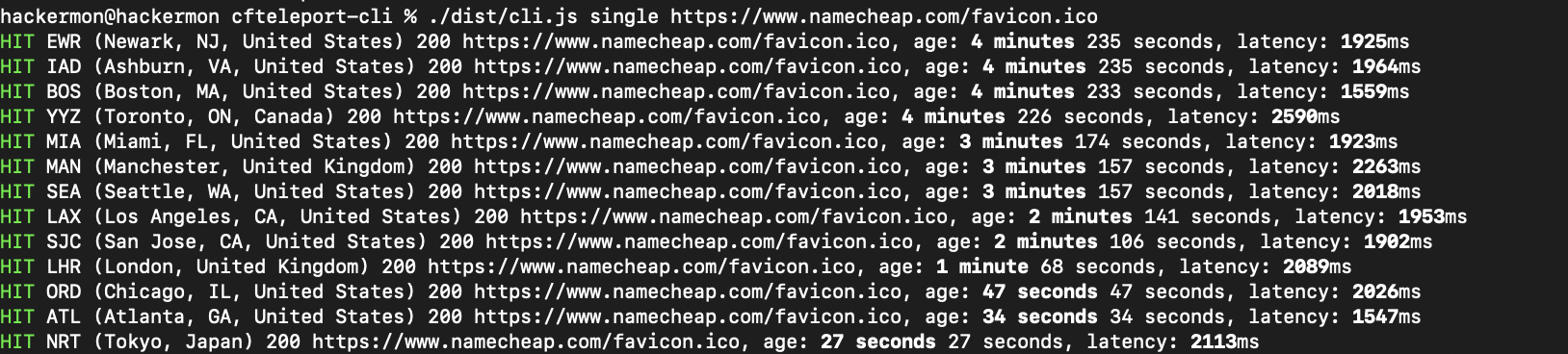
An alternative scenario is to exploit the “0-click version» of this vulnerability. That is, the user does not need to take any action. If the target had push notifications enabled, their device automatically downloaded message attachments to display in the notification. This meant the attacker could determine the user’s location without requiring any interaction.
Discord served as the next demonstration platform. It was similarly vulnerable, and an attacker could exploit cached custom emojis or user avatars. For instance, sending a friend request to a target triggered a push notification, which included the attacker’s avatar. The target’s device would download the avatar, allowing the attacker to identify the datacenter that handled the request and infer the target’s location.
The researcher also developed a private Discord bot named GeoGuesser, which automated the attack. The bot changed its avatar to ensure unique caching, sent a friend request to the target, and analyzed the caching behavior to estimate the target’s location. In one example, the bot accurately pinpointed the approximate location of Discord’s CTO by triangulating data from two datacenters.
Companies Response
Being a decent tester, the young researcher alerted the companies through Bug Bounty Reports, to which the companies responded with varying levels of concern and urgency. Signal, for instance, outright rejected the report, claiming the problem wasn’t theirs to solve. Telegram, by contrast, emerged unscathed thanks to their custom protocol and lack of reliance on Cloudflare.
Discord, initially promising action, decided the issue was Cloudflare’s responsibility. Meanwhile, it wouldn’t be the first time for Cloudflare. As it turned out later, another researcher had reported this problem a year ago. But without proper proof, the problem was not considered noteworthy. Finally, Cloudflare patched it. Reporters got award a $200 bounty, and split it amongst themselves.