Google Project Zero researcher reports on a Samsung zero-click vulnerability in a distribution supplied by the company. The shortcoming allegedly sits in the audio subsystem, and is caused by buffer overflow in certain scenarios.
The finding of Natalie Silvanovich was brought to Google back in September 2024, while the official disclosure of the flaw happened only a week into 2025. The reason for such a hesitation is obvious: the developers were working on patching the flaw before it became publicly acknowledged.
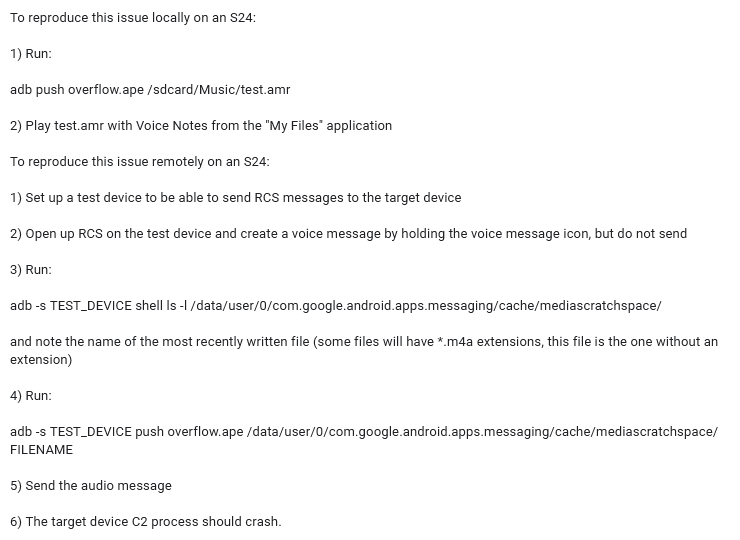
CVE-2024-49415 is a vulnerability in Samsung versions of Android 12, 13 and 14, that resides in libsaped.so, a library of C2 media service responsible for audio playback. It is possible to push executable code beyond the application buffer, making the program that uses the library to execute the code. It has received a CVSS rating of 8.1, which is low compared to other zero-click vulnerabilities.
Typically, flaws like Samsung zero-click one occur because the software does not handle its inputs properly. A thing that should not be an executable code is handled as one, which makes room for malicious activities in this place.
Researchers report about Samsung zero-click flaw being possible to exploit with a specially crafted voice message sent through the Google Messages app in Android. The zero-click nature of the flaw is provided by the way the app handles voice messages, and makes it possible to infect the user device without any interaction needed.
Why is Samsung Zero-Click Vulnerability Dangerous?
Zero-click vulnerabilities are generally considered to be among the most dangerous flaws. Yet the Samsung zero-click flaw got the severity rating of “only” 8.1 – a notable step down from RCE/ACE vulnerabilities that require no authentication, for example.
The main concern of zero-click vulnerabilities is the fact that they need no user interaction whatsoever. All that adversaries need is to send a specially crafted package or, in this case, a voice message. The rest of the action – downloading and executing a malicious program – is done by the application itself; as it is considered trusted, a lot of security solutions will not raise any alarm.
Attackers commonly use such flaws to silently deliver the payload to the target system. An infamous Pegasus spyware, that primarily targets iOS devices, is focused almost exclusively on running via zero-click vulnerabilities.
In the case of Samsung zero-click flaw, the reason for the lower severity is the need for the specific application for the trick to work as intended. In cases other than Google Message, the app may simply crash or not execute the payload properly.
Fortunately for all Samsung users, the flaw is already fixed; all that one needs to do is to install the latest security updates. As the flaw is considerably easy to exploit, I’d expect con actors to start using it massively after the recent disclosure.





