Contacto virus is a newly identified ransomware strain that encrypts victims’ files and demands a ransom for their decryption. We identified this sample on January 7, 2025, and made a comprehensive analysis of the threat.
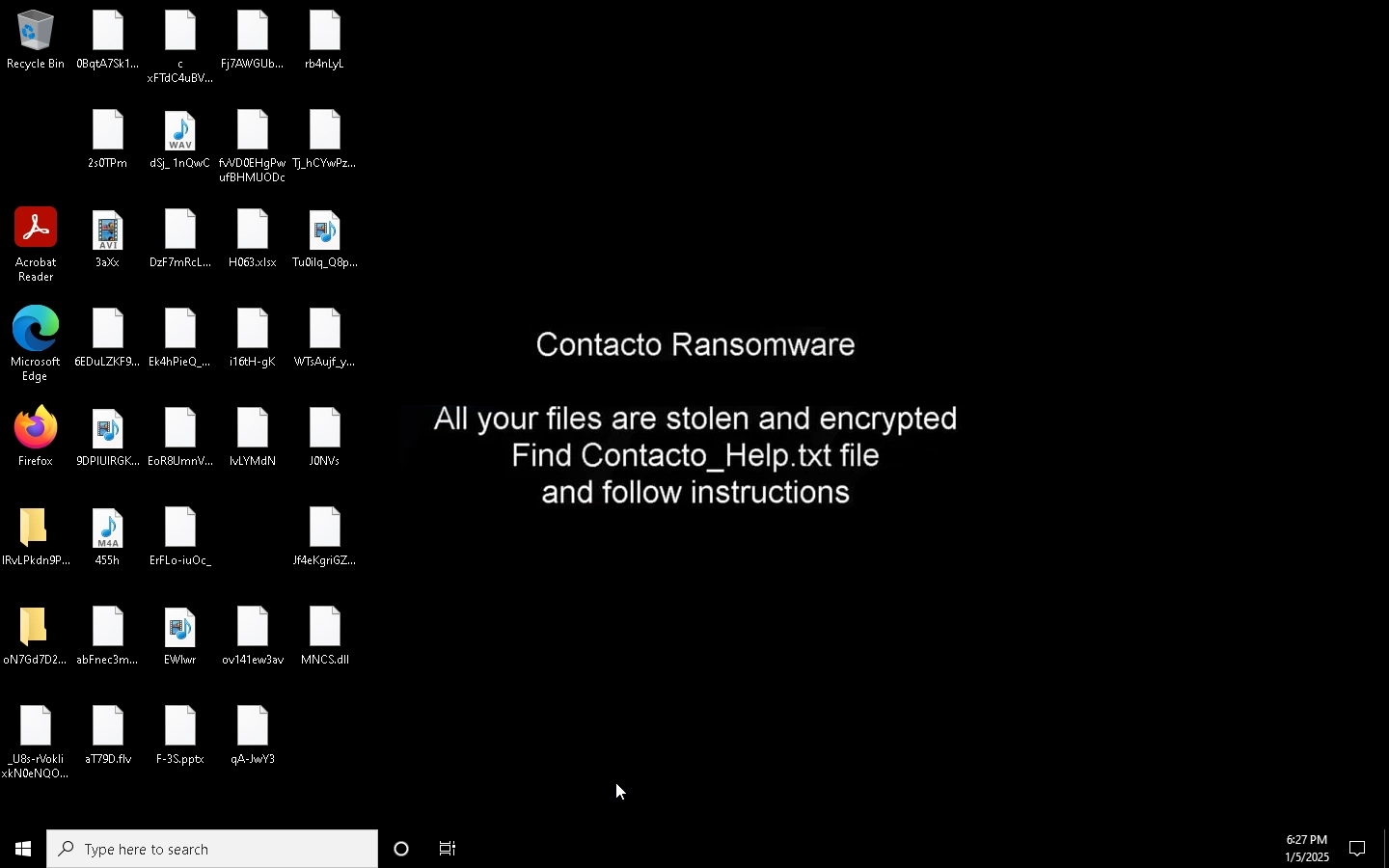
One hallmark of Contacto is its tendency to modify the system wallpaper, replacing it with a black background displaying a message in white letters: “All your files are stolen and encrypted. Find Contacto_Help.txt and follow the instructions”.
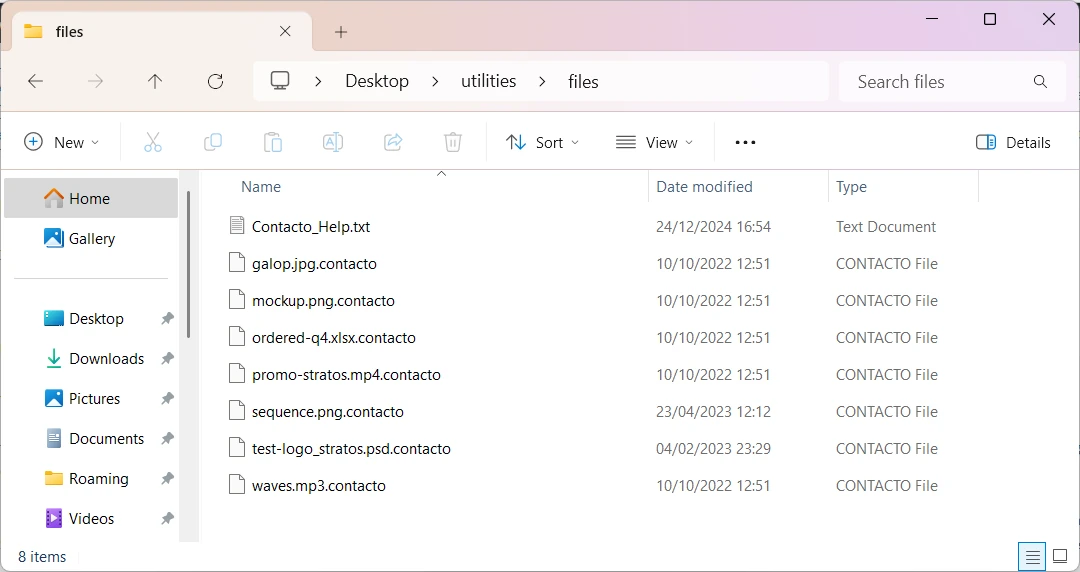
As per usual for malware of this type, the ransomware appends its unique .Contacto extension to encrypted files. The files as the result turn from, for example report.docx report.docx.Contacto. These visual and structural changes make it immediately clear to victims that their system has been compromised.
Ransom Note Overview and Analysis
The Contacto_Help.txt file mentioned in the altered wallpaper is a ransom note. It appears on a desktop and in other folders that the ransomware counts as important. Inside this note, there are pretty basic pieces of information, threats of data loss if the victim tries other decryption ways, and contact information.
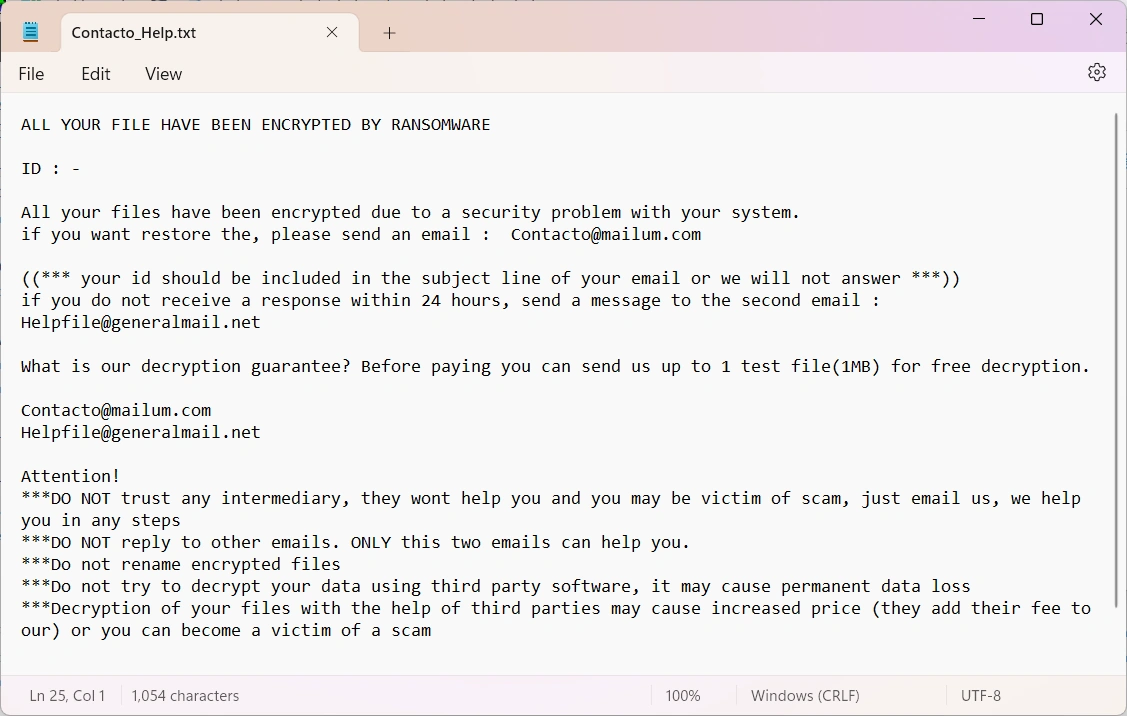
For contacting the hackers, the victim is offered to email 2 addresses – [email protected] and [email protected]. Both are specific for this malware, i.e no other ransomware strains ever used these addresses. This makes it harder to detect possible connections with currently active malware samples and hacker groups.
One of the important parts of the message is victim ID, listed at the very top. This ID is unique for the system, and has a corresponding decryption key stored on cybercriminals’ servers.
To prove having a decryption tool, hackers offer the victim to send them a file for test decryption. It should be less than 1 megabyte in size and free of any sensitive content. Such a trick aims at making the victim more confident about paying for the decryption, though it still does not guarantee anything.
I would heavily recommend you to avoid paying the ransom. Paying off the bill stimulates further activity of cybercriminal actors, so their attacks will happen more and more often. Also, you may not need to pay the money in the first place – there are ways to recover the files, which I will describe later in this article.
Contacto Ransomware Virus Overview
Contacto ransomware virus is built with heavy obfuscation techniques, making static analysis challenging and allowing it to bypass basic antivirus solutions. It also checks the system environment to avoid detection in virtual machines or debugging setups.
If the checks pass, the ransomware executes its payload by disabling system protection mechanisms, including Microsoft Defender. Another action is stopping built-in backup mechanisms like Volume Shadow Copy, so the user cannot use it to revert the system to pre-attack state.
To avoid early detection by the original file, it creates its duplicate in the ProgramData folder. This also prevents the user from being able to see the file and delete it, at least without additional tweaking. Once this duplicate file is ready, the malware deletes the original file and creates a selection of persistence mechanisms (registry keys, Task Scheduler entries) that launch the new file upon system startup.
Then, the malware starts file encryption. It uses a rather strong cipher algorithm, which ensures brute force decryption is not possible. Once the encryption is over, it initiates system reboot, which also changes desktop wallpaper; as it starts with no notification for the user, one can lose some of the progress and data. But, well, that is not the biggest concern during the ransomware attack.
How to Remove Contacto Ransomware [Important]
Before attempting any file recovery, it is vital to remove the ransomware to prevent further encryption. Contacto remains active even after finishing the encryption, continuously targeting new or restored files.
GridinSoft Anti-Malware will get you covered against active ransomware threats. With its advanced detection modules, it can effectively eliminate Contacto, no matter how well-hidden it is. Follow the guide below; opt for a Full Scan – this will check the entire system, down to the most remote files and configurations.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Recover .Contacto Files for Free
Although Contacto’s encryption algorithm is robust, it is still possible to recover your files. The methods I’ve picked are free and may only require your time and patience to execute properly.
Large Files Are Ignored. To speed up its operations, Contacto often skips encrypting files over 500 MB. Files like large videos, archives (e.g., ZIP, RAR, 7z), and some of the Office documents may only have the extension altered, with no real encryption applied to them. Simply removing the ransomware extension can restore file functionality.
File Recovery Tools. Depending on how Contacto handles files during encryption, recovery tools may be able to restore them to their original state. Choose a recovery tool capable of handling a broad range of file formats to maximize the chances of success.
Online Backups and Cloud Storages. Even though a lot of people despise automatic backups, they may actually be useful in that case. Check for any places you may have uploaded files before the attack; even conversations in messengers and social media may contain the files you need. And in future, I’d advise you to use backups on a monthly basis – this will ensure your resistance to any malware or hardware failure.