Owners of popular hardware cryptocurrency wallets Ledger have become the target of phishing attacks. Hackers send out fake emails to lure recovery phrases from users and gain access to crypto assets. This is yet another scam campaign that targets Ledger wallet holders.
Ledger wallet owners have been targeted by attackers
A new phishing campaign is targeting Ledger cryptocurrency wallet users by masquerading as a data breach notification. The attack scheme is built on using a multi-stage redirect system through Amazon AWS servers, which eventually leads users to a fake website. Their aim is to steal recovery phrases, enabling them to access and empty victims’ cryptocurrency wallets.
Ledger is a hardware wallet designed to securely store, manage, and sell cryptocurrency. These wallets use recovery phrases – 12, 18, or 24 words generated during setup – as a critical security measure. These phrases act as a master key, granting full access to the wallet and its funds. If someone obtains this recovery phrase, they can control the wallet entirely.
How Does the Scam Work?
The phishing attack begins with an email sent via SendGrid, that claims users’ wallets are secure but warns that their recovery phrases might have been exposed. To address this, the email urges recipients to verify their recovery phrase using a “secure verification tool”.
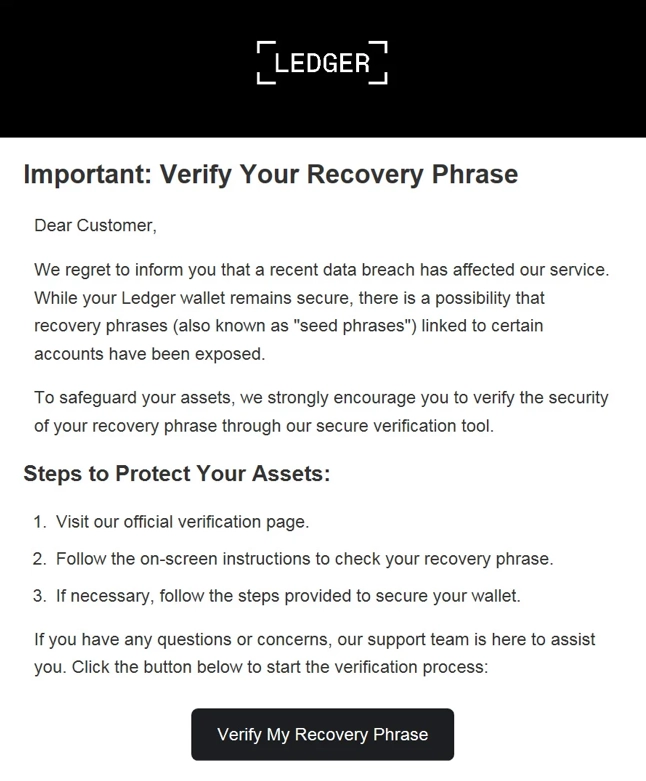
Clicking the “Verify My Recovery Phrase” button redirects victims to what appears to be a Ledger verification site. Initially hosted on an Amazon AWS domain, the link ultimately leads to a phishing site with the domain “ledger-recovery[.]info”. The phishing site is designed to mimic the official interface, asking users to enter their recovery phrases.
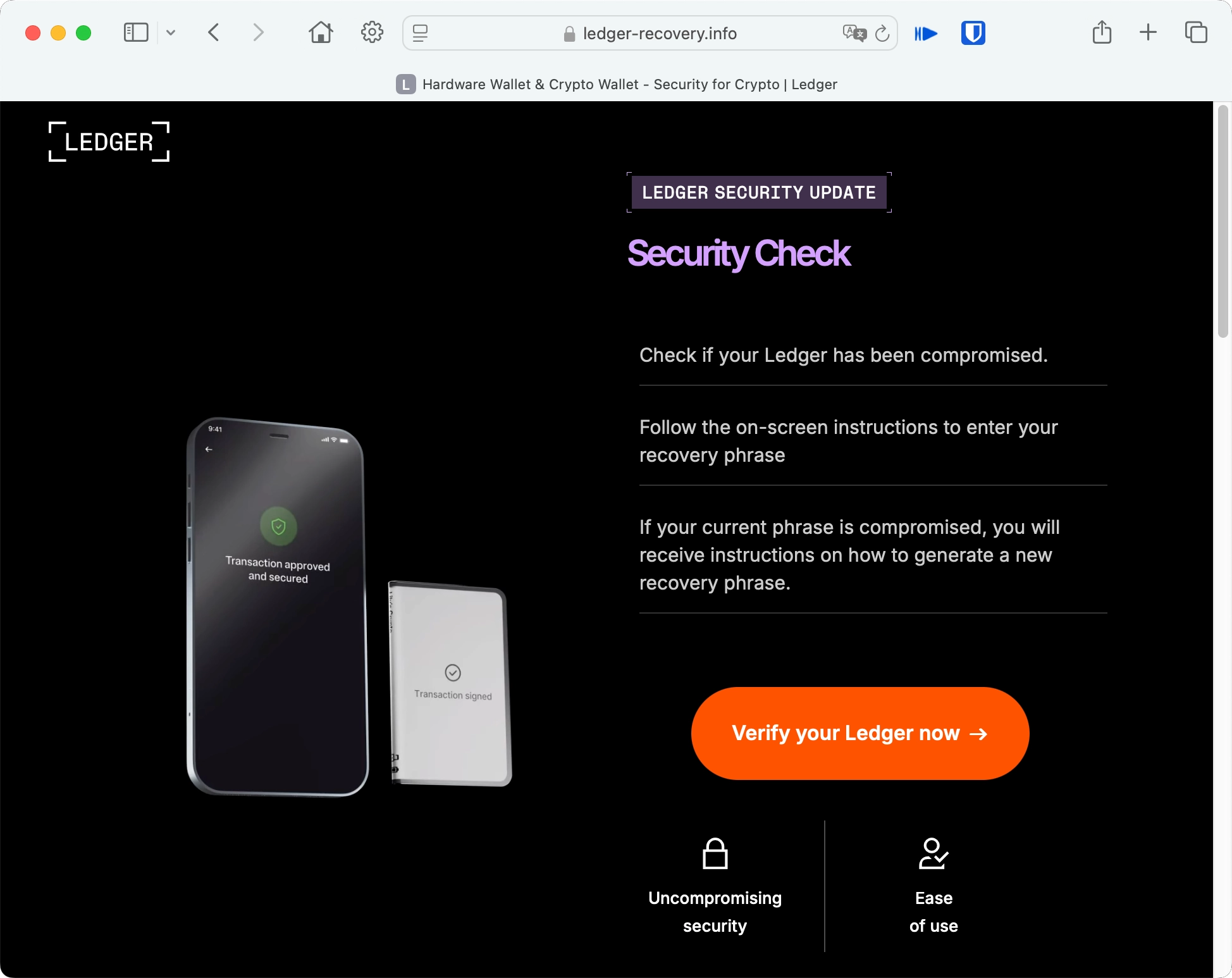
As users type in each word, the site verifies it against a list of 2,048 valid recovery phrase words, crossing out any invalid entries. Yes, these words are in fact known to everyone, but their selection for each user and their order is the key. Each word entered is immediately sent to the phishing site’s backend and stored. Regardless of what recovery phrase is entered, the site always claims it is invalid, prompting users to re-enter it multiple times. This tactic ensures that attackers capture accurate data.
Although the domain “ledger-recovery[.]info” was registered on December 15, 2024, this is not the first attack of its kind. Security analysts report about detecting similar scam sites before, but they were separated from the email spam campaign and thus not attributed to any serial action.
Why is Ledger a Target?
Ledger has become an increasingly popular target for scam actors. We have a news article about another phishing campaign that impersonates the company to promote fake firmware updates. These emails similarly attempt to trick users into sharing their recovery phrases. With these phrases, attackers can gain full access to victims’ cryptocurrency wallets and steal their funds.
Ledger has been a persistent target of phishing campaigns, especially after a 2020 data breach that exposed customers’ personal information, including names, addresses, phone numbers, and email addresses. This breach provided attackers with a rich dataset for crafting convincing phishing campaigns.
If you receive an email like this, never follow the steps in the email. Instead, mark it as spam and delete it. Remember: one should never, under any circumstances, disclose a recovery phrase to anyone. It is not needed for sending cryptocurrency to you, and no tech support agent will ever request it.
To be sure about the websites you are opening, consider using a reliable anti-malware software with a built-in network protection feature. GridinSoft Anti-Malware will provide you with excellent real-time scanning of websites that you visit, protecting even against the most recent online threats. Give it a shot by clicking the banner below.





thanks for info.