Attackers are targeting users of Meta services with phishing attacks. Classic fraud schemes are gaining momentum once again, with users risking their accounts and all the data present within them. The only difference is in tactics: hackers now impersonate Meta Security mailing about security issues with the account.
Email phishing scams from Meta Security
Researchers have observed a rise in phishing scams targeting Facebook and Instagram users. Cybercriminals are crafting convincing emails disguised as account security alerts. Despite the tactic in its core being a rather typical email phishing, the unusual disguise is what tricks the users into believing it is actually real.
In fact, these emails aim to steal users’ credentials and personal information. This is yet another example of fraudsters exploiting a well-known brand name for malicious purposes. Overall, Meta and Facebook in particular were used by scammers of different flavors pretty often, check out our separate post about Facebook scams.
How does the Meta Security Scam Work?
The scheme is straightforward and relies on human factor. Fraudsters pose as Meta, sending emails that replicate the company’s corporate style and tone. These emails include warnings like “suspicious activity,” “account suspension,” or “unauthorized login attempts,” paired with urgent requests for immediate action. As the email is styled to look as genuine Facebook mailing, users have little to no suspicion at this point.
When the receiver clicks the link, they are redirected to a fake login page that looks identical to Meta’s official site. The obvious goal here is to trick users into entering their credentials, which are then captured by the attackers. With the use of the specific kind of trickery, this stage goes beyond any security mechanisms that are present in modern web browsers, and the user will get the “incorrect login and password” error as the result.
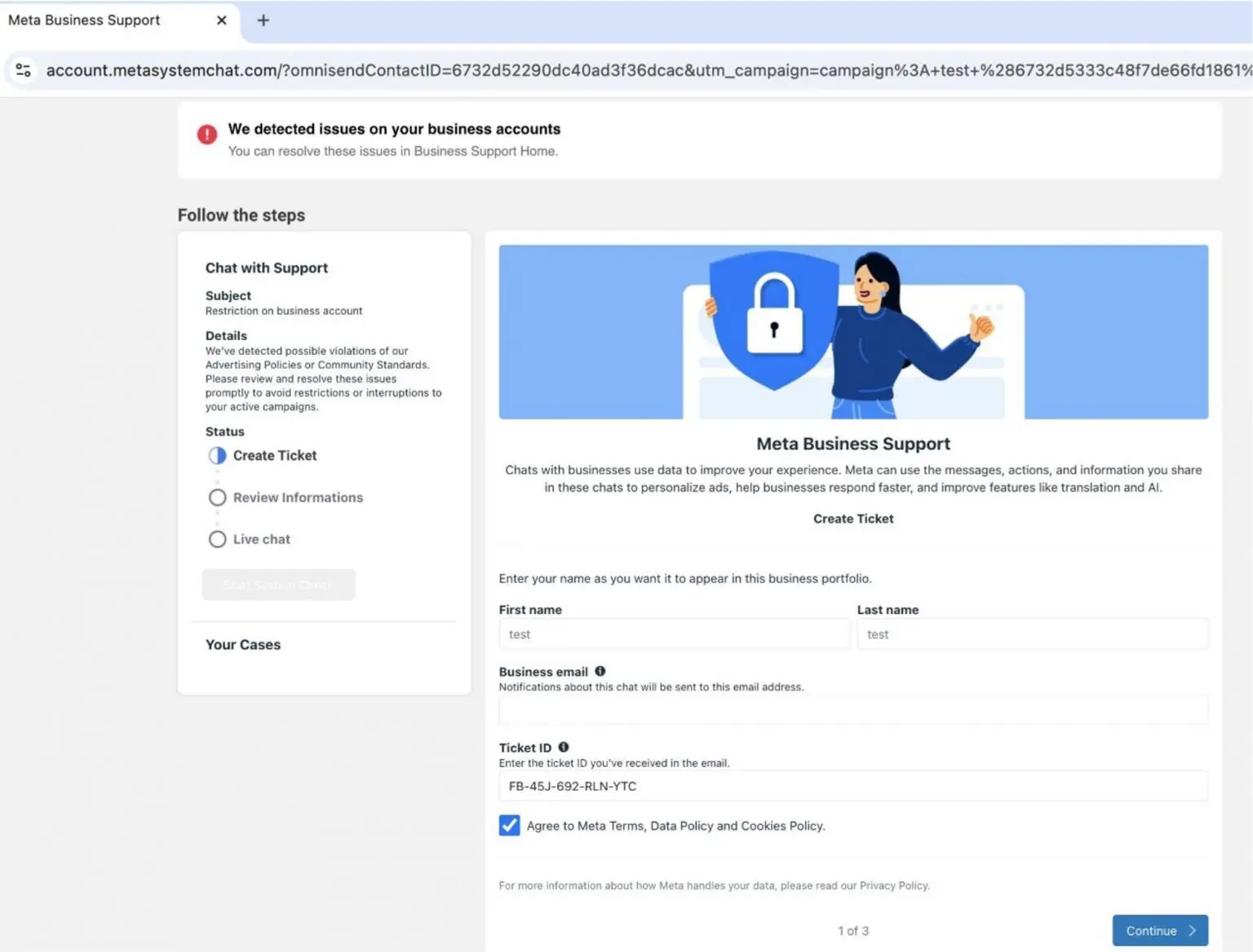
Both the phishing site and email address the message was sent from contain an important clue. They are completely different from regular credentials that Meta uses for mailing or login procedures. Frauds typically set them up days before the scam, or, in the case of an email, use a hijacked address that may bypass a lot of spam filters.
Advanced Version of the Scam
Researchers have also found a more advanced version of this scam. Victims are prompted to take additional steps, such as generating a two-factor authentication (2FA) code from their account settings. This tactic allows fraudsters to gain access not only to login and password, but also to multi-factor authentication code, which effectively provides them with the information enough to get into the most protected accounts.
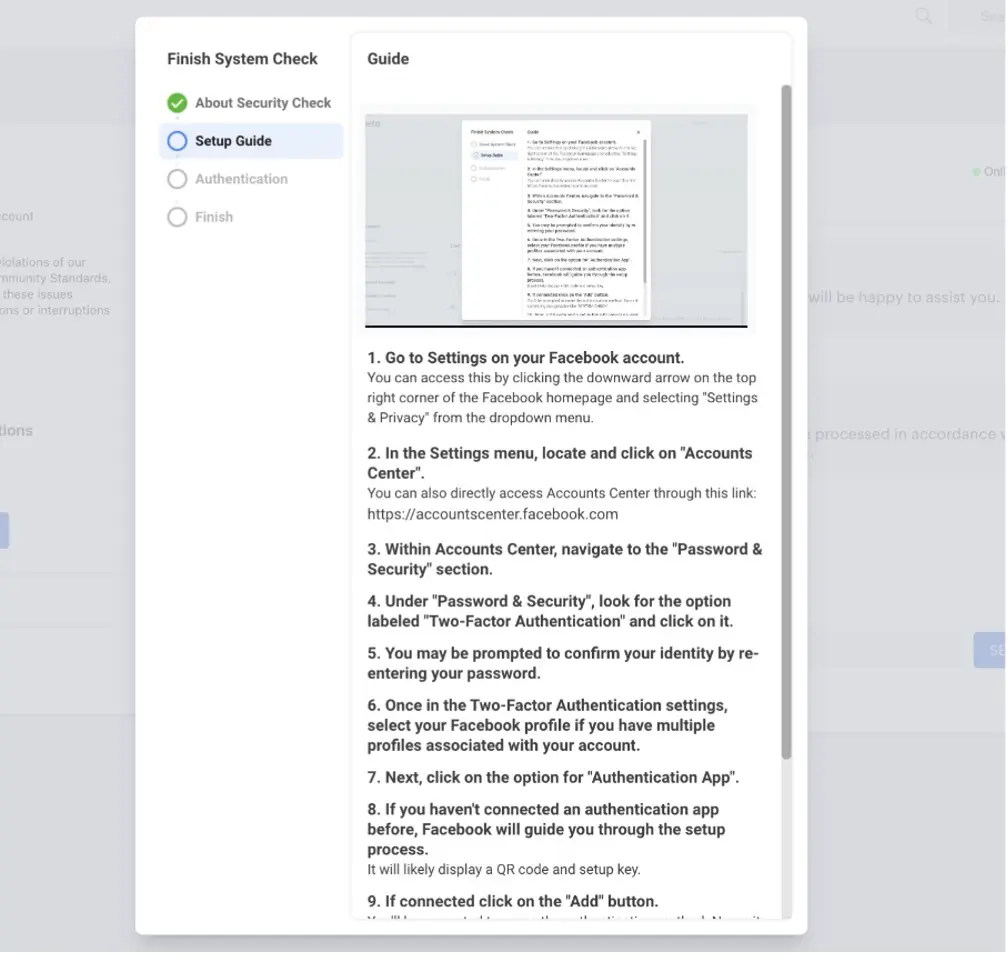
Such advanced scams typically come with a different email text as well. In one of the recent iterations, scammers impersonated Meta security officers and claimed the recipient’s account had been suspended for inappropriate behavior. The email directed the victim to resolve the issue by visiting a linked “security check” webpage. On this page, users were asked to provide sensitive information, including 2FA codes, under the guise of account restoration.
How to Avoid Meta Email Phishing Scams?
Although we detail the signs of scams in nearly every post, judging by the number of incidents, this information bears repeating.
First, pay attention to the sender’s address. While sender addresses can be spoofed, smaller scammers often don’t bother. Instead, they use random email addresses with the sender’s official name. Legitimate Meta emails are sent only from domains such as @facebookmail.com or @instagram.com.
The second point to check is the writing style. Of course, with the advent of LLM and Dark LLM, the level of persuasiveness of fraudulent messages has increased, however, there is one difference that gives away the fraudulent nature of the message. One key indicator is how the email addresses the recipient. Genuine emails address users by name, whereas fraudulent ones use generic terms like “Dear User” or “Account Holder”.
And finally, use a reliable security solution that will prevent phishing pages from opening on your device. GridinSoft Anti-Malware will provide you with an excellent online security shield that can hold up against the latest web threats. Download it by clicking the banner below and try its full power during the 6-day free trial period.