A critical vulnerability in Fortinet was exploited in the wild. Although the attackers did not deploy malware, they managed to steal technical information about the devices.
New Fortinet Flaw Has Been Exploited
On October 23, 2024, Fortinet confirmed that a critical zero-day vulnerability in FortiManager has been actively exploited since late June 2024. The flaw, CVE-2024-47575, named FortiJump, has a CVSS score of 9.8, (critical), and allows attackers to connect to FortiManager servers without proper authentication.
As a result, the attacker gains unauthorized access to execute commands and steal configuration data from managed FortiGate devices. Over 50 FortiManager servers have reportedly been compromised, and it is only up to guesses how much the hackers have already breached or will breach in future.
This vulnerability first emerged after Fortinet privately alerted customers to suspicious activity, and Fortinet has confirmed CVE-2024-47575. According to Mandiant (the company that worked with Fortinet to investigate the incident), attackers used this flaw to exfiltrate data, such as device configurations and encrypted user credentials. Despite confirmed exploitation of this vulnerability, researchers found no direct evidence of malware deployment or lateral movement within compromised systems.
CVE-2024-47575 Technical Details
The CVE-2024-47575 vulnerability exists in the FortiGate-to-FortiManager (FGFM) API that FortiManager uses to manage FortiGate devices. This flaw arises from missing authentication checks in the fgfmd daemon, allowing an attacker with a valid Fortinet device certificate to register and connect to any exposed FortiManager server. Once connected, attackers can execute commands on both FortiManager and its connected FortiGate devices.
Exploitation begins with an attacker-controlled Fortinet device, which, even in an unauthorized state, can still communicate via the FGFM protocol. This setup providesserves as an entry point for attackers to retrieve sensitive configuration data, including FortiGate credentials and IP information.
Researchers have reported that an attacker identified as UNC5820 has attempted to exploit FortiManager devices twice since June 27, 2024. Although the stolen data poses risks of further exploitation, Mandiant observed that UNC5820 primarily focused on exfiltrating configuration data rather than moving laterally across networks.
What’s Next?
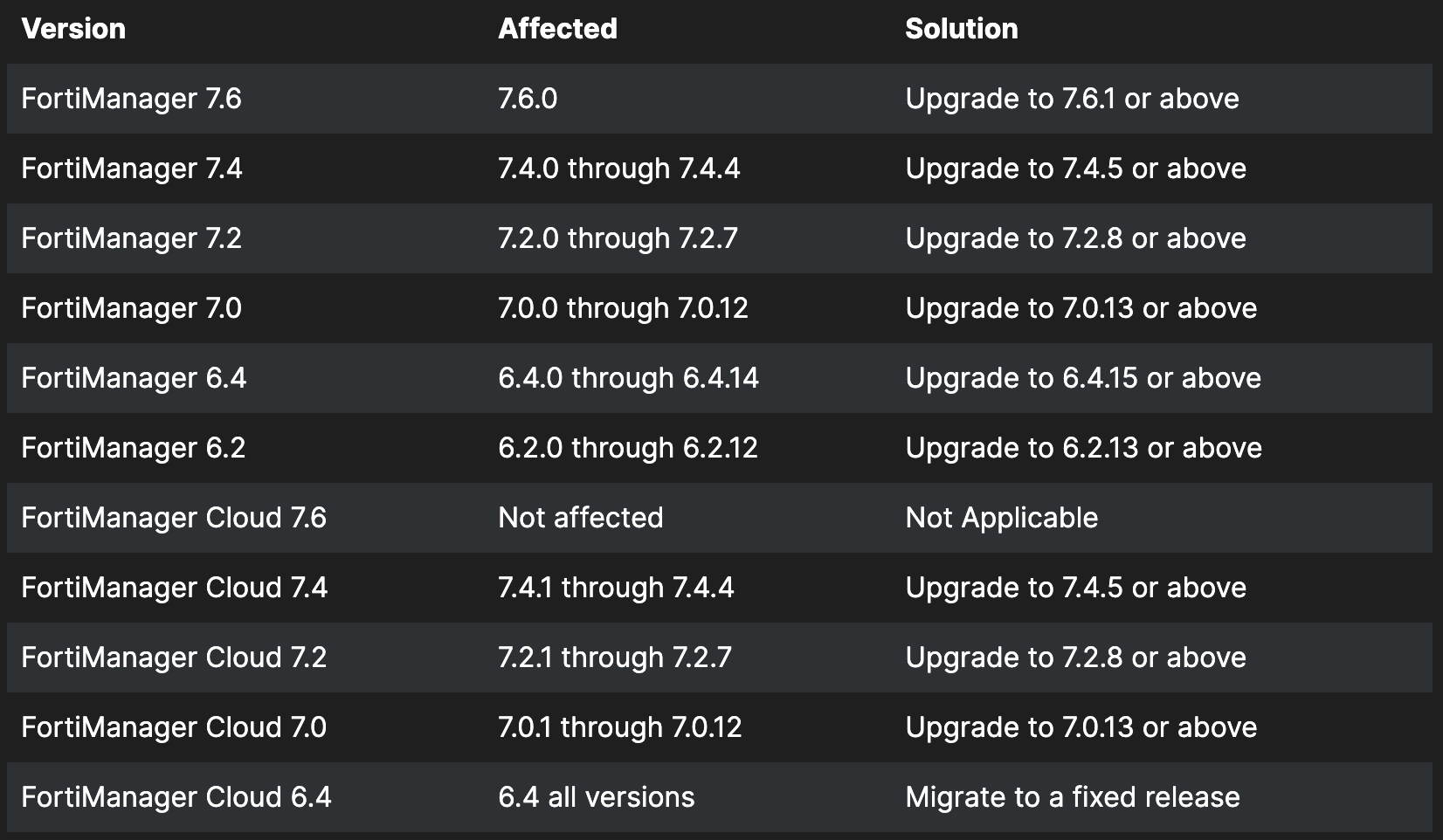
According to Censys, there are approximately 4k vulnerable FortiManager administrative portals online, with nearly 30% located in the United States. To address this vulnerability, organizations should urgently upgrade FortiManager to secure versions, specifically the patches released on October 24, which include 7.0.12, 7.2.5, and 7.4.3 or later.
Fortinet also recommends setting up IP allow-lists to control device connections and using the command “set fgfm-deny-unknown enable” to prevent unauthorized devices from accessing FortiManager.
Additional guidance includes configuring custom certificates (available from version 7.2.2 onward) and restricting public access to FortiManager’s admin portals. In addition, it is recommended to check access logs for suspicious activity.
Given the high risk associated with this vulnerability, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has included CVE-2024-47575 in its Known Exploited Vulnerabilities catalog, urging federal agencies to apply these patches by November 13, 2024.