Cybercriminals promote a fake Google Authenticator page through ads in Google Search. According to the report, they use a tricky scheme to hide the fraudulent domain and make the ad contain a genuine URL. The resulting page, which looks exactly like the original Google Authenticator one, downloads a malicious file.
Fake Google Authenticator Downloading Page Promoted on Google Ads
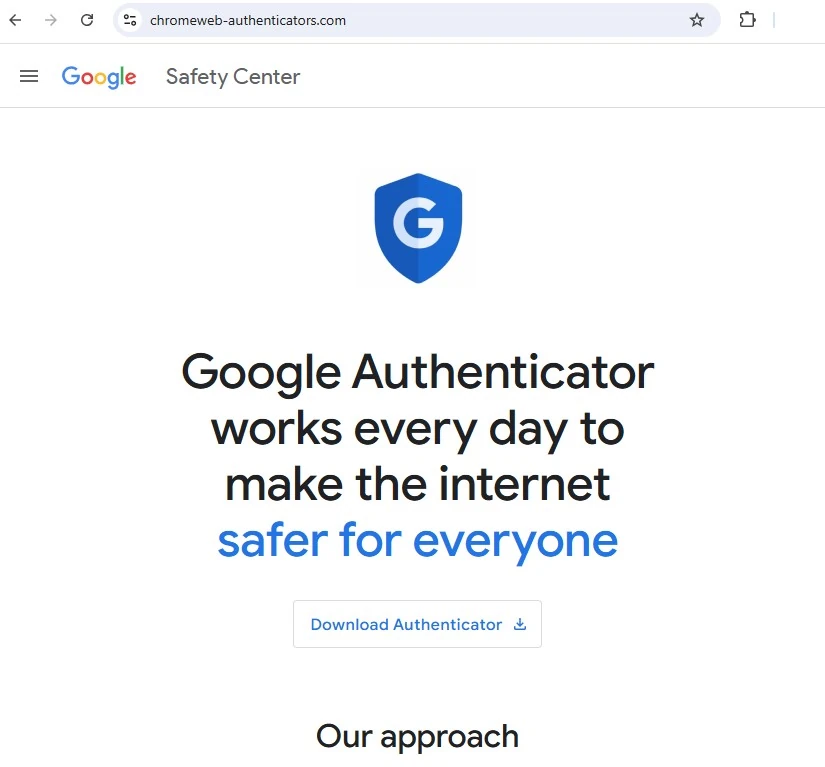
On July 30, 2024 analysts noticed an advertisement on Google Search, that leads to a website mimicking the legit Google Authenticator downloading page. This is not the first ever abuse of a not ideal ad moderation in Google Ads, but this time frauds dare to fake Google itself. The exact scam advertisement uses fancy tricks that make the link in the ad look genuine. But upon clicking it, a chain of redirects is triggered, throwing the victim to chromeweb-authenticators.com website.
List of domains used in this scam
- gg2024.info
- gg2024.com
- authenticcator-descktop.com
- authentificatorgoogle.com
- authentificator-gogle.com
- athentificator-gogle.com
- updater-pro.com
- authentificatorgogle.com
- authenticattor-googl.com
- chromstore-authentificator.com
- authentificcatorgoolgle.com
- authenticator-google.com
- authentificator-googl.com
- authentficatorgoogle.com
The website itself tries to copy the style of the original Authenticator page. It even contains links to genuine blog posts. What is different, however, is the presence of two tempting buttons that say “Download”. Thing is – Google never offered a desktop version of their MFA tool. And that is where the key part of the scheme happens.
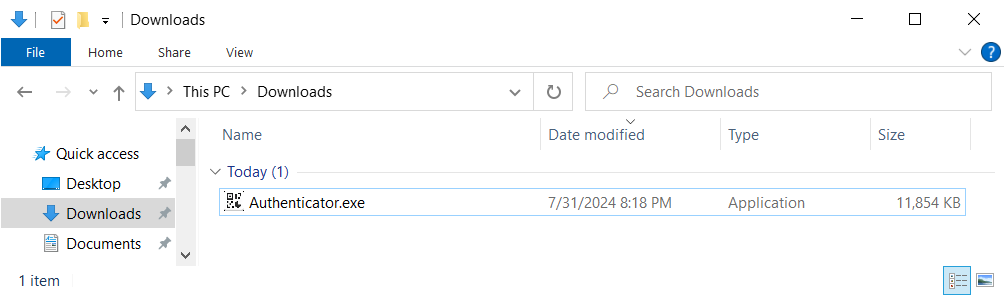
Upon clicking any of two “Download” buttons, the site pulls the Authenticator.exe file from the GitHub repository. This way, hackers who stand behind the scheme prevent early detection: GitHub is considered safe, despite being used as a malware storage in a selection of attacks. But an unaware victim will confirm the download and run the fake Authenticator, launching the payload.
DeerStealer Inside of a Fake Google Authenticator
The payload is a sample of a rather new stealer malware, dubbed DeerStealer. It is rumored as a reworked variant of the XFiles infostealer, but that makes little to no difference for the user. Once the Authenticator.exe is running, it will launch the malicious payload via DLL hijacking. After that, DeerStealer effectively runs off-the-land, in the system memory, leaving no traces on the disk.
%SAMPLEPATH%\5d1e3b113e15fc5fd4a08f41e553b8fd0eaace74b6dc034e0f6237c5e10aa737.exe
Further, malware connects to one of several C2 addresses that it carries in the system memory, and sends the collected information. Aside from the stuff that is typical for infostealers – passwords, tokens, cryptowallets etc, it also collects a rather extensive system fingerprint: GUID, language, network configurations and computer name.
How to protect against malware scams?
The best protection against malware is to mitigate the problem proactively, so you won’t even get to the point when there is malware somewhere in your system. This, however, may be problematic: as you can see from the text above, threat actors have a lot of tricks to mess with people. That is why your attention, along with proper security software, is a key for avoiding malware infections.
Review sites you get the software from. Even if an ad from Google says the site is legit, it may be not, as you can see from this case. Always check the final URL, and, if not 100% sure, use trusted online URL scanner services. Free Website Scanner is a free service that will provide you with such capabilities.
Use reliable anti-malware software with proactive protection and network security. To avoid getting into next-level scams that are totally indistinguishable from legit sites, get yourself a protection that will detect such cases for you. GridinSoft Anti-Malware provides excellent protection against the most modern threats, and will cover you even during casual browsing.