The HijackLoader malware has added new defense evasion techniques. Other threat actors are increasingly using the malware to deliver payloads and tooling. The developer used a standard process hollowing technique coupled with a trigger that makes defense evasion stealthier.
What is HijackLoader?
According to the researchers’ report, the HijackLoader malware, or IDAT Loader, has recently included advanced evasion techniques. This malware has gained immense popularity as a loader with outstanding flexibility. The attackers frequently use this malware to introduce various payloads and tools. Its structure not only facilitates the seamless integration of new functionalities but also comprises a variety of dynamic anti-analysis methods.
First observed in July 2023, the malware employs some techniques to fly under the radar. Although HijackLoader is not a highly advanced malware, it has a modular architecture. This means it can use different modules for code injection and execution – a feature that most loaders do not have. The loader downloads an encrypted configuration block that varies from one sample to another, indicating that the threat actors can change or update it quickly. This adaptability makes it a difficult target, making the development of effective countermeasures challenging.
HijackLoader Enhanced Detection Evasion Techniques
The HijackLoader follows a complex infection chain, employing multi-stage behavior to obfuscate its activities. Initially, the malware utilizes WinHTTP APIs to check for an active internet connection before proceeding with its malicious operations. Upon successful connectivity, it downloads a second-stage configuration blob from a remote address, initiating decryption and decompression processes to retrieve essential payloads. The subsequent stages involve loading legitimate Windows DLLs specified in the configuration blob, followed by the execution of position-independent shellcode.
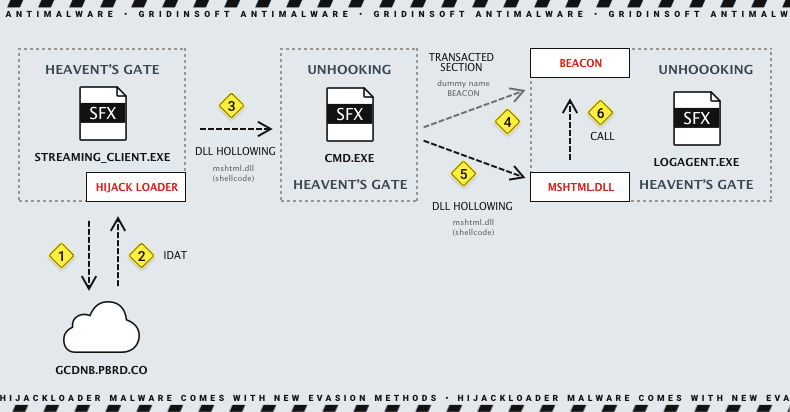
This shellcode orchestrates various evasion activities, including injecting subsequent payloads into child processes, such as cmd.exe and logagent.exe. HijackLoader uses advanced hook bypass methods, including Heaven’s Gate, to evade user mode hooks and security monitoring. It also uses process hollowing, injecting malicious shellcodes into legitimate processes to gain persistence. The malware employs interactive and transacted hollowing techniques to enhance stealthiness. These new defense evasion capabilities for HijackLoader may make it healthier and more complex to detect than traditional security solutions.
Safety Recommendations
To protect against HijackLoader and other malware, we recommend following several cybersecurity tips:
- Educate yourself. Stay informed about the latest malware threats. They constantly seek for new ways to trick users into revealing sensitive information or downloading malicious files. Educating users about these threats and the importance of avoiding opening suspicious attachments or clicking on dubious links is crucial in cybersecurity.
- Keep software updated. You should regularly update your operating system, applications, and software to ensure you have the latest versions. Malware often exploits known vulnerabilities that have been fixed in newer versions.
- Use anti-malware software. This is a complex measure to protect you against threats. Install a reputable anti-malware solution and keep it updated. These programs can detect and remove known malware strains, including variants of HijackLoader.




