Experts’ fears that attackers will use new .zip and .mov domains for phishing are beginning to be justified. A new phishing kit called File Archivers in the Browser has been demonstrated, displaying fake WinRAR or Windows File Explorer windows in the victim’s browser to convince the user to run the malware.
.Zip and .Mov Domains are Used for Phishing
Let me remind you that in early May, Google introduced eight new top-level domains (TLDs) that can be purchased to host websites or email addresses: .dad, .esq, .prof, .phd, .nexus, .foo, as well as .zip and .mov domains. The latter caused controversy among security professionals, as many considered them too dangerous.
In particular, experts fear that with the advent of new TLDs, some messaging platforms and social networks will automatically convert file names with .zip and .mov extensions to URLs, and all kinds of scammers and phishers will rush to take advantage of new opportunities. The phishing campaigns that run entirely on this trick are already active. However, some believe that nothing terrible will happen, recalling the use of homoglyphs and Unicode and other old problems that have long forced users to scrutinize URLs.
Phishing With .zip/.mov Domains Received PoC
Now cybersecurity researcher mr.d0x (known for his browser-in-browser concept attack) has created a PoC phishing toolkit that demonstrates that you can create fake WinRar and Windows File Explorer windows on .zip domains right in your browser. This will trick users into believing they are opening a ZIP file. The demo shows that the toolkit can be used to embed a fake WinRar window directly into the browser when the .zip domain is opened, giving the victim the impression that it is opening a ZIP archive and seeing the files inside it.
Let me remind you that we also wrote that Phishers Can Bypass Multi-Factor Authentication with Microsoft Edge WebView2.
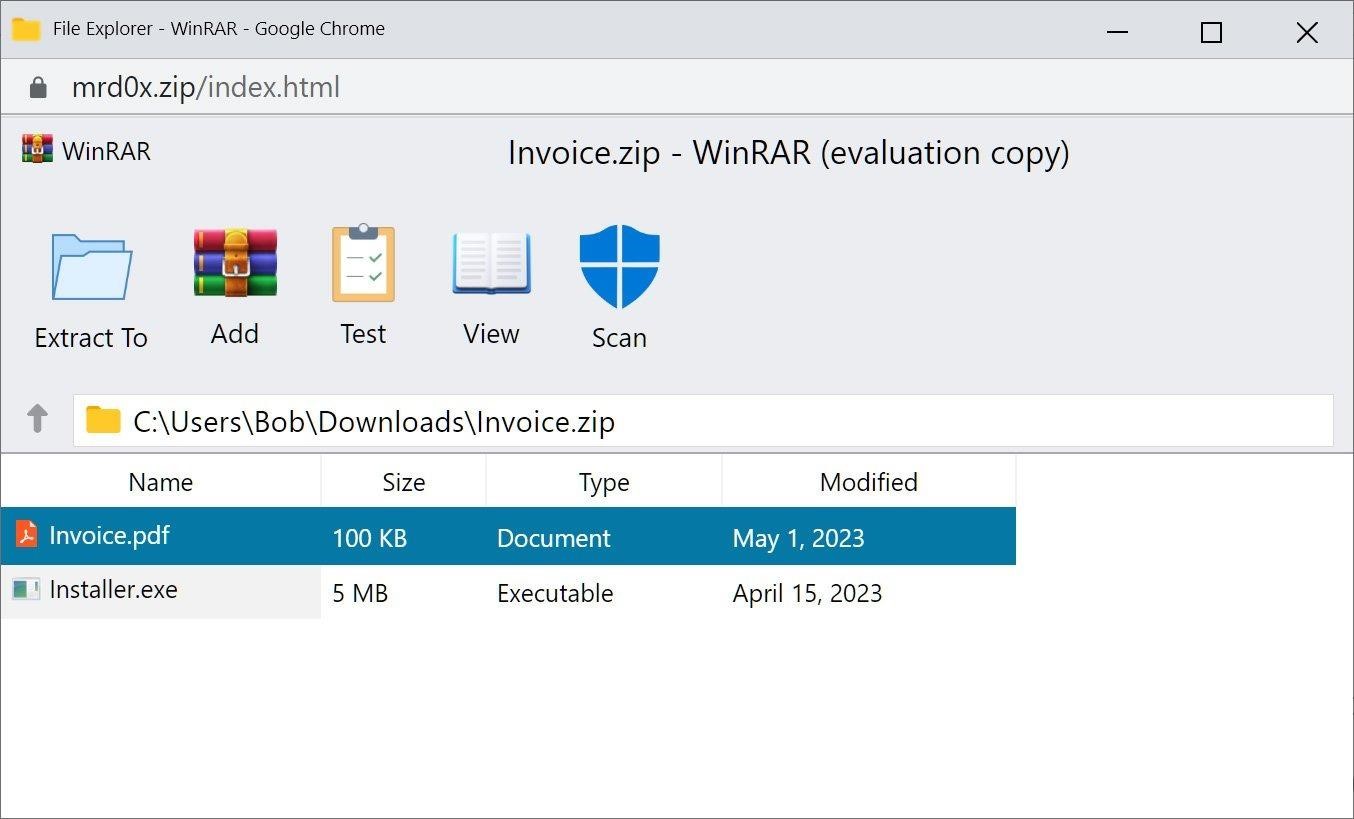
To make the fake archiver window more convincing, the expert even built a fake “Security Scan” button into his kit, which, when pressed, reports that the files have been scanned and no threats have been found. While a potential victim can still see the browser’s address bar, such a fake can trick many users into thinking they are interacting with WinRar. Also, CSS and HTML can probably be used to further refine the toolkit. Mr.d0x additionally created another attack that displays a fake File Explorer in the browser, while simulating the opening of a ZIP file. This template is still under development, so some elements are missing from it.
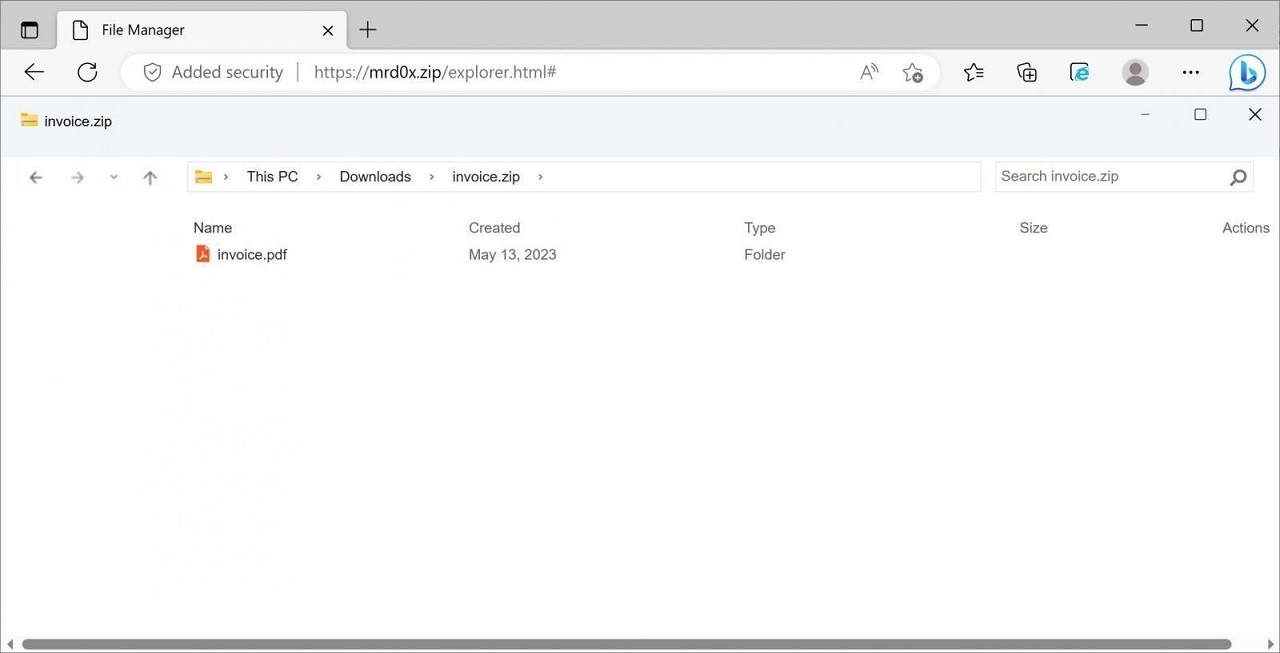
The expert explains that such a phishing kit can be used to both steal credentials and deliver malware. For example, if a user clicks on a “PDF file” in a fake WinRar window, he can be redirected to another page asking for credentials, ostensibly to properly view the file. For malware delivery, the same “PDF” can be displayed, which will download an .exe with the same name. For example, the window of the fake archiver contains the document.pdf file, but when you click on it, document.pdf.exe is loaded (recall that Windows does not show file extensions by default).





