Hackers use a vulnerability in the widely used WooCommerce Payments WordPress plugin to gain privileges of any user, including administrator, on vulnerable sites.
WooCommerce Payments is a popular WordPress plugin that allows websites to accept credit cards as a payment method in WooCommerce stores. According to official statistics, the plugin has over 600,000 active installations.
By the way, we wrote that this plugin was recognized as one of the most vulnerable, and also reported that the Woocommerce store was attacked by web skimmers. Let me also remind you of very fresh attacks on the Elementor Pro plugin.
In March of this year, the developers released an updated version of the plugin (5.6.2), which eliminated the critical vulnerability CVE-2023-28121. The vulnerability affected WooCommerce Payment version 4.8.0 and higher and was fixed in versions 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2 and 5.6.2.
Since the vulnerability allows anyone to impersonate a site administrator and take full control of WordPress, the company behind the development of the CMS, Automattic, forced updates to hundreds of thousands of sites running the popular payment system.
Then the creators of WooCommerce stated that they had no data about attacks on this vulnerability, but information security specialists warned that due to the critical nature of the error, hackers would certainly be interested in it.
Now researchers from RCE Security have analyzed the issue and published a technical report on CVE-2023-28121 on their blog, explaining exactly how the vulnerability can be exploited.
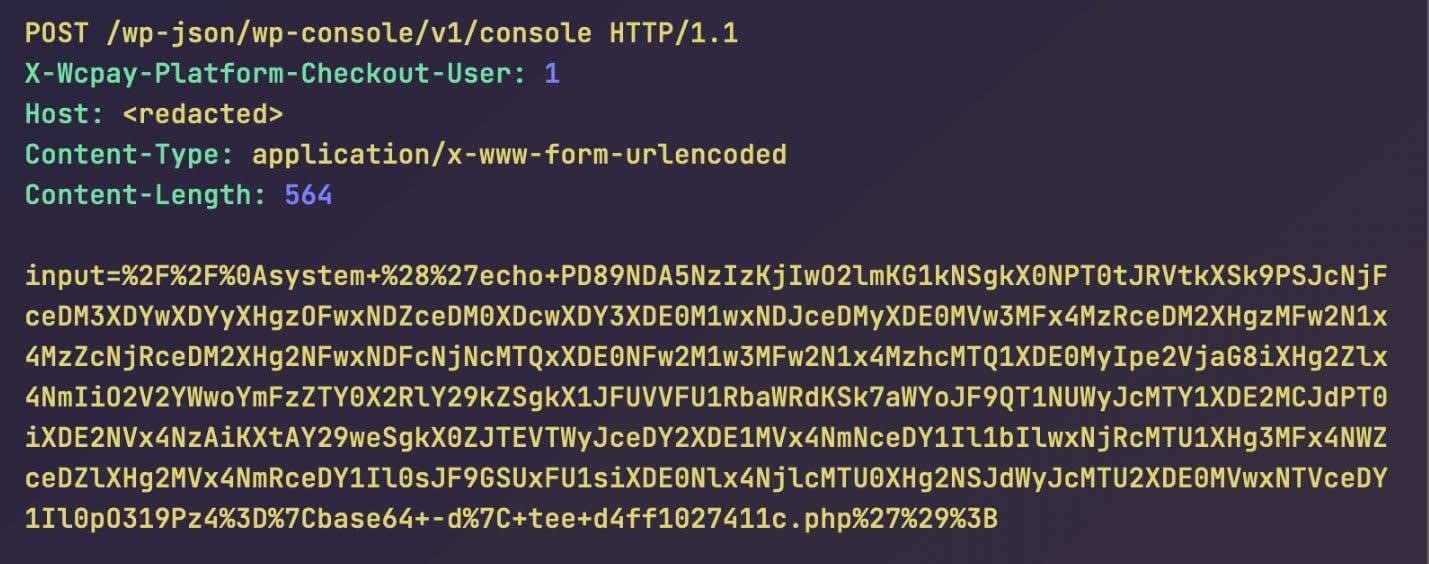
Attackers can simply add X-WCPAY-PLATFORM-CHECKOUT-USER to the request header and set it to the user ID of the account they wish to masquerade as, experts say. Given this header, WooCommerce Payments will treat the request as if it came from the specified ID, including all privileges for that user.
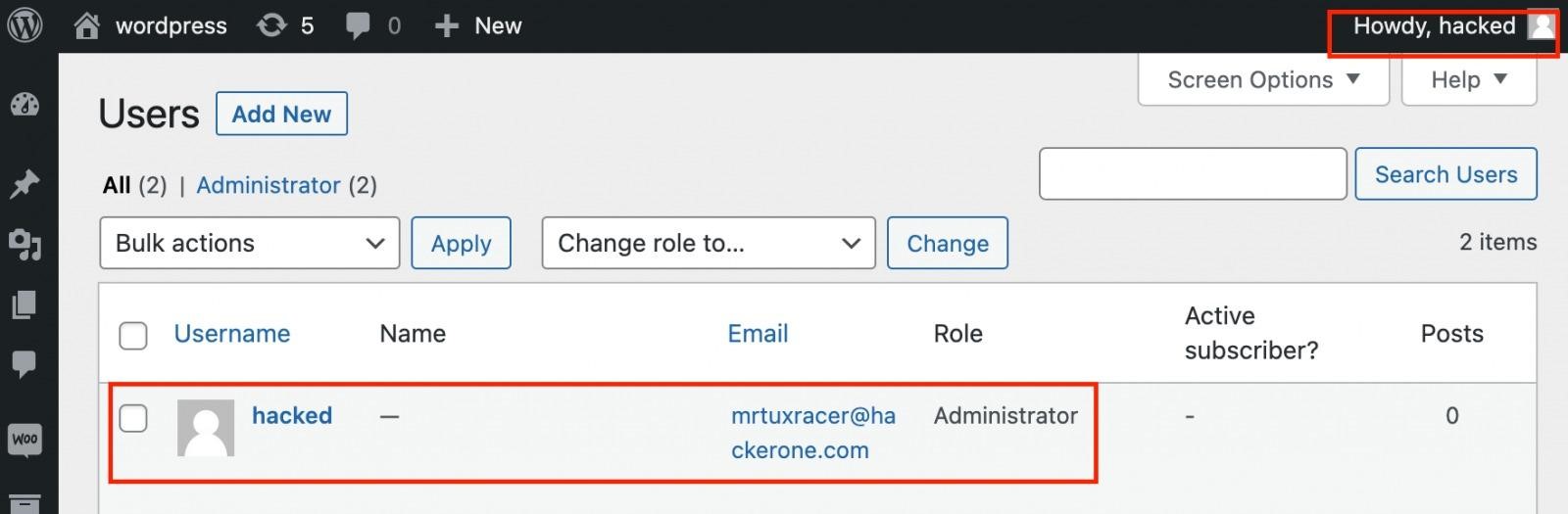
To its analysis, RCE Security attached a PoC exploit that uses a vulnerability to create a new administrator user on vulnerable sites and allows taking full control over the resource.
As a result, WordPress security company Wordfence warned this week that attackers are already exploiting the vulnerability as part of a massive campaign targeting more than 157,000 sites.
According to experts, the attackers use the exploit to install the WP Console plugin on vulnerable sites or create administrator accounts. On systems where the WP Console was installed, the attackers used a plugin to execute PHP code that installed a file uploader on the server and could subsequently be used as a backdoor even after the vulnerability was fixed.
To scan vulnerable WordPress sites, attackers try to access the /wp-content/plugins/woocommerce-payments/readme.txt file and, if it exists, proceed to exploit the vulnerability.
In their report, the researchers shared seven IP addresses from which the attacks are carried out, and especially highlighted the IP address 194.169.175.93, which crawled 213,212 sites.
Site owners are encouraged to update WooCommerce Payment as soon as possible if they haven’t done already, and to check their resources for unusual PHP files and suspicious admin accounts, removing any that can be found.




