Troubleshooting Guides
How to Get Rid of Spam Emails?
Email spam is an annoying and unwanted mailing of many letters. This kind of letter comes from unknown sources and…
How to Remove a Virus From a Computer in Safe Mode
In quite a few cases, you can see advice on using Safe Mode for malware removal. While generally good advice,…
Windows Cannot Access The Specified Device, Path or File Error Fix Guide
Windows Cannot Access The Specified Device, Path or File is a system error that users may encounter while trying to…
Scam Likely Calls: How to block them?
Have you ever glanced at your phone and seen the caller ID flash “Scam Likely”? Understanding what this alert means,…
Windows Defender Security Warning
Have you ever encountered a Windows Defender security warning pop-up while browsing? This type of malicious activity is designed to…
Vmmem High Memory and CPU Usage
Vmmem, short for “Virtual Machine Memory“, is a process that…
What Should You Do When You Get Scammed?
As online scams become not only more widespread, but also…
Phishing With Hacked Sites Becomes a Massive Menace
Threat actors started using compromised websites for phishing purposes much…
Information Security Threats in Social Media
Social media has become an important aspect of our everyday…
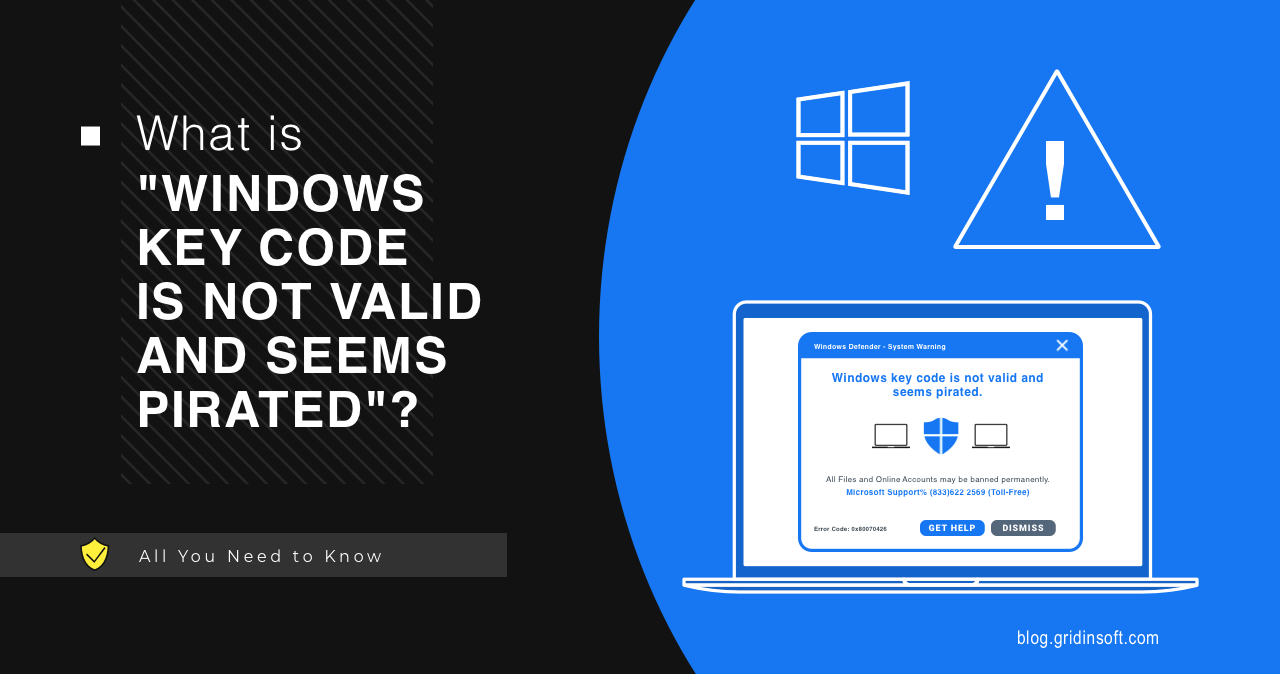
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears…
How to Defeat Insider Threat?
In the current digital world, organizations face more risks than…
5 Signs That You’ve Fallen Victim to a Scam
Internet fraud is becoming increasingly widespread and sophisticated. From simple…
Binance US Ban Scams Incoming: What to Expect?
Recent events around one of the world’s largest cryptocurrency exchanges…
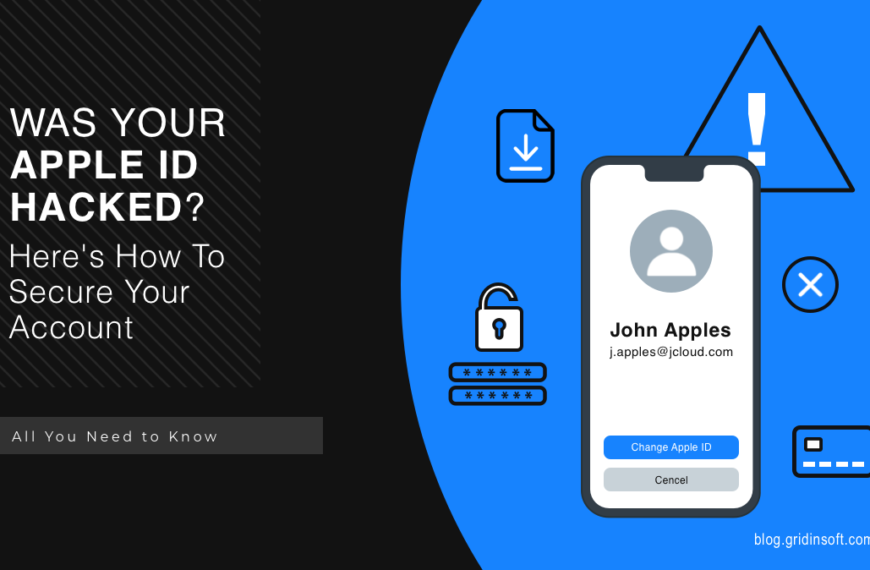
Was Your Apple ID Hacked? Here’s How To Secure Your Account
Apple’s services and products are only accessible through their walled…
Android Malware. Is Malware on Android Phone Possible?
Android malware is a common name for all malicious software…
Spyware Attack: Red Flags You’re Dealing With Spyware
Spyware is probably one of the oldest but most dangerous…
Apple ID Scams: Identify and Prevent Apple Phishing Email
Apple users are believed to be protected from all sorts…