Trojan:Win32/Mamson.A!ac is a type of malware designed to gather data from the system it infects. Sometimes, known spyware families get this detection. The malware is typically distributed disguised as helpful utilities that are downloaded from untrustworthy sources.
Trojan:Win32/Mamson.A!ac Overview
Trojan:Win32/Mamson.A!ac is a Microsoft Defender detection that flags infostealer malware. This type of malicious program aims at collecting data from the infected system. Usually, it gathers login credentials from browser files, cookies, browser history, and other information about the victim’s Internet activity. In some cases, samples of RedLine Stealer appear under this detection. Still, the effect is exactly the same.
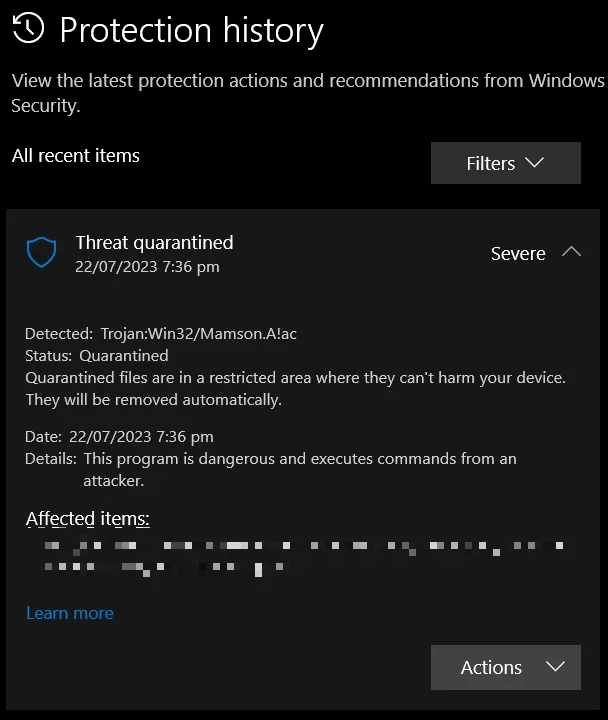
Mamson Trojan often spreads under the guise of helpful utilities downloaded from shady websites, including These places have ideal conditions for malware distribution, as most hacked software requires mandatory disabling of antivirus software during installation. In certain cases, it may hide in the installer.
Technical Analysis
Let’s analyze Trojan:Win32/Mamson.A!ac by tearing down one of its samples. Since this detection is generic, there could be rather wild variations in certain areas, but the “mainstream” functionality remains the same.
Once Mamson enters the system, it checks for the virtual environment, debugging, or sandboxing. For this, It checks the following values in the registry:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft/Windows NT\CurrentVersion\LanguagePack\DataStore_V1.0
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Display
These keys keep info about the OS version, language packs, and display settings. Such data is useful both for fingerprinting and to determine whether the environment has anything synthetic about it.
Privilege Escalation
After the first steps, the malware escalates privileges, which gives it a foothold in the system. To begin with, it manipulates the Windows Error Reporting system to legitimize itself.
%windir%\system32\wbem\wmiprvse.exe
%windir%\System32\svchost.exe -k WerSvcGroup
%windir%\system32\WerFault.exe -u -p 2660 -s 684
Further, it creates its own service, by executing a command to the Service Control Manager. This makes Mamson much harder to remove manually, as services protect its underlying files. Attempting to remove it anyways after such a trick will likely result in BSOD, unless the antimalware software is used.
C:\Windows\system32\sc.exe start w32time task_started
Defence Evasion
To avoid detection, Mamson comes in a packed (encrypted) form that allows it to avoid static detection. In order to legitimize itself, the malware plays with registry keys of Identity Client Runtime Library (IdentityCRL). Some of the values are also used to keep malware configurations.
HKEY_CURRENT_USER\Software\Microsoft\IdentityCRL\Immersive\production\Property\001880060ADF5C62
HKEY_CURRENT_USER\Software\Microsoft\IdentityCRL\Immersive\production\Property\00188006102E98CE
To cover the tracks, this malware also manipulates the logs of Windows Error Reporting system. It edits out lines of the logs that contain the information about the WerFault interactions that I’ve mentioned above.
C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_executable.exe_515752de8867334bf1b5dff986a385cbabdecb_6ccb0f67_0f5f9b13
C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_executable.exe_515752de8867334bf1b5dff986a385cbabdecb_6ccb0f67_0f5f9b13\Report.wer
C:\ProgramData\Microsoft\Windows\WER\Temp\WER1FF4.tmp.dmp
Data Collection
Mamson infostealer has primary goal is to collect sensitive information. Upon finishing preparations, the malware starts with creating a folder at C:\Users\[USER]/Downloads\cp and copying data from C:\Users\[USER]\AppData\Google\Chrome\User Data\Default\Login Data. That folder keeps a wide range of information about user’s credentials and session tokens. It also collects the following data:
C:\Windows\ServiceProfiles\LocalService\AppData\Roaming\Microsoft\Crypto\Keys\de7cf8a7901d2ad13e5c67c29e5d1662_cbbb49d6-b7ff-44ca-aba5-8a5e250d4d42
C:\Windows\System32\Microsoft\Protect\S-1-5-18\User\c74ecc55-989d-484d-a8fe-47bdfda57159
C:\Windows/System32\spp/store\2.0\cache\cache.dat.
Additionally, Mamson accesses cryptocurrency apps and wallets in order to harvest credentials. I did not have a spare crypto wallet to sacrifice for the test, so there were no corresponding logs. Once the data collection is complete, the malware sends it to one of the command servers. Their IP addresses are built into the malware sample:
23.216.147.76:443
23.216.147.64:443
104.86.182.8:443
How To Remove Trojan:Win32/Mamson.A!ac?
To remove Trojan:Win32/Mamson.A!ac you will need a scan with GridinSoft Anti-Malware. Since the malware primarily targets Windows’ built-in defenses, they may be disabled or not working correctly. With GridinSoft Anti-Malware, you will be sure that the malware is completely gone. Run a Full scan to check the entire system and remove even the most covert threats.