Tips & Tricks
Moscovium Ransomware
Moscovium ransomware is a malicious program that locks files on a victim’s computer by encrypting them, then demands a ransom,…
Behavior:Win32/Rugmigen.B
Behavior:Win32/Rugmigen.B – Complete Detection and Removal Guide Behavior:Win32/Rugmigen.B Summary Threat Name Behavior:Win32/Rugmigen.B Type Behavioral Detection (Trojan Downloader/Infostealer) Detection Method Heuristic…
Trojan:Win32/SmokeLoader: Complete Detection & Removal Guide 2025
Trojan:Win32/SmokeLoader is a sophisticated backdoor malware that has remained active in the threat landscape since 2011. It primarily functions as…
Trojan:Win64/RustyStealer.DSK!MTB
Trojan:Win64/RustyStealer.DSK!MTB is a sophisticated malware designed to infiltrate 64-bit Windows systems, primarily focusing on stealing sensitive information such as login…
Microsoft Account Locked
The “Microsoft Account Locked” scam is a deceptive tech support fraud. Users receive pop-up messages falsely claiming their Microsoft account…
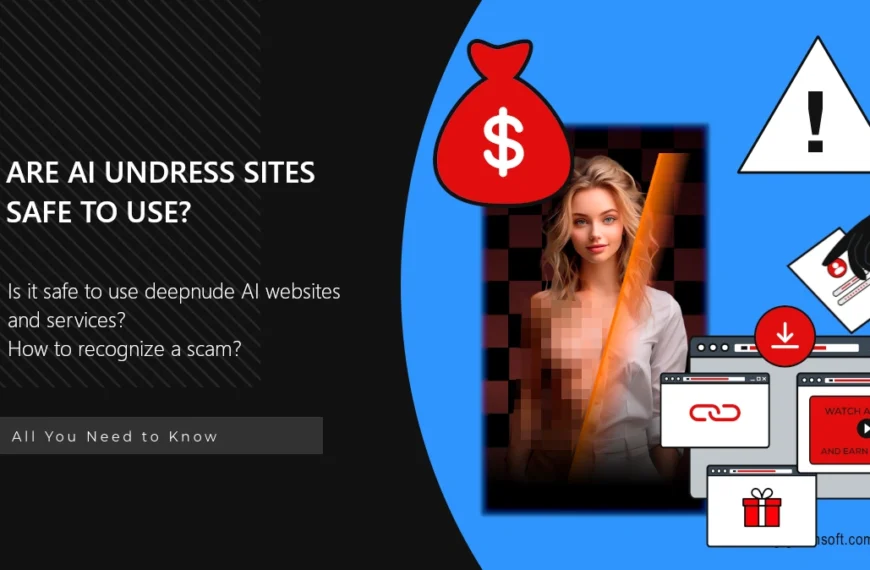
AI Deepnude Websites – Are they Safe & Trustworthy?
The development of generative AI that is capable of creating…
AlienWare Ransomware
AlienWare is a type of ransomware designed to lock your…
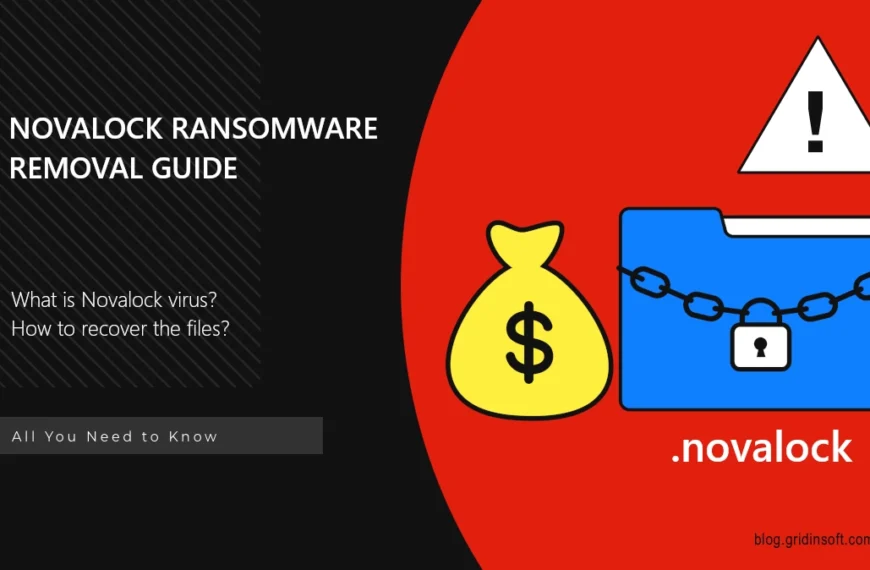
Novalock Ransomware
Novalock is a sophisticated form of malware designed to encrypt…
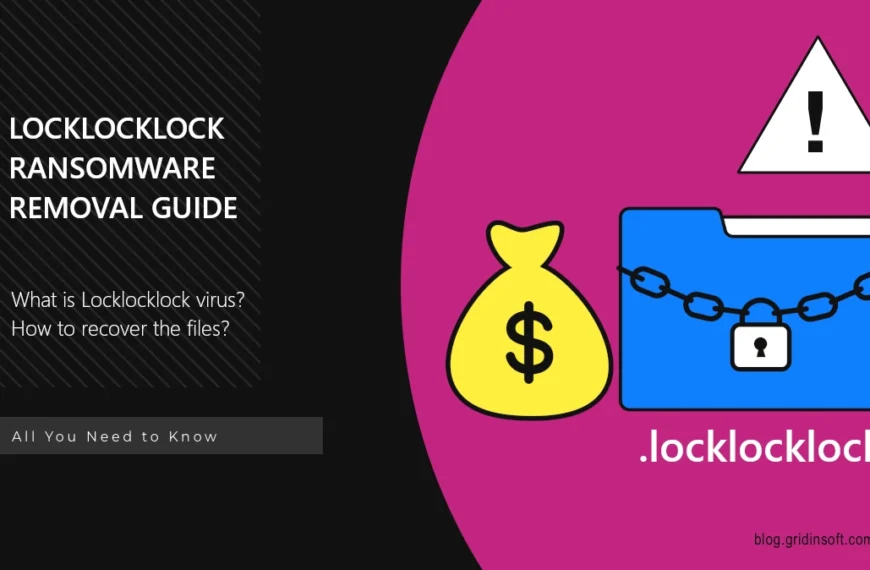
Locklocklock Ransomware
Locklocklock is a ransomware virus designed to lock your files…
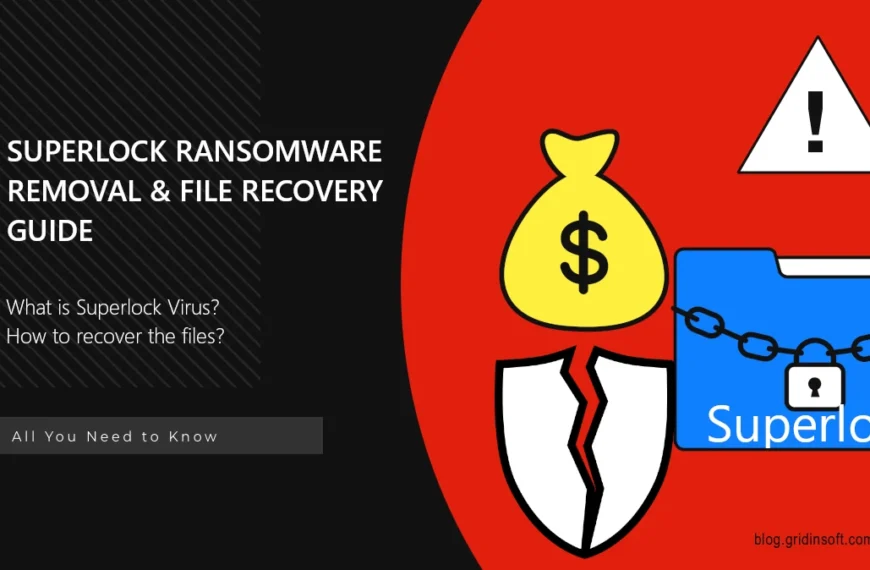
SUPERLOCK Ransomware Virus Simple Step-by-Step Removal Guide
SUPERLOCK is a ransomware infection that aims at blocking access…
Shougnoboassi.net Redirect Virus
Shougnoboassi.net is a website that you may notice appearing in…
Top 3 MMS Scams: What Threats Can Messages Bring
MMS is a rather old technology that is being pushed…
Top 4 Signal Scams to be Aware About
Anonymous messaging app Signal becomes increasingly popular amongst regular users.…
NodePay Claims Scam
“NodePay Claims” is a selection of websites that impersonate NodePay,…
Ledger Recovery Phrase Verification Scam
“Ledger Recovery Phrase Verification” is a scam email that targets…
Meta Security Email Phishing Scams Explained
Attackers are targeting users of Meta services with phishing attacks.…
Opera GX
Opera GX is a special version of the Opera browser…