Tips & Tricks
Shougnoboassi.net Redirect Virus
Shougnoboassi.net is a website that you may notice appearing in your web browser. It shows a human verification button, and…
Top 3 MMS Scams: What Threats Can Messages Bring
MMS is a rather old technology that is being pushed out of the market by proper messenger applications. Nonetheless, fraudsters…
Top 4 Signal Scams to be Aware About
Anonymous messaging app Signal becomes increasingly popular amongst regular users. Such a shift turned the attention of various cybercriminals to…
NodePay Claims Scam
“NodePay Claims” is a selection of websites that impersonate NodePay, a legit AI training platform. These sites offer sharing their…
Ledger Recovery Phrase Verification Scam
“Ledger Recovery Phrase Verification” is a scam email that targets non-vigilant users. Its goal is to trick users into writing…
11 Signs If Your Computer Has A Virus
Something seems off with your device, and you have a…
Top Amazon Scams to Avoid
Because of its reliability, Amazon is a popular choice for…
Facebook Fraud: Other Dangerous Facebook Scams
Facebook is probably one of the most popular platforms for…
Scareware: How to Identify, Prevent and Remove It
Scareware is a widespread Internet fraud scheme that intimidates victims…
Paypal Scams: Most Dangerous Examples
PayPal has a reputation for being a safe and easy…
Top 10 Cash App Scams
Protect yourself from Cash App scams by knowing how to…
Top 12 Instagram Scams in 2024
Nowadays, it’s hard to find someone who has not heard…
Instagram Scams: What You Need to Know
Instagram, one of the world’s most popular social media platforms,…
Microsoft Email Scam
Hackers are constantly finding new ways to infect your computer…
How To Make Google Chrome Faster 2024
Have you ever noticed Google Chrome running much slower than…
Google Tricks For Better Searching
Google is an iconic search engine. You use it every…
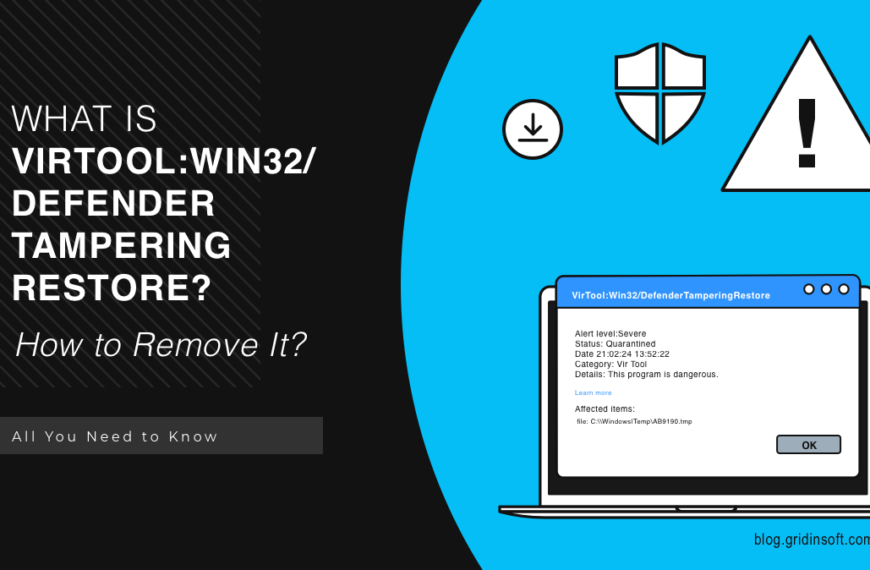
VirTool:Win32/DefenderTamperingRestore
VirTool:Win32/DefenderTamperingRestore is the name of the Microsoft Defender detection of…