Beyond Validation: Announcing the Gridinsoft Email Security Checker Upgrade
In an era where phishing attacks are becoming increasingly sophisticated, simply knowing…
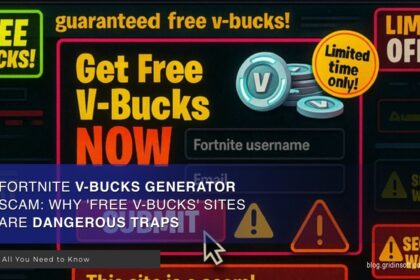
Fortnite V-Bucks Generator Scam: Why ‘Free V-Bucks’ Sites Are Dangerous
When you see a website promising free Fortnite V-Bucks, you're looking at…
“Someone Entered Correct Password For Your Account” Email Scam
"Someone Entered Correct Password For Your Account" is a wave of scam…
Bank Details Email Scam
“Bank Details” is yet another scam campaign targeting not-so-savvy internet users. In…
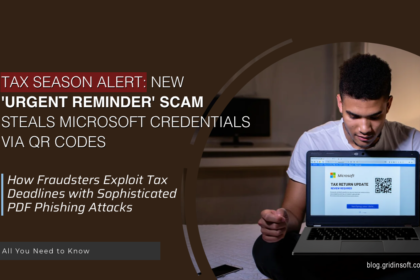
Urgent Reminder Tax Scam
The "Urgent reminder" tax scam is a yearly phishing effort designed to…
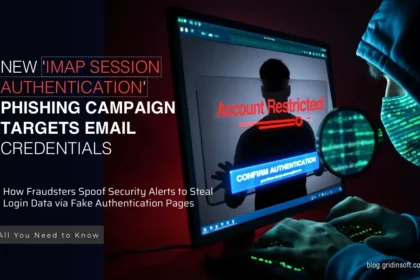
Server (IMAP) Session Authentication Email Scam
The "Server (IMAP) Session Authentication" email scam is a type of phishing…
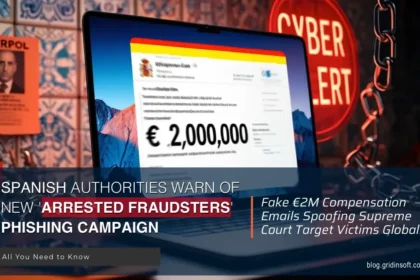
Internet Fraudsters Arrested Email Scam
The "Internet Fraudsters Arrested" email campaign is a phishing attack where cybercriminals…
Chase – Transfer Is Processing And Will Be Deducted
The "Chase - Transfer Is Processing And Will Be Deducted" email scam…
Steganography Attack
Researchers have discovered a non-obvious tactic in which attackers use steganography. While…
Phishing Links in Browser
Phishing links may lurk wherever you go on the Internet: in your…
Fake CAPTCHA Abuses PDF and SEO Poisoning
Cybercrime actors misuse search ads to distribute fraudulent PDF files, that lead…
Fake Google Chrome Downloading Sites Distribute ValleyRAT
Cybercriminals have set up fake websites mimicking Google Chrome’s official download page…