The Security Blog From Gridinsoft
KimWolf Botnet Hijacks 1.8M Android TVs for Massive DDoS Attacks
If your cheap Android TV box feels slower than usual, it might be busy launching DDoS attacks for someone else.…
AI-Generated Fake IDs Are Getting Real – How to Detect and Defend
Fraud teams have been passing around the same kind of screenshot lately: a passport-style fake ID produced by an AI…
Google Patches Chrome Zero-Day Under Active Attack — Update Now
Google dropped an urgent Chrome update on Wednesday to fix a high-severity vulnerability that’s already being exploited in the wild.…
AI Chats Are Delivering AMOS Stealer Through Google Search Results
Here’s a novel malware delivery vector that nobody saw coming. Attackers are weaponizing publicly shared conversations with AI assistants like…
The Hunter Becomes the Hunted: North Korean Hacker Infected by LummaC2, Exposing Bybit Heist Secrets
In a twist of irony that cybersecurity researchers dream about, a North Korean state-sponsored hacker has been infected by the…
The Hunter Becomes the Hunted: North Korean Hacker Infected by LummaC2, Exposing Bybit Heist Secrets
In a twist of irony that cybersecurity researchers dream about,…
React2Shell Exploitation Goes Live: Chinese APT Groups Strike
Predictably, the exploits are rolling in. Within hours of CVE-2025-55182…
React2Shell: Hot December for React and Next.js as Critical 10.0 CVSS Vulnerability Hits RSC
CVE-2025-55182 dropped yesterday evening, and predictably, everyone’s losing their minds.…
SmartTube YouTube Client Hacked: Your Ad-Free TV App Just Became a Botnet
Using SmartTube on your Android TV to escape YouTube’s aggressive…
Cryptomixer’s €1.3 Billion Laundromat Just Got Washed Out (With Cinematic Flair)
Somewhere in Zurich last week, law enforcement seized Cryptomixer, a…
Roblox Warning: Blox Green/Blue/Pink Free Robux Generators Are Fake
If you’ve been playing Roblox lately and noticed a sudden…
Media Land Sanctioned: US, UK, and Australia Crush Russian “Bulletproof” Hosting Empire
November 20, 2025 — In a rare display of international…
Chinese Hackers Used Claude AI to Automate 90% of Cyber Espionage Campaign
Chinese cyber spies automated 90% of their attack campaign using…
ClickFix Gets Creative: Abusing a 1971 Protocol to Deliver Malware
ClickFix is so widespread these days that you can find…
The Chronicles of ClickFix: 2025’s Biggest Hit Keeps Evolving
Meet ClickFix, the social engineering attack that’s become the cybercriminal’s…
PROMPTFLUX: AI Malware Using Gemini for Self-Modification
Malware that rewrites itself on the fly, like a shape-shifting…
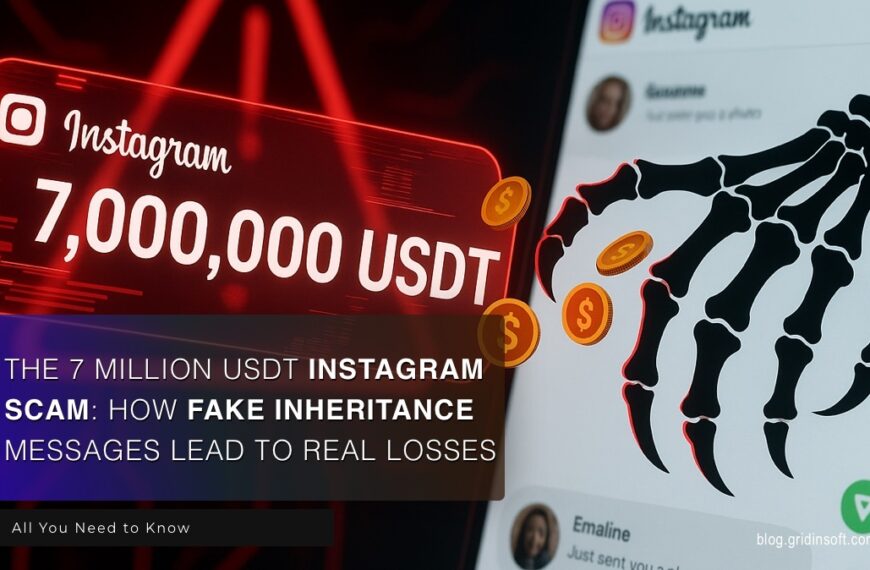
The 7 Million USDT Instagram Scam: How Fake Inheritance Messages Lead to Real Losses
Picture this: You’re scrolling through Instagram when a message pops…